As data volumes explode and the costs of ingesting, processing, and storing them rise, many security teams are finding that their legacy SIEMs no longer scale or justify the spend. But anyone who’s ever been through a SIEM migration knows it’s rarely simple. Reconfiguring agents, re-indexing logs, and maintaining coverage during the transition can be risky and time-consuming. A single missed data source or broken parser can create blind spots that undermine visibility and compliance.
This guide walks through how to plan and execute a SIEM migration with minimal disruption — from auditing your current environment to validating the new one. Along the way, we’ll also show how easily these steps can be implemented with Edge Delta. By following this structured approach, you can minimize downtime and control costs while ensuring that your organization remains secure.
Automate workflows across SRE, DevOps, and Security
Edge Delta's AI Teammates is the only platform where telemetry data, observability, and AI form a self-improving iterative loop. It only takes a few minutes to get started.
Learn MorePlan, Audit, and Map Your Data
Before migrating your SIEM, clarify your goals — whether reducing costs, improving performance, meeting compliance, or gaining modern analytics — and define measurable success metrics. For instance, you might aim to cut ingestion costs by 30%, reduce alert latency to under one minute, or simplify maintenance by consolidating log sources into a single pipeline.
Next, audit your environment by mapping all log sources, ingestion paths, and downstream consumers, and document your normalization and parsing rules. Start by listing every source feeding your current SIEM, such as application logs, firewalls, load balancers, cloud audit trails, and endpoint telemetry data. Then, trace how data flows from each source into your collection agents and onto your SIEM. This helps identify redundant or orphaned data streams that can inflate costs.
Be sure to capture the configuration details for each source, including log formats, enrichment steps, and filtering rules. For example, note whether web server logs are being parsed into JSON, or if firewall events use a custom field mapping. Similarly, record the normalization logic — such as timestamp alignment or field naming conventions — so that it can be replicated or improved in the new system.
It’s also important to map all downstream consumers of the data, such as dashboards, alerting pipelines, and compliance exports. This ensures that every dependent workflow stays functional during migration and that you can verify data parity between the old and new SIEM environments.
Finally, ensure your new platform can handle existing data formats, volumes, and enrichment logic, and maintain consistency in fields, timestamps, and taxonomies to preserve correlation accuracy. For example, if your current SIEM parses failed login events into username, IP address, and failure_reason, missing or misaligned fields in the new system could break alerts and dashboards. Planning and standardizing data flows upfront ensures critical visibility is preserved and your migration achieves its objectives.
Run a Parallel Pipeline
Migrating to a new SIEM without a parallel pipeline is risky because it leaves you blind to data gaps, broken parsers, or misconfigured alerts until after the cutover. These blind spots can translate into real impact — from lost audit trails and failed detection rules to false positives that overwhelm analysts when visibility matters most.
Running pipelines in parallel allows you to spot issues early, fine-tune the new system, and gradually ramp up traffic. Once confidence is high, you can gradually increase traffic until the new system is fully operational.
For example, say a mid-sized security team is trying to migrate to a new SIEM. If they cut over all traffic at once without running a parallel pipeline, they might quickly discover that alerts for failed logins are firing inconsistently, dashboards are missing key fields, and retention policies aren’t applied correctly. But if they mirror a subset of traffic in a parallel pipeline first, they can compare metrics side by side (e.g., event volume, field mappings, latency, and alert parity) between the old and new systems — and confirm that retention policies, dashboards, and compliance outputs match their expectations.
Communicate and Roll Out in Phases
Successful SIEM migrations depend on cross-team coordination, especially between security, compliance, and operations teams. Without alignment on timelines, testing, and validation criteria, critical details can fall through the cracks. Even small configuration issues can ripple into major visibility gaps, eroding trust.
That’s why it’s essential to coordinate early and roll out changes in deliberate, manageable stages. Start with non-critical sources, validate field mappings and timestamps, and address issues before expanding to production data. For example, if a team first migrated a low-volume set of log sources and identified that timestamp formats weren’t aligning correctly, they could fix the problem before continuing the rollout, preventing downstream alerts and dashboards from breaking.
Validate, Tune, and Decommission
With the new SIEM in place, the focus shifts to validation and tuning. Teams should confirm that every critical workflow, such as threat detection, compliance reporting, and user activity monitoring functions as intended. This might include checking that correlation rules trigger or that enrichment fields are properly populated. If detection coverage falls short of baseline performance, refining parsing logic or adjusting alert thresholds can quickly close the gap.
A stable operating period signals that it’s time to retire the legacy system. Before decommissioning, teams typically archive historical data to satisfy compliance requirements or retain it for long-term threat analysis. Documenting key lessons from the migration, such as which parsing configurations worked best or which integrations caused friction, helps streamline future transitions and ensures that hard-earned insights aren’t lost.
How Edge Delta Simplifies SIEM Migrations
While this process can be complex, Edge Delta’s Telemetry Pipelines make it far easier. Edge Delta lets you route data to multiple SIEMs at once — without any manual agent reconfiguration. You can test, compare, and migrate in minutes through a graphical interface, ensuring zero downtime and complete visibility throughout the transition.
Imagine you have a pipeline sending data from an HTTP source through a JSON parser and a metric extraction parser into Edge Delta. As your infrastructure expands, your security team begins evaluating Splunk as a central SIEM to unify visibility across cloud and on-prem environments. Using Edge Delta, they can route a subset of logs to Splunk while maintaining full visibility in their existing pipelines — testing cost, latency, and alert fidelity before committing to a full migration.
Step 1: Add a Splunk Destination – Within Edge Delta’s graphical interface, configure a new output to the Splunk SIEM without touching the original agent or disrupting live traffic.
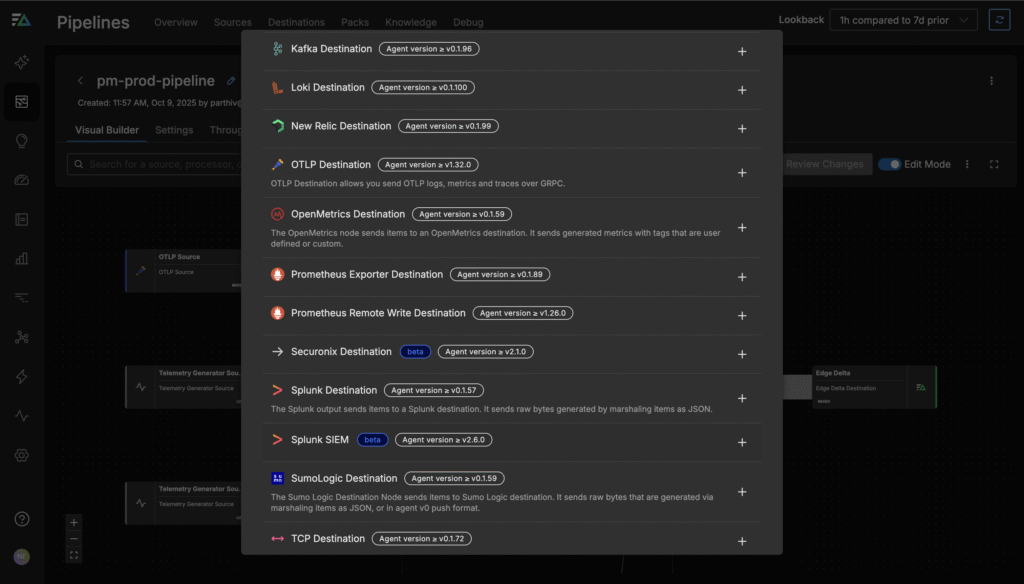
Step 2: Connect the New Destination – Once you’ve connected to the Splunk SIEM destination, your existing source can now send logs there while continuing to send logs to Edge Delta as usual, with all parsing and normalization intact.
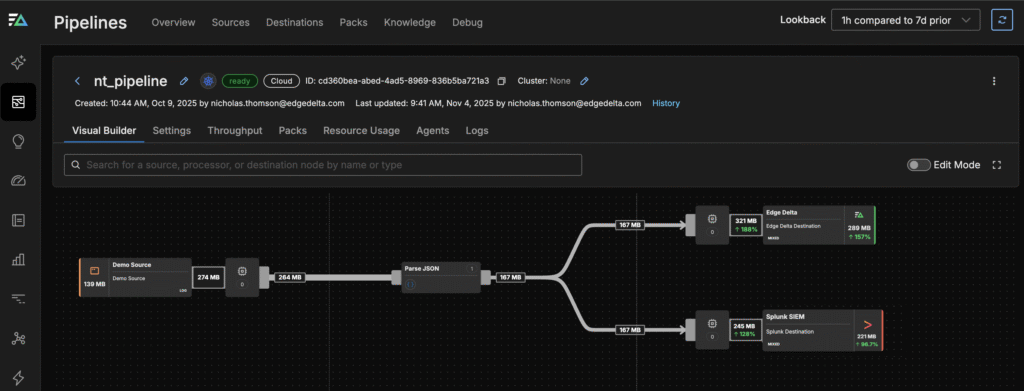
Step 3: Test and Compare – Route a subset of data to the Splunk SIEM while keeping the primary pipeline live. Compare incoming metrics across both destinations to confirm consistent fields, timestamps, and event counts before making the switch.
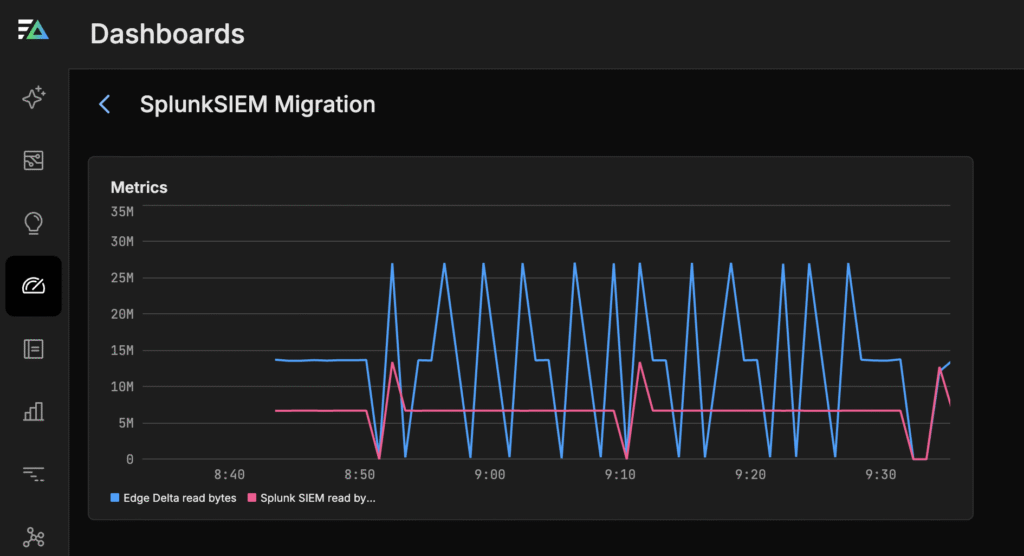
Step 4: Cut Over Gradually – Once validated, increase traffic to the new SIEM endpoint, ensuring zero downtime and full visibility throughout the migration.
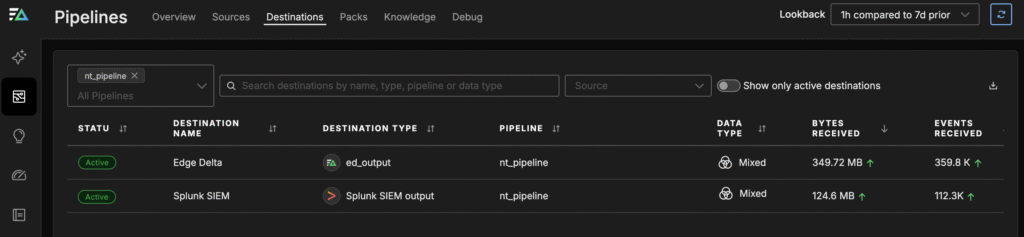
Because Edge Delta pre-processes and optimizes data before it reaches your SIEM, this approach reduces ingestion costs and improves performance. Whether moving to Splunk, Sentinel, or an open-source alternative, Edge Delta provides you a flexible, unified foundation.
Conclusion
SIEM migrations don’t have to be complicated. With the right structure and tooling, you can transition smoothly and maintain full visibility from start to finish. The key is to separate data collection from analytics, giving you the freedom to evolve your security stack without being tied to one vendor.
Ready to start your next migration? Explore how Edge Delta’s Telemetry Pipelines make it easy to test and transition between SIEMs by visiting our free, interactive Playground environment, or book a demo with a technical expert.