Analyzing Office 365 and Azure logs is crucial for understanding user actions, resolving issues, and maintaining security and compliance.
To enhance this process, the Edge Delta Microsoft Activity Pack processes API logs from Office 365 activity and Azure events, and returns sharper and more impactful insights for stronger visibility and protection against threats.
Automate workflows across SRE, DevOps, and Security
Edge Delta's AI Teammates is the only platform where telemetry data, observability, and AI form a self-improving iterative loop. It only takes a few minutes to get started.
Learn MoreWhat is the Microsoft Activity Pack and How Does It Work?
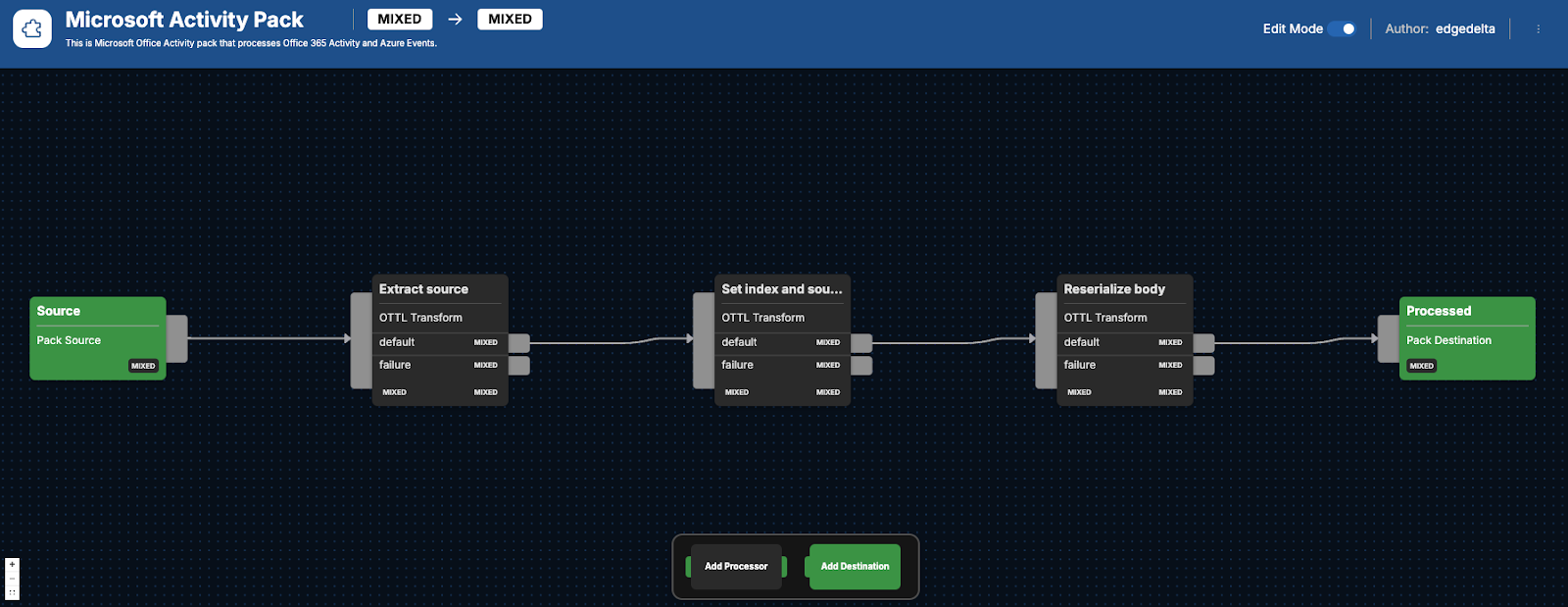
Designed for use with Edge Delta’s Security Data Pipelines, this pack contains three processors specifically designed to parse, optimize, and transform your Microsoft data. Afterwards, the improved logs can be shipped to any security platform for deeper analysis and/or to archival storage for later retrieval.
Below we’ll walk through each processing step within the Microsoft Activity Pack, and what to expect once it’s up and running.
Processing Pathway: Source Extraction
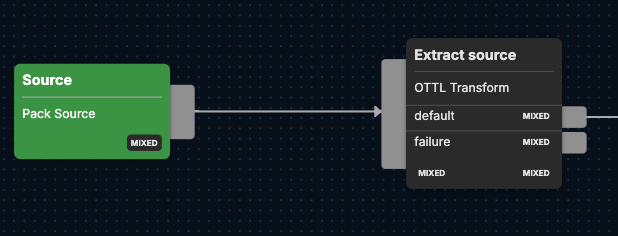
After Microsoft logs begin flowing in the Edge Delta {Source} node, they get pushed into the Extract source node. Within this OpenTelemetry Transform Language (OTTL) node, each log’s source is then extracted from the log body via a regex command to help expedite downstream analysis.
More specifically, the process for ascribing a new identifier to the log source involves pulling in part of the collector’s name — found by applying the $(?<source_collector>audit_[^$]*)$ regex pattern to the log body — and linking it to the end of the “o365:api” string.
- name: Extract source
type: ottl_transform
statements: |-
set(attributes["audit"], ExtractPatterns(Decode(body, "utf-8"), "$(?<source_collector>audit_[^$]*)$"))
set(attributes["source"], Concat(["o365:api", attributes["audit"]["source_collector"]], ":")) where attributes["audit"]["source_collector"] != nil
delete_key(attributes, "audit")
Processing Pathway: Set Index and Sourcetype
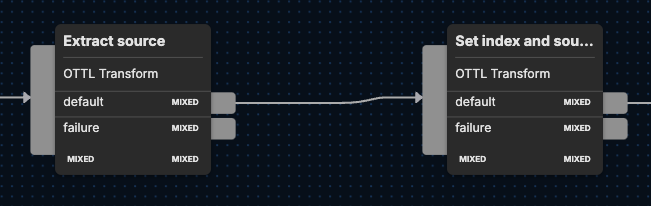
Next, the Set index and sourcetype node focuses on efficiency via log categorization. Through utilization of OTTL’s set function, the node assigns the string value "o365" to the attribute attributes["index"]. As part of this process, the node makes use of two other functions:Concat – links strings togetherConvertCase – changes the case of a string
In this case, the ConvertCase function is applied to resource["service.name"], converting its value to lowercase by specifying “lower” as the case type. Then, the Concat function joins two strings: “o365:activity” and the result of the ConvertCase function.
Finally, the set function assigns the concatenated result to attributes["sourcetype"]. The end result creates a consistent index and sourcetype attributes to improve log classification.
- name: Set index and sourcetype
type: ottl_transform
statements: |-
set(attributes["index"], "o365")
set(attributes["sourcetype"], Concat(["o365:activity", ConvertCase(resource["service.name"], "lower")], ":"))
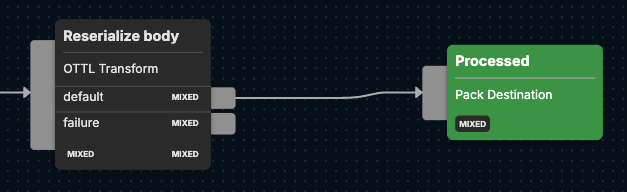
Processing Pathway: Reserialize Body
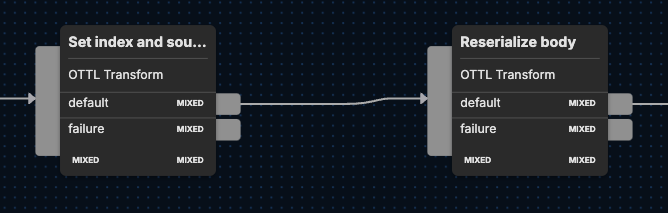
Next, the {Reserialize body} node parses the Microsoft logs into a more structured format while removing any extraneous elements, so only the most essential information moves forward in the pipeline. Here’s how that happens through four separate, sequential functions:set — the first of two set statements, this one decodes the body from a byte array to a UTF-8 encoded string and parses the decoded string into a JSON object, which is assigned to attributes["parsed_body"].
edx_delete_empty_values — deletes keys from the aforementioned attributes["parsed_body"] if the values are empty strings or nulls, which effectively removes any superfluous values from the parsed JSON object.
set — this second set statement uses the EDXEncode custom function to convert attributes["parsed_body"] back into a byte array encoded as UTF-8, leaving the body field with the newly-encoded data.
delete_key — eliminates the temporary attributes["parsed_body"] field from attributes after it has been used and encoded back into the body field.
- name: Reserialize body
type: ottl_transform
statements: |-
set(attributes["parsed_body"], ParseJSON(Decode(body, "utf-8")))
edx_delete_empty_values(attributes["parsed_body"], [], [""], ["deleteNull"])
set(body, EDXEncode(attributes["parsed_body"], "utf-8", true))
delete_key(attributes, "parsed_body")
After exiting the Reserialize body node, the Microsoft logs flow to the Processed pack output. From there, logs can be shipped to any SIEM or storage destination. You can also send a full copy of all raw log data to efficient object storage like Amazon S3 for compliance or future review.
Microsoft Activity Pack in Action
To begin using the Microsoft Activity Pack, you’ll first need an existing pipeline in Edge Delta.
For those who haven’t set up a pipeline yet, go to Pipelines, click New Fleet, and choose between Edge Fleet or Cloud Fleet, depending on your hosting environment. Then, follow the setup instructions to complete the configuration.
Once your pipeline is running, open the Pipelines menu, select Knowledge, then navigate to Packs. Scroll down to locate the Microsoft Activity Pack and hit Add Pack. This will relocate the pack to your library, which you can access any time from the Pipelines menu under Packs.
To install the pack into an existing pipeline, return to your Pipelines dashboard, choose the pipeline where you want to apply the Microsoft Activity Pack, enter Edit Mode, and configure it using the Visual Pipelines builder. While in the pipeline’s Edit Mode, click Add Processor, go to Packs, and select the Microsoft Activity Pack.
You’ll then have the option to rename the pack from “Microsoft Activity Pack” to anything you’d prefer instead. Once ready, click Save Changes to apply the pack to your pipeline. Then, head back to the Visual Pipelines builder and drag and drop the initial connection from your Microsoft logs source into the pack.
To finalize the process, you’ll need to add some destinations. Edge Delta Security Data Pipelines allow you to ship your processed Microsoft logs to any SIEM — such as Splunk, Microsoft Sentinel, CrowdStrike Falcon, or others — or storage platform.
Getting Going with the Microsoft Activity Pack
Ready to see Edge Delta’s Microsoft Activity Pack in action? Check out our packs list and add the Microsoft Activity Pack to any running pipeline. New to Edge Delta? Visit our Playground to get a feel for how we can provide a stronger foundation for your security data.








