At 8:47 AM, Emily’s coffee was still warm when the alert hit her queue. A PowerShell execution on the CFO’s laptop ran an encoded command attempting to bypass execution policy at 8:40 AM. Her stomach tightened.
It wasn’t just the alert itself, which was fishy enough, but the timing: end of quarter. Wire transfer approvals were flying left and right, and the whole company was busy and stressed out. The perfect moment when finance executives are distracted and attackers know it.
Want Faster, Safer, More Actionable Root Cause Analysis?
With Edge Delta’s out-of-the-box AI agent for SRE, teams get clearer context on the alerts that matter and more confidence in the overall health and performance of their apps.
Learn MoreEmily pulled up the alert details in her SIEM. The process tree showed that PowerShell spawned directly from Outlook without the normal macro-laced .docx middleman. That meant a possible exploit against Outlook itself. This was highly unusual and a sign of an advanced exploit — possibly a Zero Day in Outlook.
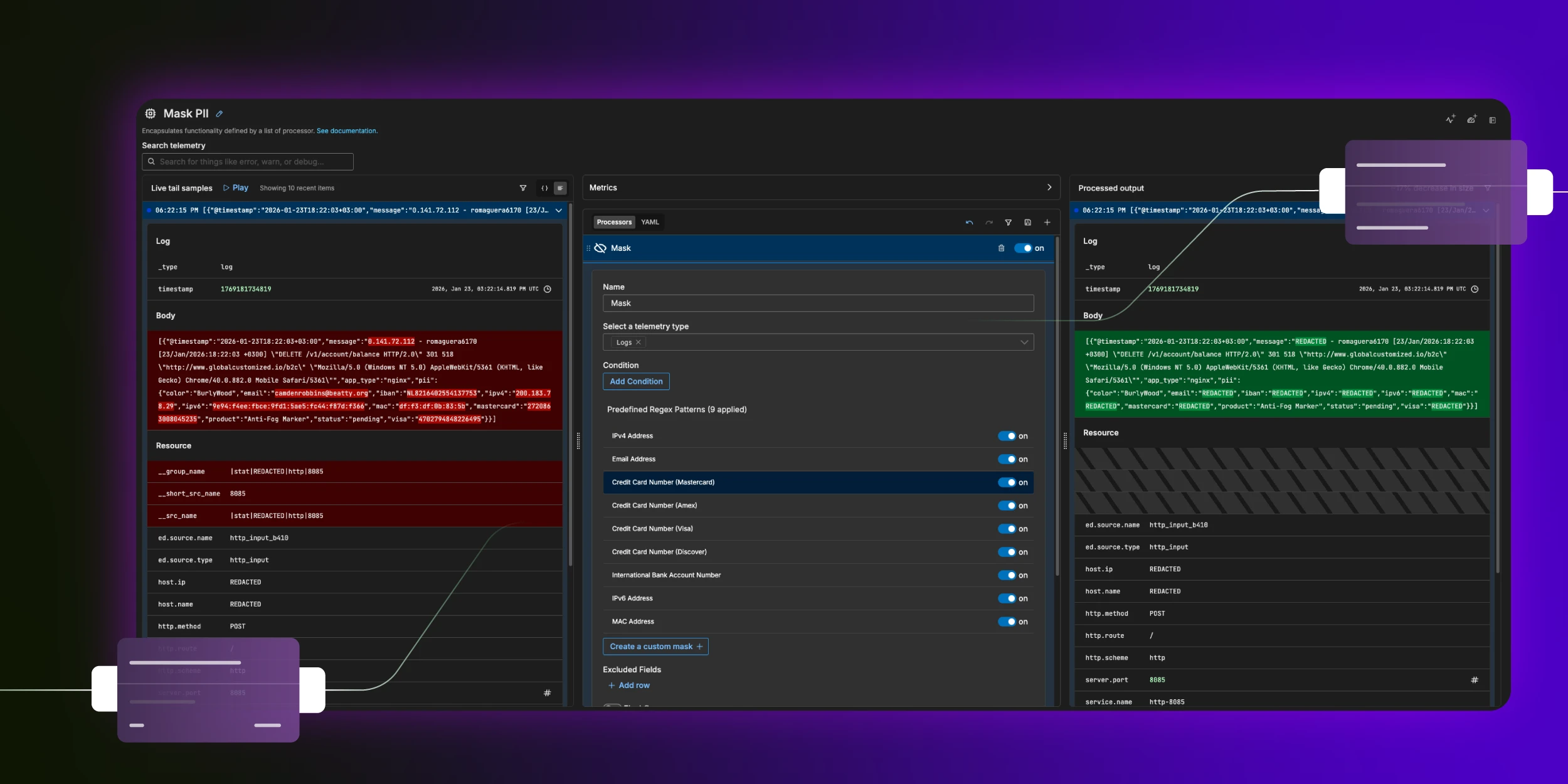
“This isn’t good.” She was already opening new browser tabs for her EDR console, firewall logs, and email gateway. Thankfully, her team had recently onboarded Edge Delta’s Telemetry Pipelines to manage and normalize their log data across most of their security stack — a huge boost that would help her correlate these logs and catch up to the attacker who was already seven minutes ahead.
Emily’s EDR console loaded first. The PowerShell command was base64 encoded — a standard obfuscation technique. She copied it into her scratchpad and ran a macro to decode it. The script was attempting to download a second-stage payload from a compromised WordPress site, then launched into sophisticated persistence mechanisms she needed to analyze further.
The WordPress dropsite was classic living-off-the-land tactics — using a poorly secured and long forgotten blog site to host malware. She knew what to do with that. She copied the compromised WordPress URL and pasted it into their malware analysis sandbox submission form. The automated analysis would take 3-5 minutes if the sandbox wasn’t backlogged with everyone else’s end-of-quarter suspicious files. While that ran, she could check for any other activity.
She switched to the firewall interface, searching for any unusual outbound connections from the CFO’s machine between 8:30 and 8:50 AM. The Palo Alto logs loaded slowly.
She squinted at the timestamp field. Normally, this would have been incredibly confusing, with firewalls logging in Pacific Time while SIEMs normalized to Eastern. But to her relief, most systems now showed timestamps in clean GMT, all synced to the same time server. The team had built timestamp normalization into the Edge Delta pipeline, which was critical here: no more manually subtracting three hours from entries or doing timezone math in her head while tracking a possible breach.
Except… wait. The firewall logs looked different.
The first sweep showed nothing obvious — just the usual Microsoft telemetry, some Salesforce API calls, standard corporate traffic. But the logs had gaps. Several fields that should have contained byte counts just showed null values. The network team hadn’t yet migrated onto Edge Delta, and as a result, nobody had been alerted that they had pushed a configuration change last week that broke some of the logging. Naturally.
Emily pulled up Slack. “Hey @networkteam, I need raw logs from FW-CORP-01 for the last hour. The processed ones are missing transfer sizes.”
Three dots appeared, then disappeared. Then reappeared. Finally: “Those take 15-20 min to hit our collector. Check back at like twenty-past, and be ready for a big file.”
Fifteen to twenty minutes. The attack happened at 8:40. It was now 8:58. By the time she got those logs, any exfiltration could be ancient history. She made a note in her investigation tracker and moved on.
The email gateway had to have something. If PowerShell spawned from Outlook, there was an email involved. She logged into Proofpoint and started hunting. Thanks to Edge Delta’s pre-index filtering, she wasn’t drowning in scanner noise — the pipeline had already separated security appliance chatter from actual email events. The CFO’s inbox for the last 24 hours showed 47 emails. Most were internal threads about quarterly numbers. But there, at 8:33 AM, was an external email from noreply@wellsfargo-secure[.]net.
The domain was wrong — Wells Fargo would never use a hyphenated domain like that. She clicked through to the full headers and message content. The email was a masterpiece of social engineering. Perfect Wells Fargo branding, urgent language about a “pending wire transfer requiring immediate verification,” and a link that had already been clicked at 8:38 AM.
“Okay, we need to isolate this machine, sorry Mr. Smith.” She returned to the EDR console and initiated a quarantine. Then she opened ServiceNow and submitted a task to have the Forensics team grab it for analysis.
Emily began tracing what happened after that click. Edge Delta’s pipeline had already enriched the logs with session tracking, letting her follow the CFO’s actions like breadcrumbs through the system — from email click to process execution, all linked by a common thread. Without that enrichment, she’d be manually correlating events across three different tools. But even with perfect correlation, she hit a snag: the link rewriting function had replaced the original malicious URL with Proofpoint’s safe-link wrapper, which would take precious time to decode.
She needed to understand exactly what the PowerShell script was trying to do. Emily opened a new browser tab and logged into ChatGPT.
“Analyze this PowerShell command,” she typed, pasting the decoded script. Within seconds, the AI broke down the script’s functionality: it was designed to establish persistence via a scheduled task, then beacon out to a command-and-control server every five minutes. Her EDR telemetry confirmed a scheduled task creation attempt, matching what the AI-decoded script described.
The AI analysis was helpful, but it couldn’t tell her if the script had successfully executed or if the endpoint protection had blocked it. For that, she needed to correlate the EDR telemetry (which said the script ran) with the firewall logs to see if any beacon traffic actually made it out. With the in-pipeline timestamp normalization, this should have been a breeze. But those critical firewall logs were still missing.
She flipped back to her investigation. The CFO clicked the malicious link at 8:38. PowerShell executed at 8:40. That two-minute gap mattered. What happened in those two minutes?
At 9:15 AM, the network team’s logs still hadn’t arrived, but something else caught her attention. The AI’s analysis of the malware pointed to sophisticated polymorphic capabilities with anti-analysis countermeasures. This looked like it could mimic legitimate banking portals, capture credentials and two-factor codes, then proxy real login attempts through attacker infrastructure — classic man-in-the-middle tactics routinely used in high-value wire transfer fraud.
She opened a ticket for the Malware Analysis Team. There were a whopping two members and they were permanently swamped. She tagged it highest priority and lobbed them a Slack message: “Target is CFO, execution likely.”
The CFO was probably in meetings, unaware his laptop was compromised. If data was being exfiltrated, it had been happening for 35 minutes already.
The AI could help her analyze what she found, but it couldn’t conjure up data that wasn’t there.
Emily took a sip of her now-cold coffee and prepared to do what SOC analysts always do: build the best timeline possible with incomplete data, and hope it was enough to stop the attack before real damage was done.
At 9:30 AM, Emily’s Slack exploded.
“@security-team URGENT: Wells Fargo just called about a wire request from CFO for $3.2M to a Hong Kong account. CFO says he didn’t initiate. Please advise ASAP” – Finance Controller
Emily’s stomach dropped. This wasn’t theoretical anymore. Real money was in motion.
“Tell them to HOLD THE TRANSFER. CFO’s machine is compromised. DO NOT PROCESS.” She fired back, then immediately called the finance controller.
“The CFO’s laptop has malware. Whatever authorization they think they have is fraudulent. Kill the transfer now.”
While finance scrambled to contact Wells Fargo, Emily attacked her timeline with renewed urgency. Thanks to Edge Delta’s log processing, most of the puzzle pieces were already in place and properly correlated. The malware showed credential theft capability. The CFO had clicked a fake Wells Fargo link at 8:38. PowerShell executed at 8:40. Somewhere in those two minutes, the attack had pivoted from email to active exploitation.
“Think, Emily,” she muttered. The pieces clicked. This wasn’t a normal phishing kit. The email had triggered something in Outlook itself — a vulnerability that let the attacker jump straight from email click to code execution. No document required. That’s why the PowerShell spawned directly from Outlook.exe.
She opened another browser tab and searched for recent Outlook vulnerabilities. There it was — CVE-2025-98785, a security bypass that allowed remote code execution through specially crafted emails. Unpatched on most systems. The security bulletin was only two weeks old.
The attack chain crystallized: Email arrives → CFO clicks link → Triggers Outlook vulnerability → Executes PowerShell → Downloads banking trojan → Captures CFO’s credentials when he thinks he’s checking a routine transfer → Attackers use stolen session to initiate real $3.2M transfer.
Elegant. Devastating. And it would have worked if finance hadn’t called to verify.
Emily’s phone rang. IT support.
“Hey, you asked about logs from the CFO’s machine? Our endpoint agent shows nothing unusual. Maybe a false positive?”
“What’s your retention period?” Emily asked, already knowing the answer would hurt.
“Oh, we keep 24 hours of detailed logs, then just summary data.”
“The attack was 45 minutes ago. Can you check for PowerShell execution around 8:40?”
Keyboard clicks. “Hmm, our agent logs show… nothing. But wait, that’s weird. There’s a gap from 8:35 to 8:45. Like the agent stopped reporting.”
Of course there was a gap. The malware probably suspended the monitoring agent as part of its execution. Another invisible footprint in their already-sparse data.
“Thanks. Can you pull whatever you have and send it over?”
“Sure, but it’s basically nothing for that time window.”
Emily hung up and stared at her screens. The firewall logs finally arrived at 9:42 – too late to help with the immediate threat but confirming her worst suspicions. Multiple connections to known C2 servers starting at 8:41. The beacons were getting out. And these logs were a mess — timestamps in Pacific Time, missing byte counts, no session correlation. She had to manually piece together what should have been obvious patterns.
But they’d stopped the wire transfer. The CFO’s machine was isolated. The attack had failed – barely.
She opened a new ServiceNow ticket for the remediation team, documenting everything she’d found. Then she started her handoff notes for the next shift:
“High-priority incident – CFO targeted with Outlook zero-day (CVE-2025-98785). Attack chain: Phishing email → Outlook RCE → PowerShell → Banking trojan → Attempted $3.2M wire fraud. Machine isolated, transfer blocked.
VISIBILITY GAPS:
- IT endpoint logs have 10-min gap during attack window
- Network team firewall logs arrived 45min delayed (not on Edge Delta pipeline)
- Network logs missing critical fields due to config issues
Watch for similar patterns. Attackers are using fresh Outlook exploit. Finance team on high alert.”
Emily leaned back and rubbed her eyes. Thanks to the network team stalling on pipeline adoption, an attack that should have been obvious in the first five minutes had turned into one extremely intense hour of investigation.
Had the network team’s logs been flowing through Edge Delta like everything else, this investigation would have been radically different. The attack still would have happened — zero-days are gonna zero-day. But she could have spotted the C2 beacons at 8:47 when the alert fired, confirmed the full attack chain by 8:50, and had the CFO’s machine isolated before the banking trojan ever established persistence. Instead of an hour of frantic investigation with a near-miss on $3.2 million, it would have been 15 minutes of guided response.
Emily finished her handoff notes and grabbed her cold coffee. She made sure to flag the network team’s manager about the urgent need to complete their Edge Delta migration. Nobody wanted to be the team whose “we’ll get to it next quarter” almost cost the company $3.2 million.
The security team’s early adoption of telemetry pipelines had given her the visibility to spot and stop the attack. One pipeline gap had nearly undone everything. She opened the network team’s migration ticket and updated the priority to “Critical” with a simple note: “This gap almost cost us $3.2M today.”
The tools existed. The AI capabilities were real and available. Edge Delta had proven its worth everywhere it was deployed. The only vulnerability left was in the spaces between — the teams that hadn’t yet made the jump.
She flagged her ticket for follow-up and headed to the break room for fresh coffee. The CFO’s $3.2 million was safe.
This time.