In network and cloud computing, data egress and ingress are fundamental concepts that describe data movement across network boundaries.
Data egress refers to data flow exiting a system, network, or cloud environment. This process is essential to network operations, particularly in cloud environments where managing data flow is critical for maintaining security and efficiency.
Automate workflows across SRE, DevOps, and Security
Edge Delta's AI Teammates is the only platform where telemetry data, observability, and AI form a self-improving iterative loop. It only takes a few minutes to get started.
Learn MoreIn comparison, data ingress refers to the process of transferring data from an external source, often the public internet, into a private network. In the context of cloud computing, efficiently managing ingress is crucial for ensuring the security and integrity of the network.
Understanding data egress and ingress processes is crucial for managing network security, optimizing performance, and controlling costs. Effective monitoring and management of these data flows are essential to protecting sensitive information and maintaining the integrity of network operations.
This article provides a detailed comparison of data egress vs ingress, including their use cases, applications, and best practices for managing egress and ingress.
| Key Takeaways |
| Data egress is the process of data leaving a network or system, typically to an external location. Effective data egress management is critical to ensuring data security and compliance. Data ingress refers to data entering a network or system from an external source.Strong security measures are essential for protecting data during egress and ingress.Monitoring and auditing data egress and ingress is crucial for data integrity, anomaly detection, and organizational and regulatory compliance.A frequent transfer of large datasets can quickly increase data egress costs. |
Data Egress vs. Ingress: A Full Comparison
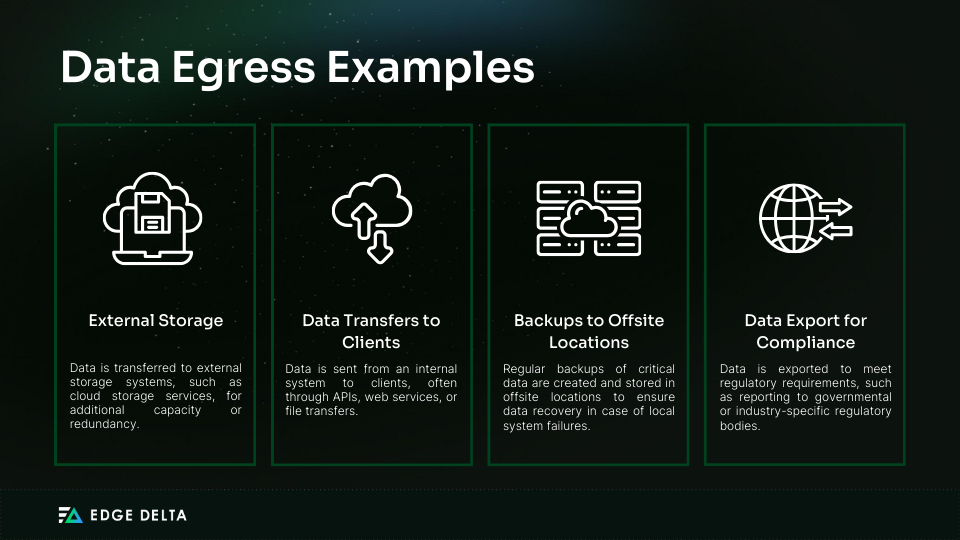
Data egress refers to data exiting a network or system, often to an external location. This process is essential for various business operations and can involve the following:
- Sending data to external storage
- Transferring data to clients or other services
- Creating backups at offsite locations
Managing data egress effectively is crucial for maintaining data security and compliance, as it often involves sensitive or critical information. Here are common examples of data egress scenarios:
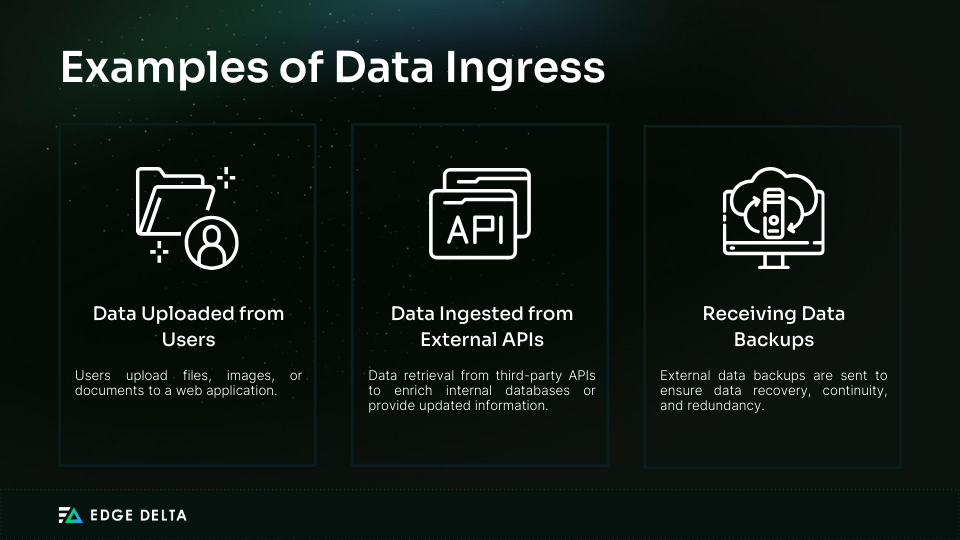
In comparison, data ingress refers to bringing data into a network or system from outside sources. This process involves introducing external data into an organization’s internal systems for processing, storage, or analysis.
Its goal is to ensure that data from various sources can be easily integrated and used within the organization’s digital setup.
While data egress and ingress are complementary processes, they serve different purposes, operate in opposite directions, and have distinct applications. Below is a comparison table highlighting their main differences.
| Aspect | Data Egress | Data Ingress |
| Definition | Data exiting a system or network. | Data entering a system or network. |
| Examples | Exporting data from a cloud service. | Uploading data to a cloud service. |
| Cost Considerations | Often incurs higher costs, especially in cloud services. | Usually less costly, but it depends on the volume and source. |
| Security Concerns | Risk of data leaks, requires robust encryption. | Risk of malicious data entry, requires validation and filtering. |
| Bandwidth Impact | Can saturate outbound bandwidth. | Can saturate inbound bandwidth. |
| Common Use Cases | Data backups, data sharing, and content delivery. | Data collection, data synchronization, and application updates. |
| Regulatory Issues | Compliance with data protection laws for data leaving a region or country. | Ensuring data complies with local regulations upon entry. |
| Monitoring | Tracking data leaving the system for security and usage patterns. | Monitoring data entry points to detect unusual activity. |
Managing data egress and ingress is vital for network security, performance, and cost control. It prevents breaches by detecting unauthorized transfers, optimizes traffic to avoid congestion, and reduces expenses by minimizing data volumes.
For instance, financial institutions monitor egress for security, e-commerce platforms balance peak traffic, and cloud users optimize transfer schedules to save money. Keep reading to learn more about data egress vs ingress in the next section.
Use Cases and Applications of Data Egress and Ingress
Data egress is essential for numerous business processes, from securing critical information in offsite backups to enabling real-time collaboration across different geographic locations. Conversely, data ingress involves seamless data intake from various sources, facilitating tasks such as:
- System updates
- Data consolidation
- Real-time analytics
Read on for detailed use cases of data egress and ingress.
Use Cases of Data Egress
Understanding various data egress use cases can significantly enhance an organization’s data management, security, and operational efficiency. Here are some common scenarios where data egress plays a crucial role:
| Use Case | Description |
| Cloud Storage | Sending data to cloud storage services for backup, archiving, or cloud computing capabilities. |
| External Sharing | Sharing data with external partners, clients, or third-party vendors for collaboration, analysis, or compliance. |
| Offsite Backup | Creating backups at offsite locations for redundancy and disaster recovery. |
| Data Migration | Transferring data from on-premises systems to cloud environments or between different cloud platforms. |
| Data Replication | Replicating data to remote servers or data centers to ensure high availability and reliability. |
| Content Distribution | Distributing data across various edge locations using CDNs for faster and more reliable access. |
| External Processing | Sending data to external analytics or machine learning platforms for processing and analysis. |
| Compliance Reporting | Exporting data to comply with regulatory requirements and reporting to regulatory bodies or external auditors. |
| Collaborative Projects | Using data egress to integrate with collaborative tools, enhances real-time data sharing and team productivity. |
| IoT Data Sharing | Sending data from IoT devices to central cloud sites for processing and analysis. |
- Use Case: Cloud Storage
Sending data to cloud storage services for backup, archiving, or leveraging cloud computing capabilities allows for scalable and cost-effective data storage accessible from anywhere with an internet connection.
Scenario: An organization backs up its critical data to cloud storage to ensure business continuity in case of a system failure. This process allows data recovery from any location with internet access, minimizing downtime.
- Use Case: External Sharing
Sharing data with external partners, clients, or third-party vendors involves exporting data from internal systems to external entities for collaboration, analysis, or regulatory compliance.
Scenario: A company shares anonymized user data with a third-party analytics firm via secure APIs for advanced customer behavior analysis. External sharing enhances the company’s understanding of its user base while ensuring data security.
- Use Case: Offsite Backup
Data egress happens when creating backups at offsite locations for redundancy and disaster recovery. Offsite backups ensure that data is safe and retrievable in case of local data loss due to hardware failure, natural disasters, or cyber-attacks.
Scenario: A healthcare provider maintains offsite backups to protect against ransomware attacks, ensuring quick data recovery and continuity of patient care.
- Use Case: Data Migration
Data migration from on-premises systems to cloud environments or across cloud platforms is essential for upgrading, consolidating, or moving to more advanced or cost-effective data management solutions.
Scenario: A retail business moves its customer database from an on-premises server to a cloud database to leverage cloud-based analytics and machine learning capabilities. Doing so improves customer insights and operational efficiency.
- Use Case: Data Replication
Replicating data to remote servers or data centers ensures high availability and reliability. Data replication can be synchronous or asynchronous and is crucial for maintaining business continuity during a primary site failure.
Scenario: An e-commerce platform uses synchronous data replication between data centers to ensure uninterrupted service during peak shopping seasons. This technique provides a seamless shopping experience for customers.
- Use Case: Content Distribution
Distributing data across various edge locations using CDNs provides faster and more reliable access to data and applications for users around the globe. This distribution benefits media companies, e-commerce platforms, and businesses requiring low-latency content access.
Scenario: A video streaming service uses a CDN to distribute high-definition content to viewers worldwide, ensuring minimal buffering and high-quality playback.
- Use Case: External Processing
Sending data to external analytics or machine learning platforms for processing and analysis allows businesses to leverage advanced analytics tools and machine learning models hosted on specialized platforms to gain insights and make data-driven decisions.
Scenario: A marketing firm exports customer behavior data to a machine learning platform for predictive analytics, helping clients tailor their marketing strategies more effectively.
- Use Case: Compliance Reporting
Exporting data to comply with regulatory requirements (e.g., financial reporting, healthcare data sharing, or data privacy regulations) involves securely transmitting data to regulatory bodies or external auditors to ensure compliance and avoid legal penalties.
Scenario: A hospital system sends patient records to a central database to comply with healthcare data security and privacy regulations.
- Use Case: Collaborative Projects
Using data egress to integrate with collaborative tools like team communication platforms or project management software facilitates real-time data sharing and collaboration among team members, enhancing project productivity and coordination.
Scenario: A software development team shares project updates and files through a team communication platform, streamlining communication and collaboration across different time zones.
- Use Case: IoT Data Sharing
Sending data from IoT devices to centralized cloud platforms for processing and analysis is essential for applications like smart cities, industrial automation, and healthcare monitoring, where real-time data from various sensors and devices needs to be aggregated and analyzed to provide actionable insights.
Scenario: A city government collects data from various IoT sensors (traffic, air quality, and energy usage). It then sends it to a cloud platform for analysis to improve urban planning and resource management.
Use Cases of Data Ingress
Data ingress is a critical aspect of data management, encompassing various scenarios such as user interactions, API calls, and data imports from different sources. Here are various use cases of data ingress to illustrate its importance and versatility:
| Use Case | Description |
| IoT Data Ingestion | Receiving data from IoT devices for processing |
| User Data Uploads | Users uploading files or data to a system |
| API Calls | Sending data to external APIs |
| Database Imports | Importing data from external databases |
| User Requests | User interactions generating data |
| File System Imports | Importing data from file systems |
- Use Case: IoT Data Ingestion
Receiving and processing data from IoT devices enables real-time monitoring, analytics, and proactive interventions. This process is crucial for applications in healthcare, industrial automation, and smart homes, where timely data from sensors can significantly improve efficiency and safety.
Scenario: A healthcare system uses wearable devices to monitor patients’ vital signs, such as heart rate, blood pressure, and activity levels. This data is continuously ingressed into the healthcare provider’s system for real-time monitoring. Physicians can use this data to track patient health remotely and intervene promptly if any irregularities are detected.
- Use Case: User Data Uploads
Facilitating users’ secure and organized uploading of files or data to a centralized system for storage, processing, and access is typical in educational platforms, cloud storage services, and content management systems, where user contributions must be handled systematically.
Scenario: An online education platform allows students to upload assignments and projects. These files are then stored in a central repository, where instructors can access them for grading. This process ensures that all student submissions are securely collected and easily retrievable.
- Use Case: API Calls
Sending and receiving data through external APIs enhances application functionality and provides users with up-to-date information. This use case is essential for integrating third-party services, improving app capabilities, and delivering enriched user experiences.
Scenario: A weather app makes API calls to a weather service provider to fetch current weather data and forecasts. The data retrieved from the API is then displayed to the users in the app interface, providing them with accurate and up-to-date weather information.
- Use Case: Database Imports
Importing data from external databases into a system for comprehensive analysis, reporting, and decision-making is vital for financial institutions, research organizations, and any entity that relies on extensive data for strategic insights.
Scenario: A financial analysis tool imports historical stock market data from an external financial database. This data is used to perform trend analysis, generate reports, and provide investment recommendations to users. Regular data imports ensure that the analysis tool has the latest market information.
- Use Case: User Requests
Capturing and processing data generated by user interactions with a system to personalize experiences and provide actionable insights is fundamental for social media platforms, e-commerce sites, and interactive online services.
Scenario: When a user interacts with a social media application by liking a post, leaving a comment, or sharing content, these actions generate data that the system records. This user-generated data helps personalize the user experience, target advertisements, and analyze user engagement.
- Use Case: Data Imports from File Systems
Importing and integrating data from disparate file systems into a centralized repository for unified analysis and business intelligence is crucial for organizations that must consolidate data from various sources to gain comprehensive insights.
Scenario: A company consolidates data from various departments by importing files stored in different departmental file systems. This data, such as sales reports, customer feedback, and inventory logs, is integrated into a centralized data warehouse.
Understanding and effectively managing data ingress is crucial for maintaining the flow of information into a system, ensuring that applications function smoothly and that data is available for analysis, monitoring, and decision-making.
Keep reading to learn some best practices for managing data egress and ingress.
Best Practices for Managing Data Egress and Ingress
Data egress and ingress best practices are crucial as data traffic grows in volume and complexity. Effective management ensures seamless communication, optimizes performance, and enhances security.
Below are some of the best practices for managing data egress and ingress.
Best Practice 1: Implementing Security Measures
Robust security measures are critical for protecting data during egress and ingress. Securing data ingress and egress is crucial to:
- Protecting sensitive information
- Maintaining privacy
- Securing your network and systems
Implementing security measures ensures that sensitive information remains secure from potential threats and breaches. Maintaining robust network security in complex egress and ingress traffic involves several practices:
- Access Control: Limit sensitive data access to authorized users and applications. To manage permissions effectively, use techniques like role-based access control (RBAC) and attribute-based access control (ABAC).
- Firewall: Install firewalls and intrusion prevention systems (IPS) at the network’s perimeter to monitor and control incoming and outgoing traffic. Set firewall rules to allow necessary traffic and block malicious traffic.
- Network Segmentation: Divide your network into different zones based on the sensitivity of the data and applications. This procedure can help lessen a breach’s potential impact and narrow the attack surface.
- Data Loss Prevention (DLP): Use DLP tools to monitor and restrict sensitive data from leaving the network. DLP solutions can detect sensitive information in data streams and enforce policies to prevent unauthorized data egress.
- Virtual Private Networks (VPNs): Implement VPNs to create secure, encrypted tunnels for data transmission between remote users, devices, or networks.
- Monitoring and Logging: Monitor network traffic and system events to detect and respond to security incidents. Use SIEM tools to analyze logs and identify threats.
- Employee Training: Train employees to recognize and avoid security threats like phishing emails and social engineering attacks. Encourage them to follow best practices for handling sensitive data.
- Endpoint Security: Secure all devices (computers, servers, and mobile devices) with up-to-date antivirus software, security patches, and robust authentication methods.
- Continuous Monitoring: Implement real-time monitoring tools to monitor ingress and egress traffic. Monitoring tools help quickly identify unusual data flows that might indicate a security breach or policy violation.
- Encryption: Encrypt sensitive data for both egress and ingress traffic to protect data integrity and confidentiality, especially over public networks. Use robust encryption protocols like Transport Layer Security (TLS) for data transmitted over the internet.
Pro Tip: For data stored in databases, use advanced encryption methods like AES-256.
- Regular Audits: Conduct regular security audits and reviews of egress and ingress rules to ensure they are up-to-date with current security policies and threats.
- Policy Enforcement: Implement strict policy enforcement mechanisms for all data entering and leaving the network, ensuring compliance with organizational security standards and regulations.
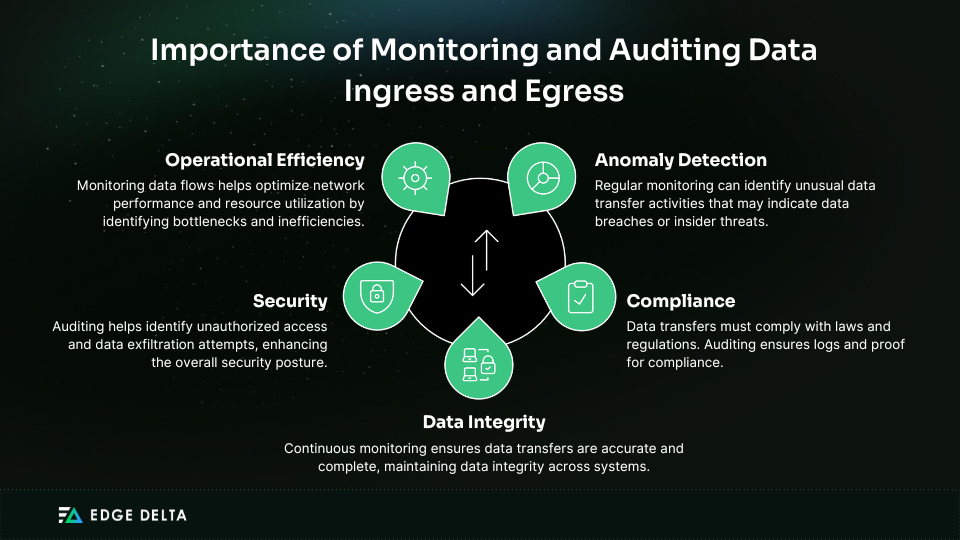
Best Practice 2: Monitoring and Auditing
Monitoring and auditing data egress and ingress activities are essential for data integrity, anomaly detection, and organizational and regulatory compliance. Effective monitoring helps identify unusual data transfer patterns, which could indicate potential security breaches or unauthorized access.
Auditing provides a historical record of data movements, aiding in forensic investigations and compliance reporting. The importance of monitoring and auditing data egress and ingress includes the following:
The dual requirement to secure data leaving and entering the network requires comprehensive monitoring tools and strategies to detect and mitigate threats in real-time.
As data moves between endpoints and processing stages, it becomes vulnerable to cyberattacks and internal misuse. Thus, robust monitoring and auditing tools are essential to protecting this data and network integrity.
The following table shows monitoring and auditing tools for managing data egress and ingress:
| Tool | Key Features | Benefits |
| Splunk | Real-time monitoring, anomaly detection, comprehensive audit trails | Centralized logging, powerful search capabilities, scalability |
| Datadog | Network monitoring, anomaly detection, compliance monitoring | Integrates with cloud platforms, customizable dashboards |
| Elastic Stack | Real-time data monitoring, audit logging, anomaly detection | Open-source, highly customizable, large community support |
| AWS CloudTrail | Logging API calls, monitoring user activity, auditing AWS resources | Integrated with AWS services, detailed logging, compliance |
| Azure Monitor | Monitoring and diagnostics, activity logs, security alerts | Native to Azure, integrates with other Azure services |
| Google Cloud Audit Logs | Activity monitoring, access transparency, compliance logging | Integrated with GCP, real-time monitoring, detailed logging |
| Edge Delta | Real-time observability, anomaly detection, compliance monitoring | Automated insights, scalable, integrates with multiple data sources |
Best Practice 3: Optimizing Data Transfers
Optimizing data transfers is crucial for improving system performance, reducing costs, and ensuring efficient resource usage. Effective data transfer management enhances the speed and reliability of your operations and mitigates potential bottlenecks and security risks.
These benefits are especially important for data egress and ingress, which affect system efficiency. Here are key techniques to optimize data transfers:
- Data Compression
Data compression reduces data size, speeding up egress and ingress while lowering bandwidth usage and costs, especially with large data volumes. Use lossless compression algorithms like ZIP, GZIP, or LZ4 for text files, logs, and other data types that cannot tolerate loss.
Lossy compression methods like JPEG or MP3 significantly reduce file sizes for multimedia files with acceptable data loss. Automate compression with scripts or data transfer tools featuring built-in compression and choose the correct algorithm based on data type, speed, and compression ratio.
- Implement efficient transfer protocols
Efficient transfer protocols enhance the speed and reliability of data transfers while reducing the risk of data loss and errors. Use SFTP for secure file transfers and HTTPS for web-based transfers, which encrypt data for added security. UDP-based protocols like QUIC are ideal for real-time data transfers and low-latency applications.
Tools and libraries can optimize these protocols for fast file transfers. Choose protocols based on security, data sensitivity, and network conditions.
- Schedule transfers during off-peak times
Scheduling data transfers during off-peak times minimizes the impact on network performance and reduces the likelihood of congestion and delays.
Use automation tools to schedule transfers during off-peak hours and apply rate limiting during peak times to protect critical applications. Analyze network usage patterns to identify off-peak hours and automate transfers accordingly.
Best Practice 4: Managing Costs
Data egress costs are relatively low, but they can quickly escalate, particularly with frequent transfers of large datasets. Understanding the factors that influence these costs—such as data volume, transfer destinations, and provider-specific pricing terms—is essential.
Effective data flow management can save businesses money and predict IT budgets. Below are some critical cost management practices to optimize and monitor your data traffic, ensuring your cloud operations are efficient and cost-effective.
- Choose Cost-effective Cloud Services
When managing data egress and ingress, compare the pricing models of various cloud providers to find the most economical options for data transfer. Utilize free data transfer allowances and discounts for long-term commitments offered by your provider.
Select storage locations within the same region or availability zone to minimize cross-region data transfers. This technique reduces the costs associated with data moving in and out of different regions.
- Reduce Unnecessary Data Transfers
Compress data before transfer to reduce its size, using techniques such as gzip for text files or advanced algorithms for binary data. This technique minimizes both ingress and egress costs.
Implement caching mechanisms to keep frequently accessed data closer to the application, reducing redundant data retrievals and egress charges. Employ differential (delta) transfers to send only changes between data sets instead of the entire data set.
- Implement Data Transfer Policies
Schedule data transfers during off-peak hours to benefit from lower ingress and egress rates. To stay within budget, utilize automated tools to monitor and manage data transfers, providing insights and alerts.
- Optimize Data Architecture
Partition data to store and process relevant data together, reducing cross-region transfer needs and lowering egress costs. Use hybrid cloud architectures to store and process data on-premises and in the cloud, reducing cloud transfers and expenses. Process data closer to its source with edge computing to reduce large data transfers to central cloud servers and egress costs.
- Utilize Content Delivery Networks (CDNs)
Employ CDNs to cache frequently accessed content closer to end-users, reducing egress charges by shortening the data travel distance.
- Strategic Data Storage Selection
Choose appropriate storage classes based on access patterns to optimize costs and leverage lifecycle policies for cost-effective transitions. Over time, leverage lifecycle policies to automatically transition data to the most cost-effective storage class.
- Optimize Network Traffic
Analyze and optimize traffic to minimize unnecessary transfers and use centralized management services.
- Enable Cost Allocation Tags
Use cost allocation tags to attribute data transfer costs to specific projects or departments, providing visibility and helping manage high-cost activities.
Conclusion
Data egress and ingress are fundamental concepts in networking and cloud computing, defining data flow into and out of a network. Effective management of these data points is crucial for optimizing network performance, ensuring security and compliance, enabling scalability, and facilitating troubleshooting.
By adhering to best practices and industry standards, network administrators can provide efficient data flow and protect their networks’ integrity and confidentiality.
FAQ for Data Egress vs Ingress
u003cstrongu003eWhat does data egress mean?u003c/strongu003e
Data egress refers to transferring data from a cloud provider’s infrastructure to a user’s local system or another cloud provider. This process may include downloading files, streaming content, or transferring data between services.
u003cstrongu003eWhat are ingress and egress rules?u003c/strongu003e
Ingress and egress rules are like gatekeepers for a network. Ingress rules decide what data can enter the network, while egress rules control what data can leave. These rules make managing and securing network traffic easier, replacing older methods that require more complicated setups.
u003cstrongu003eWhat are data ingress and egress charges?u003c/strongu003e
Ingress and egress charges are the costs of transferring data between cloud regions and zones and between the internet and on-premises networks. Although data ingress is typically free, all providers charge for data egress.