Insights from Domain Name System (DNS) logs provide broader visibility into the overall state of your network, so IT and Security teams can quickly diagnose issues and strengthen protection.
Edge Delta’s Microsoft DNS Server Pack is a pre-built set of processors designed to transform and normalize DNS logs for more consistent and efficient analysis and tracking.
Want Faster, Safer, More Actionable Root Cause Analysis?
With Edge Delta’s out-of-the-box AI agent for SRE, teams get clearer context on the alerts that matter and more confidence in the overall health and performance of their apps.
Learn MoreThe pack was designed for Edge Delta Security Data Pipelines, which standardize, enrich, and stream data to security platforms and archives. The result of this combination delivers a sharper, real-time view of DNS transactions so teams can speed response times and better protect networks.
In this post, we’ll cover installing the Microsoft DNS Pack, how it processes your data, and what you can expect once it’s live.
What is the Microsoft DNS Server Pack and How Does It Work?
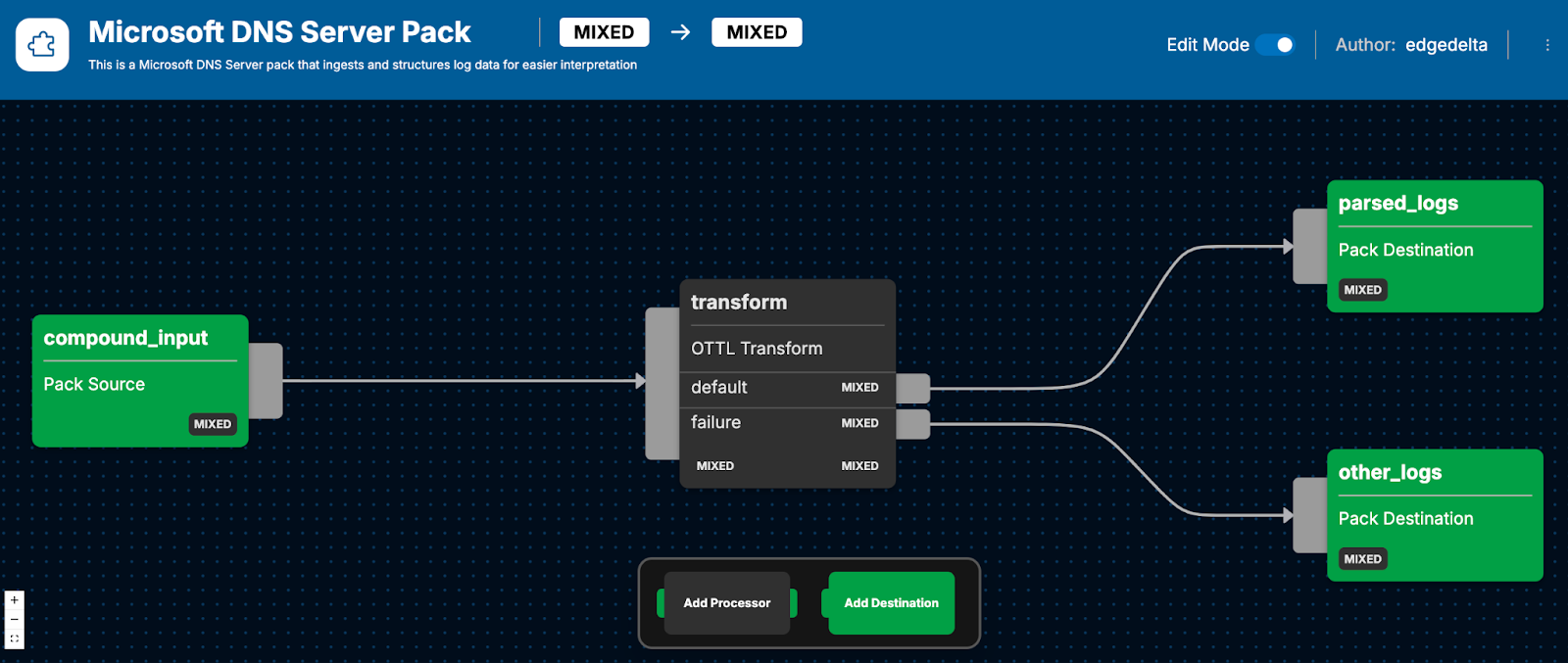
The Microsoft DNS Server Pack consists of a four-step, automatic, sequential processing journey — which begins with a Source node and ends with two Processed compound output nodes — that filters, optimizes, and organizes Microsoft DNS log data for enhanced, easier-to-interpret insights.
The bulk of log processing in this pack occurs within a single, OpenTelemetry Transformation Language (OTTL) transform node, which performs body decoding, pattern extraction, normalization, and attribute updating.
Afterwards, you’ll have two separate output nodes from which you can route your logs:
parsed_logs— route the improvements made to the overall structure of the logs
other_logs— send any remaining logs that failed a pack processing step
In either case, you can ship your logs to any downstream destination for deeper investigation and/or to simple storage for compliance or later analysis.
Processing Pathway: Log Transformation
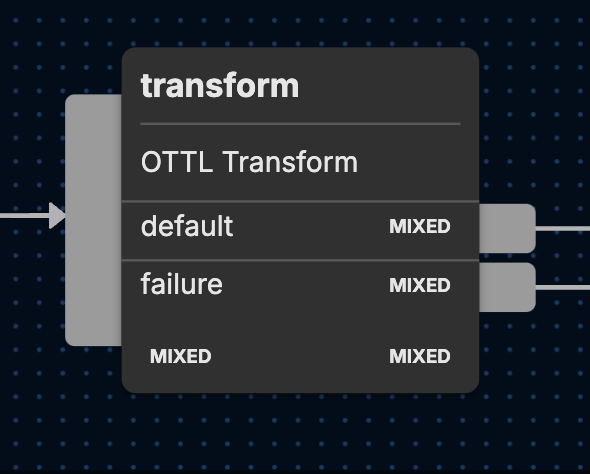
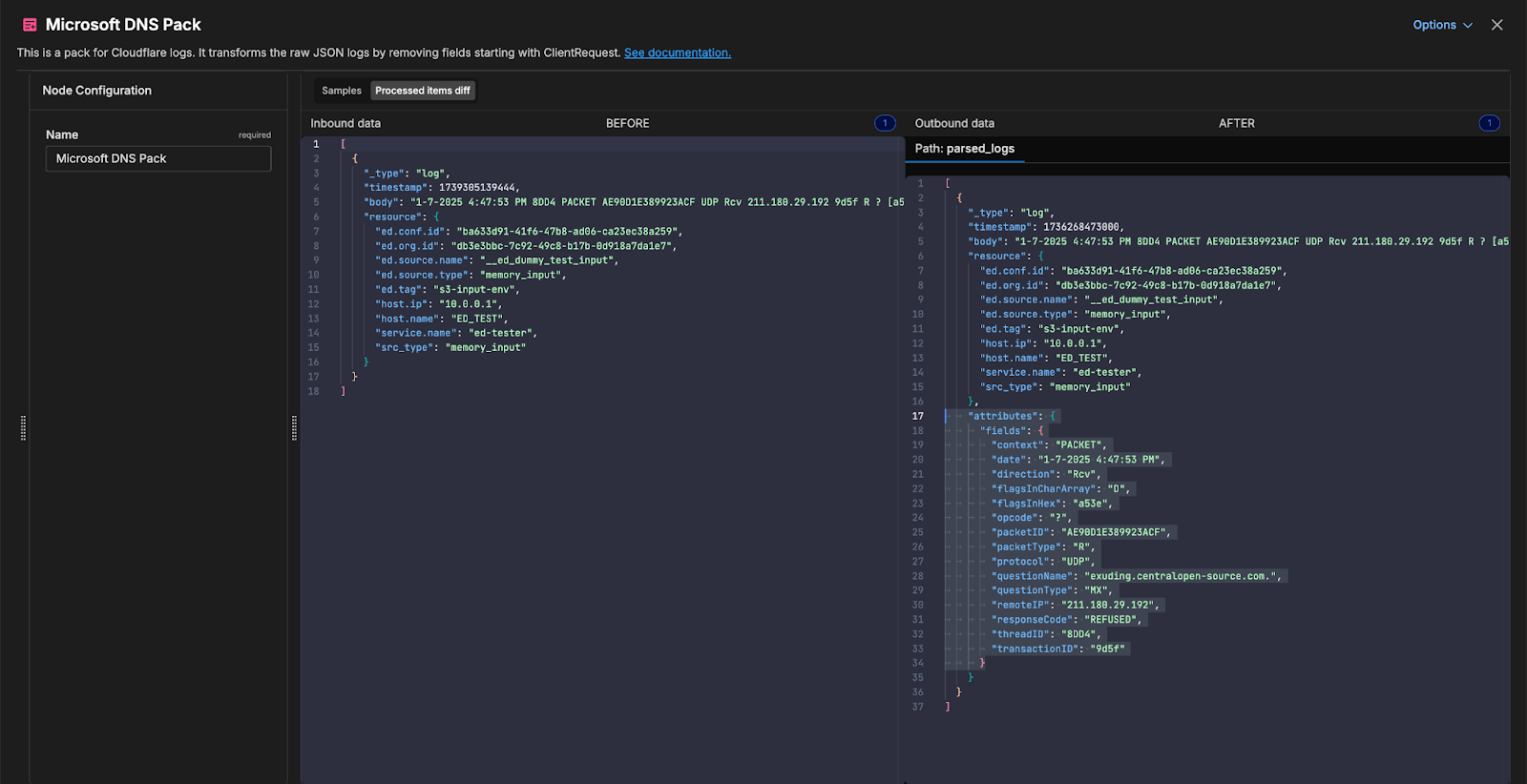
After data begins flowing into the entry point for the Microsoft DNS Server Pack via the compound_input node, logs start processing via the {transform} node with the following five functions:
Body Decoding
Decodes the DNS log message body via the character encoding standard Unicode Transformation Format 8-bit (UTF-8).
Pattern Extraction
Parses unstructured data into a structured format by extracting named capture groups from the target string using Grok patterns. If there are no matches found, an empty map is returned.
Normalization
Structures the file’s questionName and packetType to a consistent format by removing extraneous characters and conditionally modifying the respective value.
Time Normalization:
Converts date strings into UNIX milliseconds through the following steps:
- The
UnixMillifunction converts atime.timeobject to its Unix timestamp representation, measured in milliseconds sinceJanuary 1, 1970UTC. It is applied to a time value obtained from thetimefunction to set the timestamp. - Then, the
timefunction parses a string representation of time into atime.timeobject based on a specified format. It is used here to parse the date extracted by the Grok patterns.
Attributes Update
Finally, the parsed and normalized attributes are set in the attributes section of the log item for further utilization.
Processing Pathway: Processed Outputs
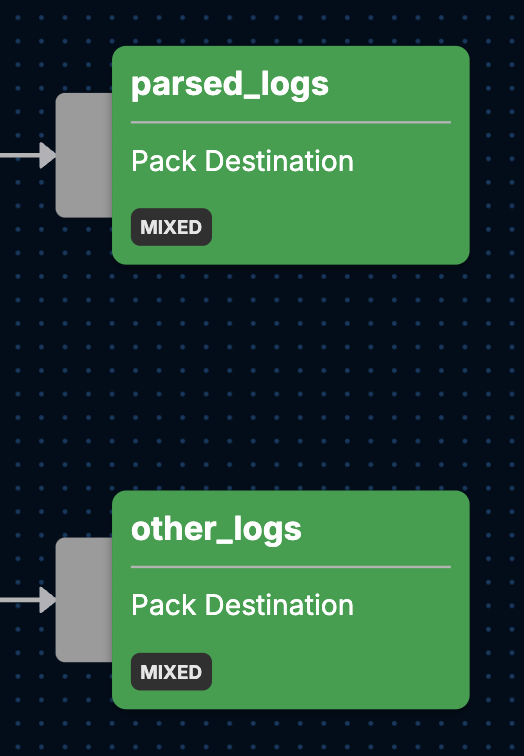
After all transformations have been made, the DNS logs then flow into one of two potential outputs:
parsed_logs: all log data that has successfully been transformed
- name: parsed_logs
type: compound_output
other_logs: logs that failed a transformation
- name: other_logs
type: compound_output
You can then route both parsed_logs and other_logs to the destinations of your choice.
Microsoft DNS Server Pack in Practice
To get started with the Microsoft DNS Server Pack, you’ll first need an existing pipeline within Edge Delta. If you don’t have an Edge Delta pipeline created yet, you can navigate to Pipelines, select New Fleet, and choose whether you want your pipeline to be configured with an Edge Fleet or Cloud Fleet — which correspond with the environments in which they’re hosted — and then follow the remaining setup steps.
Once your pipeline is running, navigate to the top-level Pipelines menu, and select “Knowledge,” and then “Packs.” From there, scroll to the Microsoft DNS Server Pack and click “Add pack.” This will send the Microsoft DNS Server Pack to your pack library, which you can access from the Pipelines menu under “Packs.”
Head back to your main Pipelines dashboard, select the pipeline where you’d like to add the Microsoft DNS Server Pack, enter “Edit Mode,” and configure the pipeline with the Visual Pipelines builder. In edit mode, navigate to “Add Processor,” then “Packs,” and find the Microsoft DNS Server Pack.
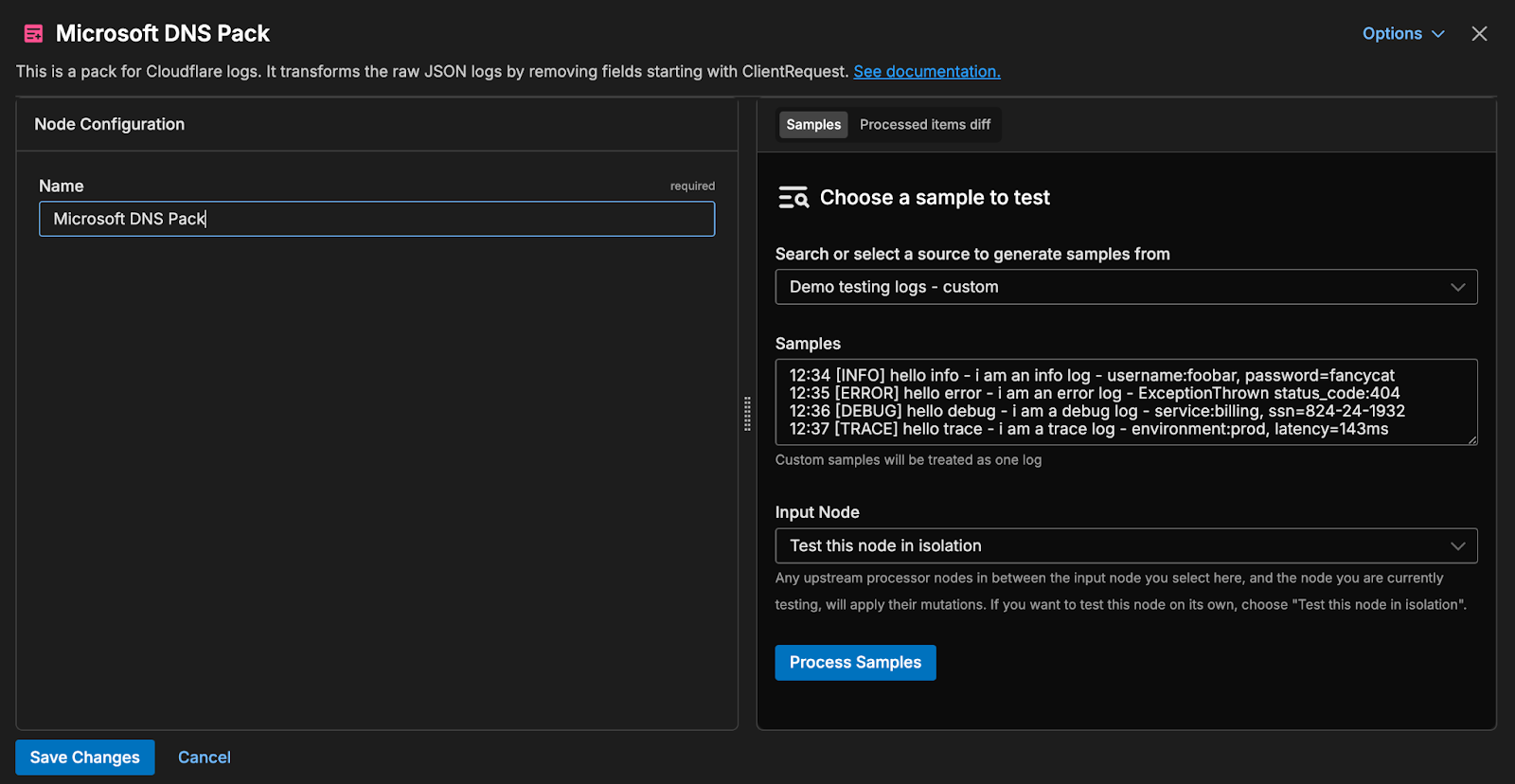
At this point, you’ll be given the option to rename the pack and choose some sample logs to test. When you’re ready, hit “Save Changes,” and the Microsoft DNS Server Pack will be added to your pipeline. Then, drag and drop the connection from the initial Microsoft DNS logs source into the pack.
Next, Edge Delta Security Pipelines allow you to ship your processed Microsoft DNS Server logs to a destination of your choosing.
For example, processed logs can be routed to your current SIEM vendor — whether that’s Splunk, Microsoft Sentinel, CrowdStrike Falcon, or others.
You can also route your data into Edge Delta, and take advantage of our log analysis capabilities. Additionally, you can send a full copy of all your raw log data to archival storage destinations such as S3 for compliance or later analysis.
Getting Started
Ready to see Edge Delta’s Microsoft DNS Server Pack in action? Check out our packs list and add the Microsoft DNS Pack to any running pipeline. New to Edge Delta? Visit our Playground to get a feel for how we can help you change the way you manage your security data.








