DevOps teams are starting to embrace two key tools for infrastructure automation and deployment management: Terraform and Ansible.
Terraform, by HashiCorp, uses a cloud-agnostic, declarative syntax to manage and version infrastructure as code, simplifying the provisioning of diverse resources. Ansible focuses on configuration management and application deployment, automating tasks across servers with an agentless, declarative approach.
Automate workflows across SRE, DevOps, and Security
Edge Delta's AI Teammates is the only platform where telemetry data, observability, and AI form a self-improving iterative loop. It only takes a few minutes to get started.
Learn MoreThe former excels at infrastructure management, while the latter ensures consistent configurations and deployments. Together, they enhance IT automation by improving efficiency, scalability, and reliability. They reduce errors and costs and accelerate provisioning, driving digital transformation and operational excellence for an agile and productive IT environment.
Keep reading to find out how to use Terraform and Ansible to automate infrastructure and deployments.
Key Takeaways:
Automating infrastructure and deployments increases efficiency, consistency, scalability, and reduces human error. Terraform creates, updates, and deletes resources based on your specified infrastructure state.Ansible is an IT automation tool that streamlines provisioning, configuration management, application deployment, and orchestration.Proper Terraform state management is critical for resource tracking, consistent deployment, and security. Integrating Terraform and Ansible automates infrastructure provisioning and configuration management from start to finish. Creating modular and reusable configurations in Terraform and Ansible is essential for modern DevOps and infrastructure management.
A Guide on Using Terraform with Ansible for Infrastructure and Deployment Automation
Terraform allows you to write code to define and manage infrastructure on cloud platforms like AWS and GCP. Using a declarative approach, Terraform automatically creates, updates, and deletes resources to match your chosen infrastructure state.
This method ensures consistency and minimizes deployment errors. Terraform supports multiple providers with a single configuration file, making infrastructure management predictable, reproducible, and scalable.
Ansible is an IT automation tool that simplifies provisioning, configuration management, application deployment, and orchestration. It uses an agentless architecture with SSH for communication, requiring no additional software on managed nodes.
Ansible’s human-readable YAML playbooks make automation scripts easy to write and understand, efficiently handling large-scale automation tasks and ensuring system consistency and reliability.
Here’s a quick view comparison table for Terraform vs. Ansible:
| Points of Comparison | Terraform | Ansible |
| Type | Infrastructure as Code (IaC) | Configuration Management & Automation |
| Language | HashiCorp Configuration Language (HCL) | YAML |
| Approach | Declarative | Procedural |
| State Management | Maintains state files | Stateless |
| Multi-cloud Support | Yes | Yes |
| Primary Use Case | Infrastructure provisioning | Configuration management, deployment, orchestration |
Read on to learn how to do complete automation using Terraform and Ansible.
Automating Infrastructure with Terraform
Terraform, a robust IaC tool, automates and streamlines infrastructure provisioning, management, and scaling. By writing simple, human-readable configuration files, you can define your entire infrastructure and deploy it consistently across multiple cloud platforms.
Whether you are managing a few resources or complex multi-cloud environments, Terraform streamlines infrastructure management, reducing manual intervention and improving reliability.
Continue reading to learn how to automate infrastructure using Terraform.
1. Setting Up Terraform
To begin using Terraform, you need to install it on your local machine and configure it to interact with your chosen cloud provider.
- Setup Credentials on the Cloud Provider Platform
Configuring your credentials is the first step in building the infrastructure with Terraform. This step is crucial for Terraform to interact with your cloud platform account.
For example, if you want to set up your credentials on Amazon Web Services (AWS), follow these steps:
- Access the AWS Management Console.
- Navigate to the IAM (Identity and Access Management) dashboard.
- Create a new IAM user and assign the necessary permissions.
- Generate an IAM user access key and secret key.
- Install and Configure Terraform
To use Terraform, you need to install it on your operating system:
- Obtain Terraform from the official Terraform website.
- Install Terraform based on your operating system.
- Confirm the installation’s success by executing the terraform –version command.
- Set up your credentials by executing the necessary command.
Code example for installing Terraform:
curl -LO https://releases.hashicorp.com/terraform/1.0.0/terraform_1.0.0_linux_amd64.zip
unzip terraform_1.0.0_linux_amd64.zip
mv terraform /usr/local/bin/
terraform -version
2. Creating and Applying Terraform Configurations
With Terraform installed and configured, you can now define and apply infrastructure configurations.
- Define Your Infrastructure
Create Terraform configuration files to define the infrastructure you wish to establish. These files typically have a .tf extension. For instance, to establish an AWS EC2 instance, create a main.tf file.
Code example for basic Terraform configuration:
provider "aws" {
region = "us-west-2"
}
resource "aws_instance" "example" {
ami = "ami-0c55b159cbfafe1f0"
instance_type = "t2.micro"
}
- Initialize and Apply
After preparing your configuration files, you must initialize your working directory and apply the configuration to create the infrastructure.
Code example for applying Terraform configuration:
terraform init
terraform plan
terraform apply
3. Managing Terraform State
Properly managing the Terraform state is essential for tracking resources, ensuring consistent deployments, and maintaining security. The state file records the infrastructure’s current state, enabling Terraform to map resources, detect changes, and plan updates.
Remote state backends enhance collaboration by allowing shared access to the state file. They also offer encryption and access control features, ensuring the state file is secure and preventing issues like data loss or conflicts.
Add a backend configuration block to your Terraform configuration to set up a remote backend. For example, using an S3 bucket as a remote backend:
terraform {
backend "s3" {
bucket = "my-terraform-state-bucket"
key = "path/to/my/terraform.tfstate"
region = "us-west-2"
encrypt = true
dynamodb_table = "my-lock-table"
}
}
Automating Configuration and Deployments with Ansible
As a powerful IaC tool, Terraform allows you to automate and streamline your infrastructure’s provisioning, management, and scaling. By writing simple, human-readable configuration files, you can define your entire infrastructure and deploy it consistently across multiple cloud platforms.
Terraform streamlines infrastructure management, reducing manual intervention and improving reliability in single-cloud or multi-cloud environments. Keep reading to learn how to automate configuration and deployments with Ansible.
1. Setting Up Ansible
To start using Ansible, you’ll need to install it on your system and configure the inventory files that define the hosts Ansible will manage.
Here are a few simple steps to setting up Ansible:
- Update your package lists
sudo apt update
- Install Ansible
sudo apt install ansible -y
- Verify the installation
ansible --version
- Create an inventory file
An inventory file lists the hosts and groups of hosts on which Ansible will operate. Create a file named inventory and add your hosts.
[webservers]
webserver1.example.com
webserver2.example.com
2. Creating and Running Ansible Playbooks
Playbooks are the heart of Ansible’s automation. They allow you to define your systems’ desired state in a human-readable YAML format and systematically manage configurations and deployments.
- Create a playbook file (e.g., myplaybook.yml):
Here’s an example of a basic Ansible playbook:
---
- hosts: webservers
become: yes
tasks:
- name: Install Nginx
apt:
name: nginx
state: present
- Run the playbook
ansible-playbook -i inventory myplaybook.yml
3. Using Ansible Roles and Modules
Ansible uses roles and modules to keep your playbooks organized and reusable. Roles group related tasks, variables, files, templates, and handlers into cohesive units, allowing for modular and reusable components that simplify complex configurations.
Modules, the building blocks of Ansible tasks, are scripts that perform specific actions on managed nodes. Roles and modules enable scalable, maintainable playbooks, enhancing code readability and collaboration while streamlining system and network administration tasks.
- Creating Ansible Roles
Roles allow you to break down your playbooks into reusable components.
- Create a new role
ansible-galaxy init myrole
- Use the role in a playbook
---
- hosts: webservers
roles:
- role: myrole
- Using Ansible Modules
Modules are the building blocks of tasks in Ansible. Here are a couple of examples of using modules:
- Managing a user
- name: Manage user
user:
name: johndoe
state: present
- Installing a package
- name: Install Apache
apt:
name: apache2
state: present
Combining Terraform and Ansible for Complete Automation
Terraform excels at provisioning infrastructure resources, while Ansible excels at configuration management. Integrating these two tools allows you to achieve comprehensive automation for creating and managing infrastructure.
Read on to find out how to complete automation by combining Terraform and Ansible.
1. Integrating Terraform and Ansible
Integrating Terraform and Ansible allows for end-to-end infrastructure provisioning and configuration management automation. Terraform first sets up the necessary infrastructure, and then Ansible configures it. This combination ensures that both infrastructure and applications are consistently deployed and configured.
Here’s an example of how to use Terraform to provision an AWS instance and then use Ansible to configure it:
# Example Terraform configuration using Ansible provisioner
resource "server_instance" "example" {
image_id = "image-12345"
instance_type = "small"
provisioner "local-exec" {
command = <<EOT
ansible-playbook -i ${self.public_ip}, -u user playbook.yml
EOT
}
}
In this configuration, Terraform provisions a server instance. The local-exec provisioner runs an Ansible playbook to configure the instance once it’s running.
2. Use Case Example: Web Server Deployment
To demonstrate the power of combining Terraform and Ansible, let’s walk through an example of deploying a web server. We will use Terraform to provision the infrastructure and Ansible to install and configure the web server.
- Terraform configuration
First, define the Terraform configuration to provision a server instance:
# Terraform configuration
provider "cloud" {
region = "region-1"
}
resource "server_instance" "web" {
image_id = "image-12345"
instance_type = "small"
provisioner "local-exec" {
command = "ansible-playbook -i ${self.public_ip}, -u user playbook.yml"
}
}
This Terraform script sets up a server instance in the specified region and runs an Ansible playbook using the local-exec provisioner.
- Ansible Playbook
Next, we define the Ansible playbook to install and configure Nginx on the provisioned instance:
# Ansible playbook
---
- hosts: all
become: yes
tasks:
- name: Install Nginx
apt:
name: nginx
state: present
This playbook updates the apt cache, installs Nginx, and ensures it is running.
Combining Terraform and Ansible: Step-by-Step
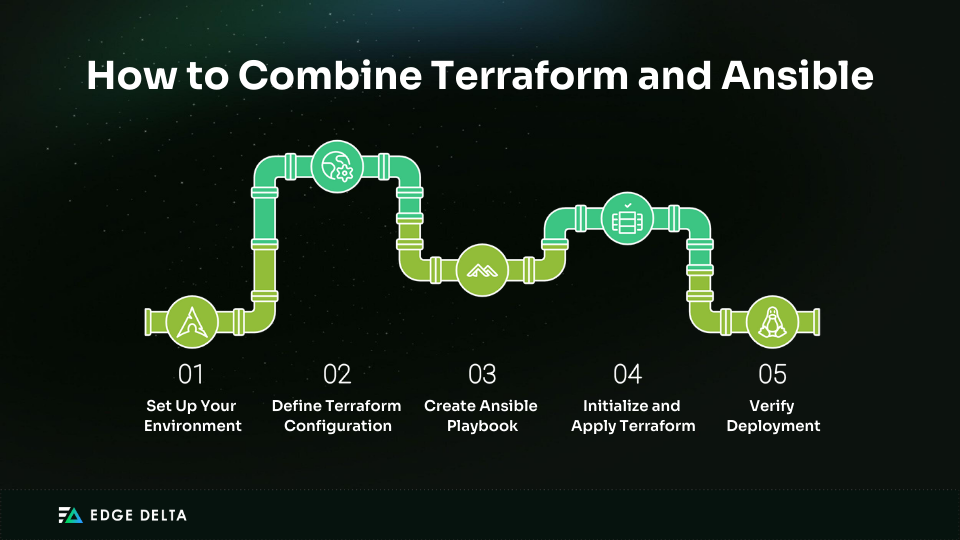
- Set Up Your Environment
- Create a project directory with Terraform and Ansible configurations.
- Generate an SSH key pair for secure server access.
- Define Terraform Configuration
- Specify the provider, variables, and resources.
- Use the local-exec provisioner to run the Ansible playbook after provisioning the infrastructure.
- Create Ansible Playbook
- Write a playbook to handle the server configuration (e.g., installing Nginx).
- Initialize and Apply Terraform
- Navigate to your project directory and run terraform init to initialize the project.
- Execute terraform apply to provision the infrastructure and automatically run the Ansible playbook.
- Verify Deployment
- Check your cloud provider’s console to verify the instance is up.
- Access the instance’s public IP in a browser to confirm Nginx is installed and running.
By integrating Terraform and Ansible, you can automate the entire process of provisioning infrastructure and configuring applications, leading to a more efficient, reliable, and scalable deployment process.
Best Practices for Using Terraform and Ansible
By codifying infrastructure and configuration management, you can achieve greater consistency, reduce manual errors, and streamline the deployment process. However, to maximize the benefits of these tools, it’s essential to follow best practices.
Discover the best practices for using Terraform and Ansible below.
1. Version Control and Collaboration
Effective management of Terraform and Ansible configurations is crucial for maintaining IaC integrity and promoting team collaboration. Utilizing version control systems (VCS) like Git can significantly enhance this process. Here are some best practices to consider:
- Use a Dedicated Version Control Repository
Maintain separate repositories for Terraform and Ansible configurations. This technique helps isolate infrastructure management from configuration management, making handling and tracking changes easier.
Organize repositories with a clear directory structure. For Terraform, segregate by environments (e.g., dev, staging, production). For Ansible, use a directory layout that includes roles, playbooks, and inventory directories.
- Commit Small, Atomic Changes
Make small, incremental commits that encapsulate a single change or feature. This practice simplifies code reviews and debugging. Write clear and descriptive commit messages to provide context about the changes. For example, “Added security group rules for web servers” is more informative than “Updated Terraform script.”
- Branching Strategy
Use feature branches for new developments. Merge them into the main branch only after thorough testing and code review. Maintain separate branches for different environments to prevent untested code from affecting production environments.
- Implement Code Reviews
Conduct peer reviews regularly to ensure code quality and adherence to best practices. Code reviews help catch issues early and foster knowledge sharing among team members.
- Collaboration Tools
Use PRs to facilitate discussions and reviews before merging changes into the main branch. PRs should describe changes, the problems they solve, and any relevant context. Use GitHub Issues, Jira, or similar tools to track bugs, features, and tasks. Link issues to commits and PRs for better traceability.
- Testing and Validation
Implement automated testing for Terraform using the Terraform plan and Terraform validation. For Ansible, use ansible-playbook –syntax-check and ansible-lint. Integrate version control with CI/CD pipelines (e.g., GitLab CI, Jenkins) to automate the testing, validation, and deployment of infrastructure changes.
2. Modular and Reusable Configurations
Creating modular and reusable configurations in Terraform and Ansible is fundamental to modern DevOps and infrastructure management. Maintaining a consistent, reliable, and efficient setup becomes increasingly challenging as organizations scale, and their infrastructure becomes more complex.
Modularity and reusability help address these challenges by:
- Breaking down configurations into manageable components
- Standardizing components for easy maintenance
- Scaling configurations as needed
- Reusing components across different projects and environments
Here’s why this approach is crucial:
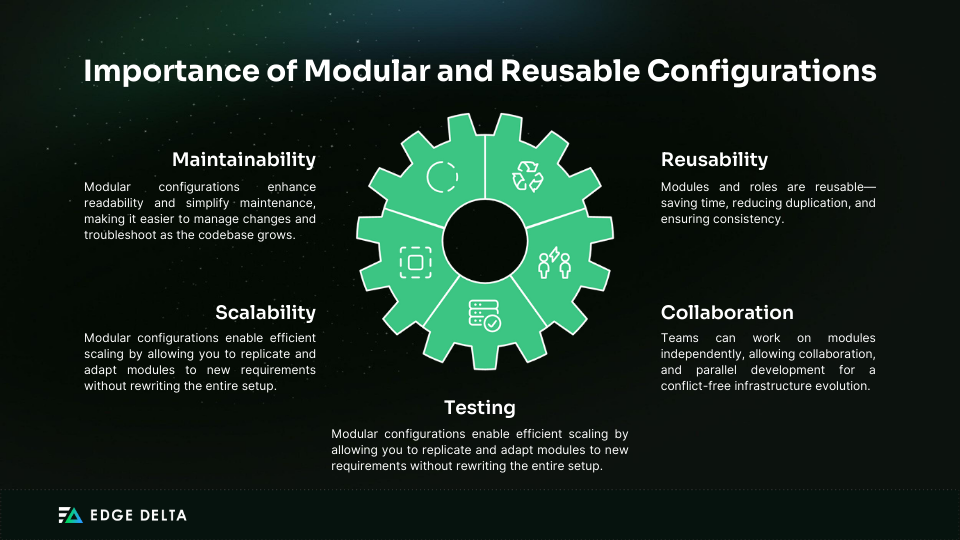
- Maintainability: Modular configurations are easier to read, understand, and maintain. Smaller, well-defined modules simplify managing changes and troubleshooting issues when the codebase grows.
- Reusability: Modules and roles can be reused across different projects and environments, saving time and effort. This approach reduces duplication and ensures consistency across the infrastructure.
- Scalability: Modular configurations allow you to scale more efficiently as your infrastructure grows. You can easily replicate and adapt modules to new requirements without rewriting the entire configuration.
- Collaboration: Teams can work on different modules independently, which improves collaboration and parallel development and ensures that other parts of the infrastructure can evolve without conflict.
- Testing: Smaller modules are easier to test individually. Testing leads to a more robust and reliable infrastructure, as each module can be validated separately before integration.
3. Security Considerations
Security is paramount when Terraform and Ansible are used to manage IaC. Implementing best practices protects your infrastructure from unauthorized access, data breaches, and other security threats. Some of the best security practices include:
- Manage Sensitive Data
Use tools like HashiCorp Vault or Ansible Vault to securely store and manage sensitive data such as passwords, API keys, and certificates. Avoid hardcoding sensitive data in your scripts; store this information in environment variables, which can be dynamically accessed during execution.
Encrypt variables and state files to protect sensitive data at rest. Terraform supports encryption of state files using secure backends like AWS S3 with server-side encryption or Google Cloud Storage with encryption at rest.
- Secure Connections
Use SSH keys for authentication instead of passwords when connecting to remote servers. Ensure SSH keys are properly managed and rotated regularly. All communication between Terraform, Ansible, and remote servers must be secured using SSH keys.
SSL/TLS protocols to prevent man-in-the-middle attacks and ensure data integrity. Use secure remote backends like AWS S3 with IAM roles or Google Cloud Storage with IAM permissions to store Terraform state files securely.
- Least Privilege Principle
The principle of least privilege means granting the minimum level of access required for a particular resource to function correctly. This approach minimizes the potential damage an attacker can do if they gain access to your infrastructure.
Implement Role-Based Access Control (RBAC) to ensure that users and systems have the minimum necessary permissions to perform their tasks. Use IAM roles or policies in Terraform that adhere to least privilege principles, limiting access to only the resources required for specific operations.
Use scoped credentials to limit resource access, reducing the risk of unauthorized access. Adopt an immutable infrastructure approach where infrastructure components are not modified after deployment, reducing the risk of unauthorized changes and maintaining a consistent security posture.
- Regular Audits
Enable and regularly review audit logging to monitor changes made by Terraform and Ansible. This technique helps track unauthorized or malicious activities, providing a trail for forensic analysis.
Implement code review procedures to ensure that multiple team members review Terraform and Ansible scripts, helping to spot possible security flaws before deployment. Automated security scanning tools regularly scan Terraform and Ansible configurations for vulnerabilities and misconfigurations, proactively identifying and mitigating security risks.
Update Terraform, Ansible, and their dependencies regularly with the latest security patches. This practice protects against known vulnerabilities and ensures you use the most secure versions.
4. Continuous Integration and Deployment (CI/CD)
CI/CD is essential to modern DevOps practices as it streamlines the software development lifecycle, promoting rapid, reliable software development and deployment cycles. Integrating Terraform and Ansible with CI/CD pipelines automates the testing, deployment, and monitoring processes.
Best practices include:
- Automated Testing
Use tools like Terratest for Terraform and Molecule for Ansible to automate the testing of your configurations before deployment. These tools help ensure that your infrastructure code works as expected and meets all requirements, reducing the risk of errors during deployment.
- Pipeline Integration
Configure CI/CD tools such as Jenkins, GitLab-CI, or GitHub Actions to automate the execution of Terraform and Ansible scripts. For instance, Terraform plans and applications can run on GitLab-CI, followed by Ansible playbook executions. This automation ensures consistent and repeatable deployments across different environments.
- Environment Segregation
Separate environments (e.g., development, staging, production) in your CI/CD pipelines to ensure isolated and controlled deployments. This practice helps maintain stability and allows for thorough testing in non-production environments before changes are deployed to production.
- Rollback Mechanisms
Implement rollback mechanisms to revert changes in case of failure, ensuring minimal downtime and quick recovery. CI/CD pipelines can be configured to automatically revert to the stable state if a deployment fails, reducing potential issues.
Conclusion
Integrating Terraform with Ansible enables efficient automation of infrastructure and deployments, making it easier to build and scale applications. Leveraging both tools streamlines operations and enhances IT automation. Understanding their distinct functionalities helps IT professionals make better infrastructure decisions in a more responsive environment.
The combination of Ansible and Terraform offers a powerful toolkit for IT transformation. By reducing manual effort, minimizing errors, and improving consistency, these tools allow IT teams to focus on strategic initiatives and drive innovation.
FAQs for How to Use Terraform and Ansible
How do you deploy Terraform infrastructure?
To deploy Terraform’s infrastructure, identify your project’s infrastructure needs. Next, write the configuration. Once the configuration is ready, initialize the project to install the necessary plugins. Use the plan command to preview and apply the changes to deploy the infrastructure.
Can we use Ansible for infrastructure provisioning?
Yes, Ansible can be used to provision infrastructure without pre-existing servers. This means creating virtual machines or cloud instances, configuring them, deploying packages, installing applications, etc. Ansible can run the entire infrastructure provisioning workflow very efficiently.
Can Ansible be used for deployment?
Yes, Ansible can be used for deployment. It is a powerful automation tool that streamlines the application deployment process, providing consistent and reliable deployments, reducing manual effort, and increasing efficiency.
What is infrastructure as code with Terraform and Ansible?
Infrastructure as Code (IaC) with Terraform and Ansible involves using code to automate infrastructure management. Terraform uses a declarative approach to provisioning cloud resources. With an agentless architecture, Ansible focuses on configuration management and task automation. Terraform and Ansible work together to provision infrastructure and manage configuration and application deployment.
Sources








