Cisco Adaptive Security Appliances (ASAs) are cybersecurity hardware devices designed to provide users with highly secure access to data and network resources. They boast a wide variety of security features — including VPN and enterprise-class firewall capabilities — which play a crucial role in preventing threats from entering and expanding within your network infrastructure.
Cisco ASA devices also produce large quantities of telemetry data — in particular, firewall logs. Firewall logs serve as detailed records that capture critical information about events related to the ASA firewall, including attempted network connections and traffic, interface status changes, and much more.
Want Faster, Safer, More Actionable Root Cause Analysis?
With Edge Delta’s out-of-the-box AI agent for SRE, teams get clearer context on the alerts that matter and more confidence in the overall health and performance of their apps.
Learn MoreHowever, analyzing these logs is challenging, as users aren’t able to instrument source code to change their format. Instead, they must first properly process the firewall logs after they’ve been created and collected, before performing any log-based analysis.
Edge Delta’s Cisco ASA Pipeline Pack is a specialized collection of processors built specifically to handle firewall logs in the Cisco ASA format, enabling you to transform your log data to fuel analysis. Our packs are built to easily slot into your Edge Delta pipelines — all you need to do is route the source data into the Cisco ASA pack and let it begin processing.
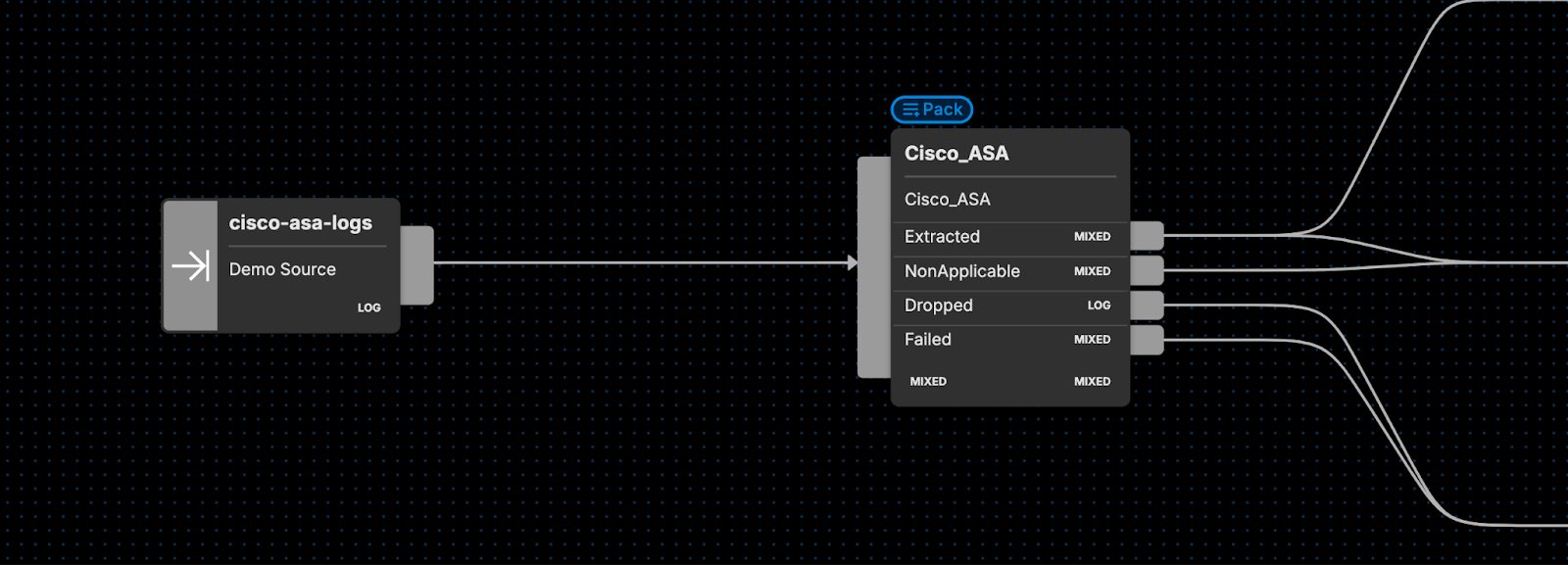
If you are unfamiliar with Edge Delta’s Telemetry Pipelines, they are an intelligent pipeline product built to handle log, metric, trace, and event data. They are also an on-the-edge pipeline solution that begin processing data as it’s created at the source, providing you with greater control over your telemetry data at far lower costs.
How Does the Cisco ASA Pack Work?
The Edge Delta Cisco ASA Pack streamlines log transformation by automatically processing Cisco ASA firewall log data as it’s ingested. Once the processing is finished, these logs can be easily filtered, aggregated, and analyzed within observability platforms of your choosing.
The pack consists of a few different processing steps, each of which play a vital role in allowing teams to use ASA firewall logs to gain crucial insights into their network infrastructure and security events.
Here’s a quick breakdown of the pack’s internals:
Add Fields
The Cisco ASA pack begins with two nodes, which enrich ASA logs by adding metadata to the log items. More specifically, they:
- Extract the code type from the log message and use it to fill a newly created
asa_codefield in theattributessection of the log. - Reference Edge Delta’s ASA code lookup table with the
attributes.asa_codefield as the key to find the corresponding comment, and use the found comment to fill a newly createddrop_messagefield in theattributessection of the log.
Filter Messages
After enrichment, logs are filtered out based on their code type, to ensure we’re only processing the necessary log data in future steps. This is done by:
- Filtering out all logs with an
attributes.drop_messageand routing them to theDroppedoutput, while sending all other logs down for further processing.
Further Enrichment
Once we’ve filtered out the appropriate logs, we can complete processing by enriching the remaining logs one last time. We’ll do this by:
- Referencing Edge Delta’s ASA Regex lookup table with the ASA code as the key to find the corresponding regular expression, and adding it to the log under the
attributessection in theasa_regexfield. - Leverage the extracted regular expression in the
attributes.asa_regexfield to parse the log message for the vendor, product, and vendor_product specifics, and add them to the log under theattributessection in thevendor,product, andvendor_productfields respectively.
Pack outputs
In total, there are four output paths from the Cisco ASA Pack:
Extracted— logs that traveled through each stage successfully, and were properly enriched.Failed— logs that traveled through the first enrichment phase and filter phase successfully, but weren’t able to properly complete the “Further Enrichment” phase.Dropped— logs that were dropped from the “Filter Messages” phase due to having an ASA code present in the ASA code lookup table.NonApplicable— logs in which an ASA code was never found.
For a more in-depth understanding of these processors and the Cisco ASA Pipeline Pack, check out our full Cisco ASA Pipeline Pack documentation.
Cisco ASA Pack in Practice
Once you’ve added the Cisco ASA Pack into your Edge Delta pipeline, you can route the outputted log streams anywhere you choose.
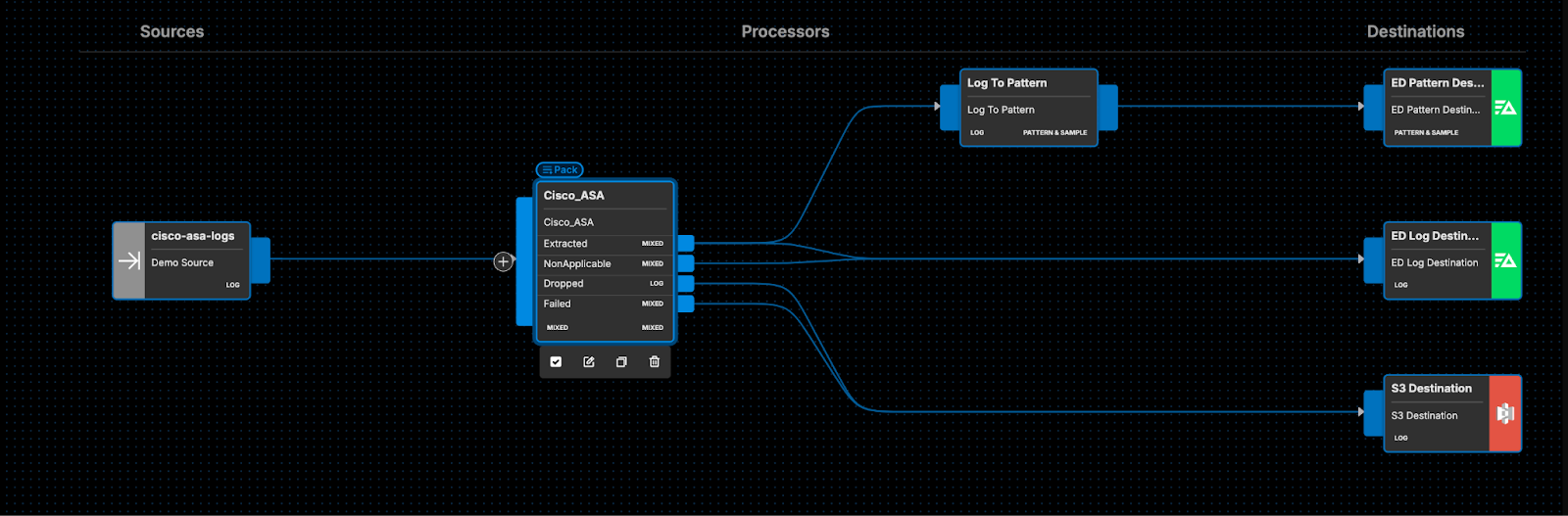
For instance, you can route your newly formatted Cisco ASA logs to ed_patterns_output to leverage Edge Delta’s unique pattern analysis, and to ed_logs_output for log search and analysis with Edge Delta’s Log Management platform, as shown below:
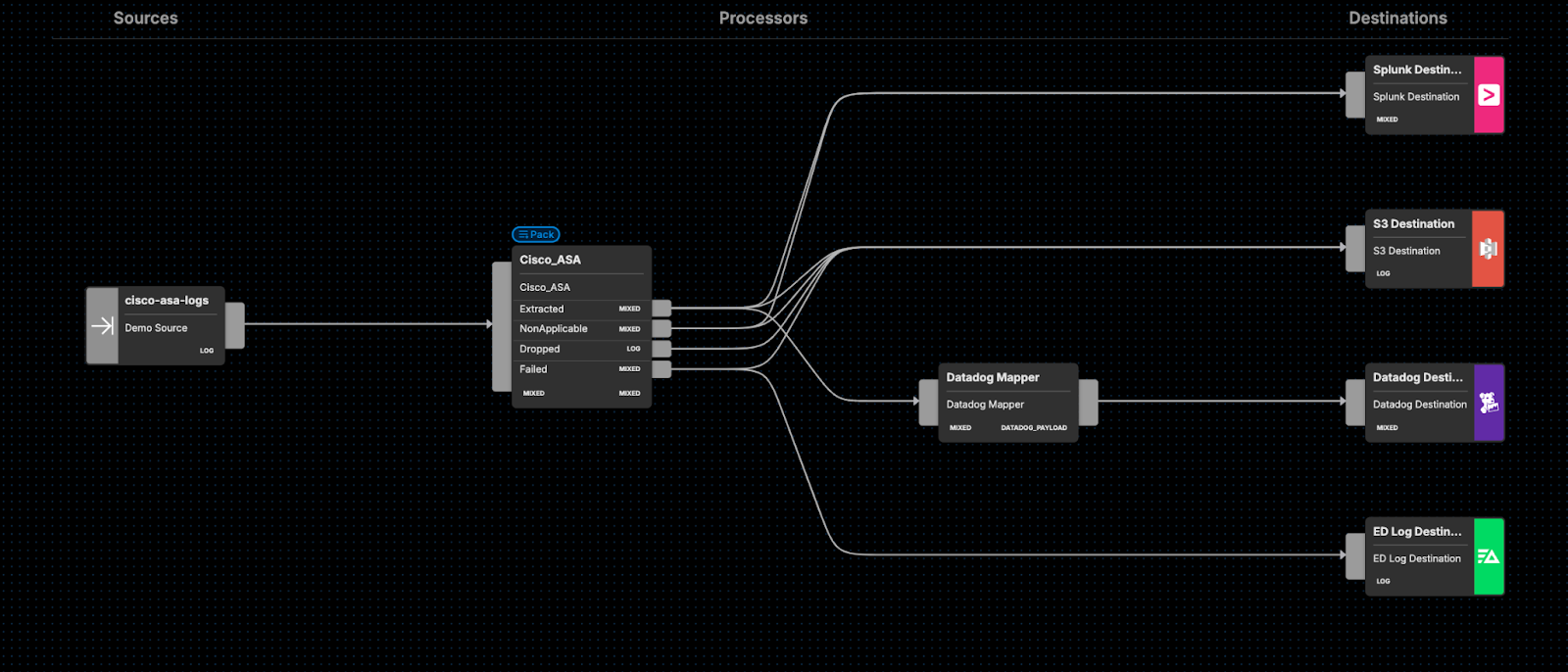
Alternatively, you can route your Cisco ASA logs to other downstream destinations, including (but not limited to) Datadog and Splunk. As always, you can easily route a full copy of all raw data directly into S3 as well:
Getting Started
Ready to see it in action? Visit our pipeline sandbox to try it out for free! Already an Edge Delta Customer? Check out our packs list and add the Cisco ASA pack to any running pipeline.








