The rise of the digital landscape has also led to more security issues. With breaches costing USD 4.45 million in 2023, businesses facing cybersecurity threats are also rising. Fortunately, every system creates security event logs, which help protect a system from these threats.
Security event logs are system records related to security. With these logs, security teams can gain comprehensive insights into a system’s past and present condition. These insights are crucial in detecting or investigating breaches and other security issues.
Want Faster, Safer, More Actionable Root Cause Analysis?
With Edge Delta’s out-of-the-box AI agent for SRE, teams get clearer context on the alerts that matter and more confidence in the overall health and performance of their apps.
Learn MoreAs more businesses face cybersecurity threats, learning what are security event logs is crucial to improving security and protection. The article provides an in-depth discussion of these logs, including their definition, components, types, importance, and modern approaches to maximizing security.
Key Takeaways
- Security event logs are digital records related to a system’s security. It includes login attempts, system modifications, and security policy infractions. With this data, IT teams can comprehensively understand their system’s security.
- Although these logs aim to strengthen security, they come in several types. Each type provides unique data from a different source for a comprehensive analysis.
- Each security event log has five components. These components allow IT teams to seamlessly organize, manage, and analyze all logs.
- While security event logs contain helpful data, they will only be effective with proper management. Thus, it’s crucial to understand the modern approaches to leverage these logs for security.
- Security event logs can provide plenty of security-related benefits to enterprises. However, these logs need proper management, analysis, and organization if a company wants to exploit them.
Security Event Logs: Definition, Types, and Components
Security event logs are digital records created by computer systems and applications. These records provide comprehensive, valuable documentation in detecting noteworthy security-related incidents. With these logs, IT teams can see the timeline of events, including:
- Login attempts
- System modifications
- Security policy infractions
These logs provide insights into security-related activities and enable proactive defense actions. Thus, they help preserve the security and integrity of systems and networks. Some of the activities where security event logs are helpful are:
- Forensic investigation
- Incident response
- Compliance audits
- Monitoring and looking into potential security threats
Security event logs come from hardware, software, and systems. IT teams relate each source’s logs for comprehensive security audits, investigations, and monitoring.
In case you want to know the security event log location on your computer, follow these steps:
- Open “Event Viewer.”
- Expand “Windows Logs” in the console tree.
- Click “Security.”
- Individual security events are listed in the results pane.
- Click “Event” in the results pane for more details about a specific event.
Security Event Logs in a Nutshell
Security event logs are digital recordings documenting security-related events like system modifications, policy breaches, and login attempts. They play a vital role in monitoring, identifying risks, enforcing rules, and ensuring the security of computer systems and networks.
7 Types of Security Logs
Security event logs vary depending on what data or event they provide or their purpose. Here are seven common security log types you may encounter:
| Security Event Log Type | Purpose |
|---|---|
| Security Logs | Used to identify suspicious activity and assaults, such as attempted intrusions and blocked traffic |
| Proxy Logs | Used to monitor user behavior and packet sizes to spot possible security holes |
| Endpoint Logs | Used to find data about malicious activity and device vulnerabilities on PCs, laptops, and mobile devices |
| SAN Infrastructure Logs | Used to track down problems with data flow and connections in storage networks |
| Hypervisor Logs | Used to gain insights into workload management and resource allocation in virtualized systems |
| IoT Logs | Used to gain information on data flow and hardware operation to debug IoT devices |
| Server Logs | Used to understand system performance and activity, including communications between web servers |
In addition to these types, it’s crucial to understand what security event logs provide. The following section will cover every component of a security event log.
Security Event Log Components: 5 Common Elements
Every security event log contains several components that simplify data classification, organization, and analysis. Below, you can find descriptions of each component.
Event ID
Event ID is a unique identifier linked to every event. This component makes it easier to monitor and classify security-related occurrences. It also allows seamless organization and ranking of events for analysis and reaction.
Source
Source indicates where the event originated, such as a program, system element, or user account. This data is crucial in pinpointing where errors or security issues begin. Thus, it facilitates the assignment of responsibility for specific actions. Moreover, it helps IT teams understand the extent of security incidents.
User Account Information
User Account Information provides the user’s username, ID, and domain related to the event. It helps user-centric investigations, such as locating illegal access attempts or questionable user behavior.
Timestamp
Timestamp provides a historical framework with the date and time of the incident. With this component, users can understand the order of security occurrences. It establishes the chronology of security incidents and correlating occurrences.
Event Type
Event Type indicates whether the log is informational, warning, success, or failure. It helps classify events based on their importance and level of severity. Understanding the type of event that has occurred is crucial for security analysis and monitoring.
The following section will address modern strategies organizations could use to prevent potential threats proactively.
Modern Approaches to Consider When Handling Security Event Logs
With the proper approach, businesses can leverage security event logs to boost security. Here are some of the modern approaches to consider with these logs:
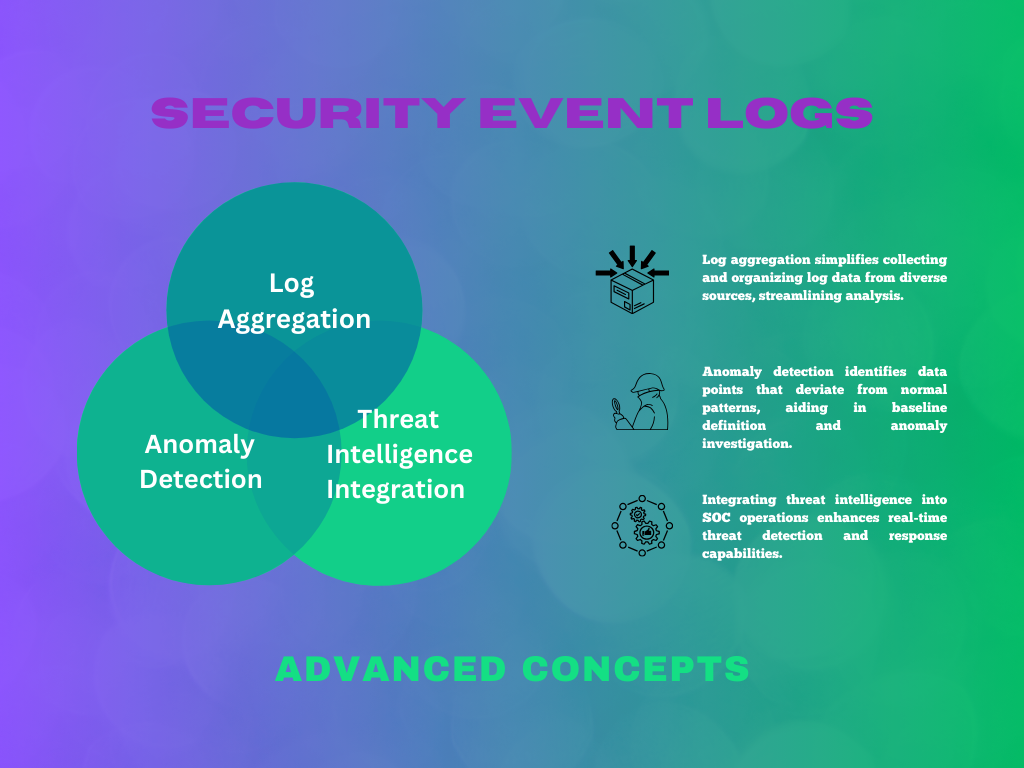
Log Aggregation
Log aggregation involves collecting and storing logs from different sources in one location. This approach gives you a comprehensive view of your IT infrastructure’s security events. With this data, you can simplify your system’s security monitoring and investigation.
With a centralized repository, every analysis, correlation, and visualization takes place in one location. This approach usually requires platforms such as Security Information and Event Management (SIEM) systems.
Anomaly Detection
Anomaly detection is locating deviations from a system or network behavior. With this algorithm, you can examine patterns and trends in security event logs. This method helps identify unexpected actions that can signal security vulnerability.
Security teams can detect new risks and security breaches using anomaly detection. Thus, you can pick up things that conventional rule-based detection techniques can miss. These are only a few factors that set anomaly detection apart from traditional monitoring.
Threat Intelligence Integration
Threat intelligence integration involves adding external threat intelligence to security event log analysis. These data provide valuable information about known threats, including:
- Indicators of compromise (IOCs)
- Malware signatures
- Tactics, techniques, and procedures (TTPs) used by threat actors
With this feature, organizations can enhance their security incident detection and response capability. This proactive approach helps security teams prevent threats and protect their systems and data.
Security event logs have become vital to safeguarding businesses from cybercriminals and other potential threats. Learn more about the benefits these logs can offer your teams and organizations.
Definition:
Security Information and Event Management, or SIEM, helps businesses manage and defend their IT infrastructure against cyberattacks by offering centralized security monitoring, real-time threat detection, and response capabilities.
Importance of Security Event Logs in Enterprises
Log files are crucial for post-error investigations to identify the reasons behind errors or breaches. Moreover, they offer up-to-date data on system activity. This feature helps identify problems and discern between deliberate and unintentional breaches.
Log file analysis can help cybersecurity admins optimize network security measures based on observed breach attempts. Moreover, this practice helps control resource access. Below are other benefits and importance of security event logs:
Enhanced Visibility
Security event logs provide comprehensive insight into a system’s or network’s internal operations. With these logs, security professionals can effectively identify and assess potential threats.
Forensic Analysis
Since logs show a timeline of events, they act as a historical record of security incidents. This data helps investigators reconstruct the attacker’s plan for a thorough forensic analysis.
Proactive Defense
Event logs enable businesses to defend against cyberattacks proactively. With these logs, IT teams can detect and fix vulnerabilities before they start affecting the system. This capability strengthens their overall security posture.
Businesses also use these logs to protect sensitive data and identify security management processes that need improvement. This capability is possible with solid logging and monitoring procedures and careful trend analysis.
Importance and Purpose
Security event logging involves analyzing electronic audit logs for unauthorized security-related activity on systems managing sensitive data. It facilitates the practical identification and handling of recorded occurrences.
Moreover, clients can effectively sift through system and audit logs with security event logging and monitoring. This way, they retain only the relevant records for analysis and retention. Using careful trend analysis guarantees improved security management and critical data protection.
Security monitoring helps safeguard sensitive data by streamlining log analysis and concentrating on pertinent records. It also allows enterprises to identify security program enhancements through trend analysis.
Conclusion
Security event logs are essential in today’s cyber threat environment, where breaches are rampant and significant. These logs provide businesses with real-time data that enables them to identify and minimize threats quickly. For over 90% of enterprises investing in big data, adopting robust logging procedures is essential to surviving in the modern digital age.
These records are essential resources for preserving network and computer security. Organizations may effectively monitor for threats, discover breaches, and verify compliance with security standards by using the information offered by these logs.
FAQS on Security Event Logs
What are logs and events?
Logs provide a thorough record of system actions and problems, which is helpful in troubleshooting and root cause analysis. Meanwhile, events enable insightful product analytics by revealing information about user behavior and application performance.
What are security events?
Security events are network occurrences that may signal potential breaches.
What are the three types of logs available through the Event Viewer?
Event Viewer shows the following types of event logs: Information, Warning, Error, Success Audit (Security Log), and Failure Audit.








