Cloud adoption is driving business innovation, but it also increases the risk of cyberattacks. Almost 83% of organizations have faced a cloud breach, with each incident costing about $4.88 million. The flexibility that helps businesses grow also puts essential assets at risk.
As workloads shift between platforms, mistakes in setup, weak identity controls, and insecure APIs create new risks. Since 82% of breaches involve cloud-stored data, having clear visibility and consistent controls is now just as important as old perimeter defenses.
Want Faster, Safer, More Actionable Root Cause Analysis?
With Edge Delta’s out-of-the-box AI agent for SRE, teams get clearer context on the alerts that matter and more confidence in the overall health and performance of their apps.
Learn MoreThis guide examines the top cloud security threats of 2025 and their impact on modern infrastructure.
| Key Takeaways • Misconfigurations cause 99% of cloud security failures, and they are often due to human error and inconsistent controls. • The average breach cost has climbed to about $4.88 million, with multi-cloud breaches even higher. • 82% of breaches involve cloud-stored data, highlighting the importance of visibility and encryption. • Zero Trust and MFA can cut breaches by up to 80%, reducing impact and speeding recovery. • Ransomware cloud attacks rose 126% year over year, with average recovery costs exceeding $5 million. • Supply chain attacks take an average of 267 days to detect and contain, posing long-term exposure risks. • Organizations face 1,876 cyberattacks weekly, led by ransomware and API exploits. |
The Cloud Security Threat Landscape in 2025
Cloud computing continues to power digital transformation, but it also reshapes the risk landscape. Global cloud spending is expected to reach more than $723.4 billion as organizations move toward hybrid and multi-cloud setups.
This fast growth encourages innovation but also gives attackers more ways to get in, so organizations need better visibility and control.
Current State and Statistics
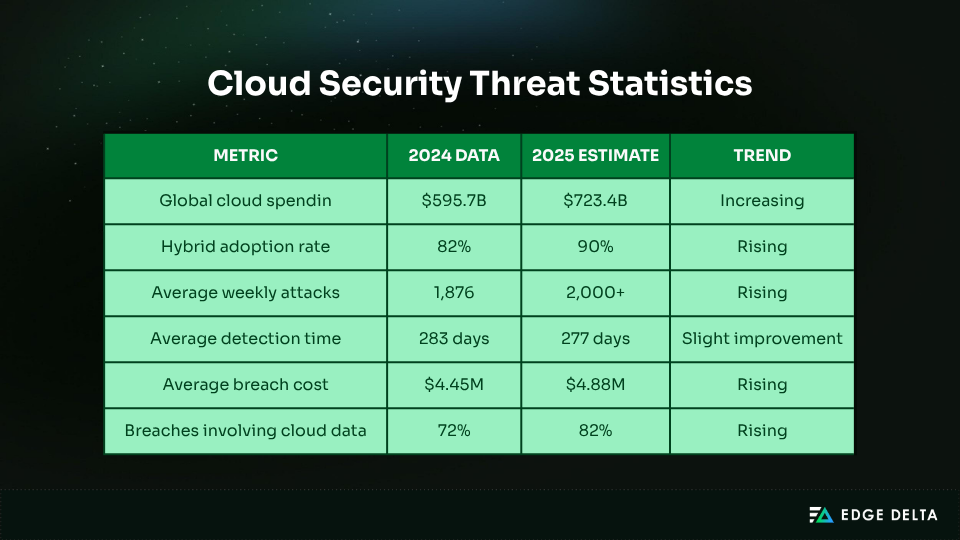
Cloud breaches are on the rise, indicating that managing risks is becoming harder as cloud use grows. There are now more than 1,870 cyberattacks each week on average, and ransomware attacks have increased as more organizations move to the cloud.
Detection remains a persistent challenge. Many organizations take 283 days to identify a compromise, giving attackers time to move freely through systems.
The financial toll is rising as well, with average breach costs approaching $4.4 million and even higher in multi-cloud settings. Most breaches involve cloud-stored data and are linked to:
- Misconfigurations and weak access control
- Inconsistent monitoring and visibility gaps
- Poor separation between cloud environments
Major incidents like the Change Healthcare breach and the National Public Data exposure show how quickly mistakes can lead to huge data leaks. These cases highlight that a lack of visibility remains a major weakness in cloud security.
Why Cloud Environments Are Targeted
Cloud environments are prime targets because they hold valuable data in complex, interconnected systems. Roughly 9% of publicly cloud storage contains sensitive data, and nearly all of it is highly confidential.
Many exposures result from misconfigurations, which cause about 23% of cloud security issues and are often due to human error. Attackers swiftly take advantage of blind spots that appear when businesses spread across several cloud platforms.“
Several factors make cloud infrastructures especially appealing:
- The expansion of remote access has increased opportunities for attacks.
- AI-driven threats have automated credential theft and scanning.
- Limited visibility across platforms allows intrusions to go unnoticed.
The effects go beyond downtime. About 86% of companies experience operational disruptions, 70% of customers stop buying from affected brands, and many organizations also face compliance fines.
In response, organizations are boosting security budgets to strengthen identity management, visibility, and incident response.
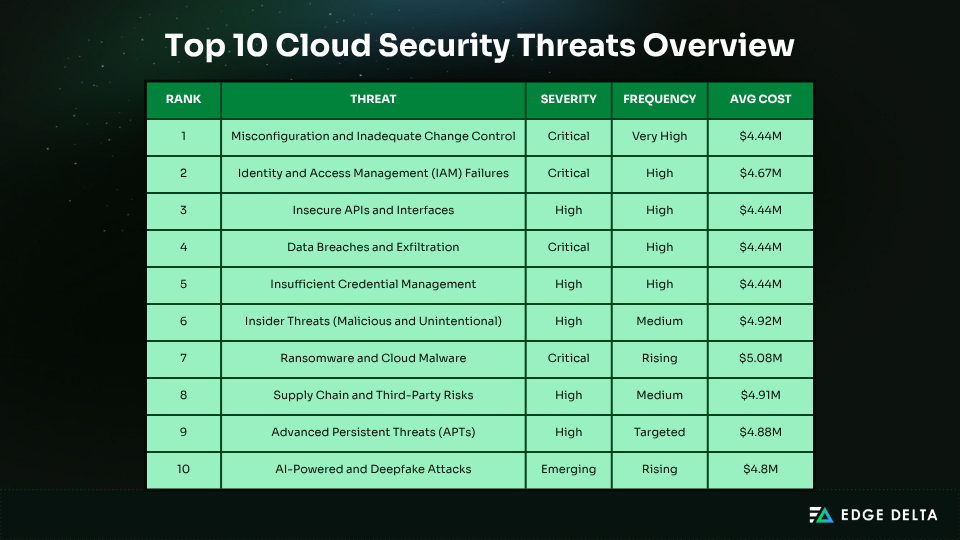
Top 10 Cloud Security Threats for 2025
Cloud environments now support most digital operations, but as they get more complex, attackers find more ways in.
Weak configurations, exposed interfaces, and unmanaged access controls continue to drive most cloud incidents. Even small mistakes can result in significant security flaws as companies grow across several platforms.
Below are the top 10 biggest cloud security threats for 2025:
1. Misconfigurations and Inadequate Change Control
Misconfiguration remains the leading cause of cloud security breaches, often exposing sensitive data or enabling unauthorized access. Almost all failures (99%) are due to customer misconfiguration, highlighting the importance of adhering to strict configuration practices.
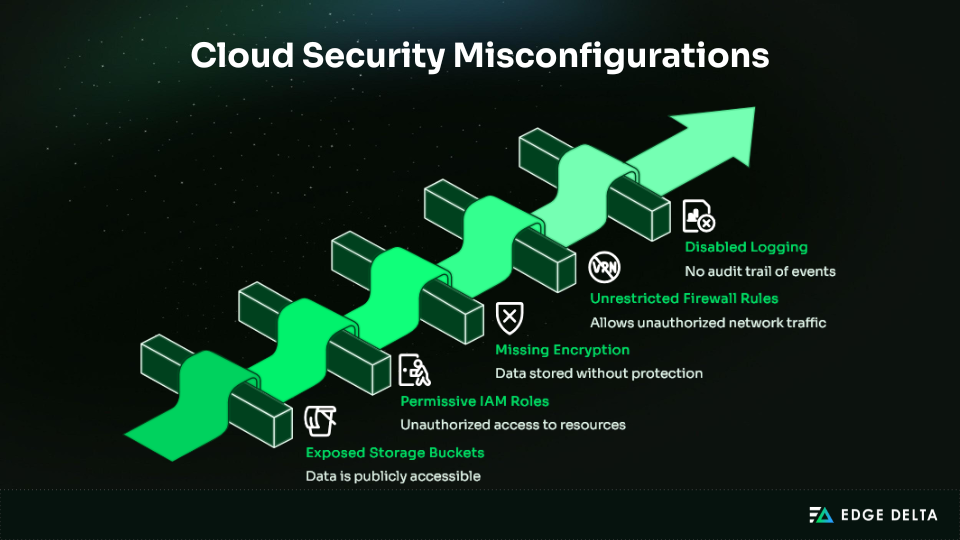
In 2025, 74% of organizations had publicly exposed storage containing sensitive data, making this one of the most common and dangerous mistakes. High-profile breaches like Toyota’s 2023 exposure of 260,000 customer records and Capital One’s 100 million–record leak reveal how small errors can have major consequences.
To prevent these incidents, companies should use automated tools to scan configurations, deploy CSPM solutions, and regularly check for changes that could weaken security.
2. Identity and Access Management (IAM) Failures
Weak identity controls remain one of the most exploited vulnerabilities in the cloud. About 35% of incidents involve the abuse of legitimate accounts, and 80% of breaches stem from compromised privileged credentials.
Once attackers gain valid access, they can move through systems unnoticed and extract sensitive data. Common weaknesses include:
- Weak passwords and missing MFA
- Excessive permissions or privilege creep
- Orphaned accounts left active
- Poor monitoring of admin and service accounts
These gaps make it much easier for attackers to impersonate trusted users and bypass standard defenses. Regular IAM checks, strong MFA, and careful review of user privileges are key to fixing these issues.
3. Insecure APIs and Interfaces
APIs connect core cloud services, making them prime targets. About 92% of organizations experienced an API-related security incident, and most lacked complete visibility into what their APIs exposed. Even one breached API can expose multiple systems.
Here are the common API security vulnerabilities:
- Weak or missing authentication controls
- No rate limiting or throttling
- Poor input validation
- Broken object-level authorization
- Excessive data exposure
- Lack of encryption in transit
To protect APIs, organizations need to identify all their APIs, test them regularly, and monitor their use to catch problems before they escalate into major breaches.
4. Data Breaches and Exfiltration
Data breaches continue to be the most damaging consequence of cloud insecurity. An alarming 82% of breaches now involve data stored in the cloud, and more than half of these incidents expose personal or financial information.
Each compromised record costs $165, which has a significant financial impact. Furthermore, 60% of malware downloads come from cloud apps, indicating that attackers are increasingly taking advantage of reliable platforms.
Most breaches can be traced back to recurring vulnerabilities that attackers exploit.
| Vector | Typical Weakness |
| Misconfigured storage | Publicly accessible buckets or blobs |
| Compromised credentials | Stolen or reused logins |
| Insecure APIs | Weak authentication or authorization |
| Insider activity | Misuse or accidental disclosure |
| Weak encryption | Unprotected data in transit or at rest |
Major breaches in recent years show the cost of simple mistakes:
- Change Healthcare exposed 192.7 million patient records.
- Dell lost 49 million customer records.
- Roblox developer data was stolen in 2025.
Using strong encryption, data loss prevention tools, and ongoing monitoring are the best ways to prevent data theft. These steps help organizations find and stop breaches early.
5. Insufficient Identity, Credential, and Access Management
Cloud account hijacking has become one of the fastest-rising attack vectors in cloud environments. In 2023, account threats surged sixteenfold, and compromised credentials were responsible for 16% of breaches.
Once attackers gain access, they often remain undetected for months, quietly taking control of resources or exfiltrating sensitive data. Here are their frequent attack methods:
- Phishing campaigns target the majority of organizations.
- Credential stuffing and password spraying.
- Session hijacking and token theft.
- MFA bypass techniques.
When these attacks succeed, they often result in privilege misuse, account theft, and service disruptions that disrupt business operations.
| Impact | Result |
| Account takeover | Full control of cloud assets |
| Privilege abuse | Data theft and unauthorized access |
| Service disruption | Downtime and financial loss |
6. Insider Threats (Malicious and Unintentional)
Insider activity is often an overlooked risk in cloud security. Nearly 28% of cloud breaches involve internal users, whether through negligence, compromised accounts, or deliberate misconduct.
Insider risks remain a serious worry for 74% of firms. The substantial financial consequences are demonstrated by the average cost of a malicious insider occurrence, which is about $4.92 million.
These can be grouped into three types:
- Malicious: Intentional data theft or system sabotage
- Negligent: Accidental exposure or poor security hygiene
- Compromised: Legitimate accounts hijacked by external attackers
Privileged access monitoring, data loss prevention tools, and user behavior analytics can help organizations detect these problems before they become critical.
7. Ransomware and Malware Targeting Cloud
Ransomware remains a dangerous and rapidly evolving threat in the cloud. In early 2025, attack activity surged by 126% YoY. The damage is severe, with destructive ransomware cloud attacks now costing organizations an average of $5.08 million.
Modern campaigns increasingly target cloud backups and combine encryption with data theft. Some variants even use AI‑driven evasion techniques to bypass defenses and accelerate propagation.
Ransomware typically spreads through stolen credentials, moves through systems, and encrypts data before demanding payment. Good defenses include endpoint detection tools, watching user behavior, and keeping backups that attackers cannot change or remove.
8. Supply Chain and Third-Party Risks
Supply chain and third‑party compromises have become a major source of risk in the cloud ecosystem. They now rank as the second-most-frequent and second-most-expensive attack vector facing organizations today.
These incidents also take the longest to resolve among major attack vectors. On average, organizations required 196 days to identify (MTTI) and 71 days to contain (MTTC) such breaches, for a combined 267 days before full resolution.
Key vulnerabilities include:
- Compromised software dependencies and open-source components
- Third-party cloud integrations and managed service provider breaches
- Stolen or misused vendor access credentials
One well-known example is the MOVEit exploit, which affected about 66.4 million users and caused damages of more than $12.15 billion. It demonstrated how a single concession may affect entire industries.
To protect against these risks, organizations should track their software components, scan for risky dependencies, and regularly check their vendors for security issues. These steps help find problems before attackers do.
9. Advanced Persistent Threats (APTs)
Advanced Persistent Threats (APTs) are long‑term, highly targeted campaigns typically run by state‑sponsored or organized crime groups. In cloud environments, APTs pose a serious risk. They have been detected in about 25% of organizations and account for 43% of the most critical security breaches.
APTs are designed to infiltrate quietly and persist over time, focusing on high‑value assets. They rely on custom malware, “living‑off‑the‑land” techniques, and multi‑stage operations that can unfold over weeks or months.
Typical characteristics of APT campaigns:
- Multiple stages progression: initial access → privilege escalation → lateral movement → data exfiltration
- Custom tools and malware designed to evade detection
- Patient reconnaissance and advanced evasion strategies
Organizations should use multiple layers of defense, such as threat intelligence, analytics, and ongoing monitoring, to catch problems early.
10. AI-Powered and Deepfake Attacks
As artificial intelligence becomes part of everyday business, attackers are using it to launch faster and more convincing attacks. More than 75% of organizations struggle to keep up with AI-powered threats, and almost 90% of security leaders believe AI-based defenses are now essential.
These threats blur the line between real and fabricated communication, making detection increasingly difficult.
| AI Attack Vector | Tactics Used | Defensive Measures |
| Phishing automation | Tailored messages at scale | AI-powered email filtering and user training |
| Deepfake impersonation | Synthetic voice and video | Voice and identity authentication |
| Adaptive malware | Self-evolving attack code | Behavioral analytics and anomaly detection |
Understanding Breach Costs and Business Impact
A cloud breach causes more than just data loss. It can lead to financial strain, downtime, and damage to reputation, which can slow digital progress for years. Knowing where costs add up helps security leaders show why prevention and automation matter.
Financial Impact Breakdown
Data breaches create costs that ripple across the entire organization. These expenses typically fall into five core areas:
- Detection
- Disruption
- Recovery
- Compliance
- Customer impact
Lost business and downtime are usually the biggest costs after a breach, often accounting for more than half of total expenses.
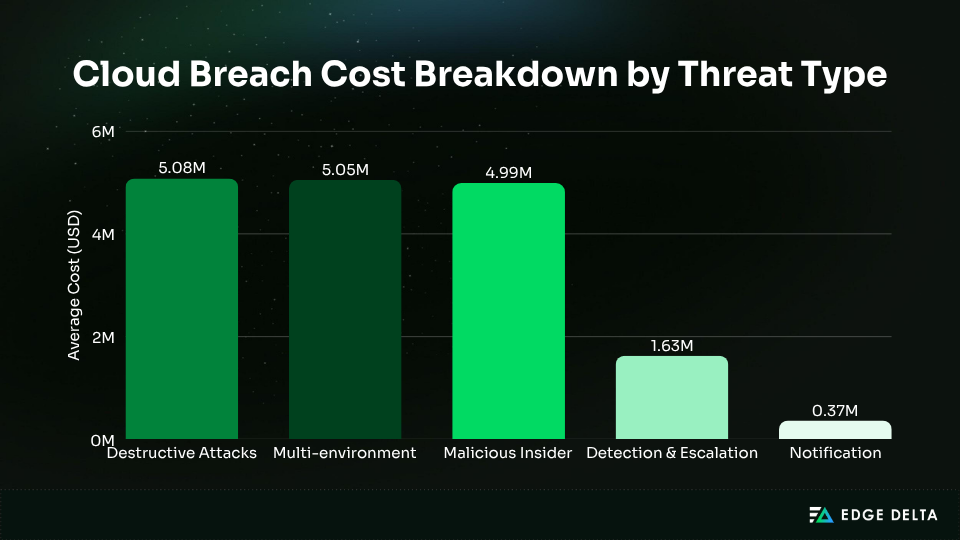
| Cost Component | Description | Business Effect |
| Detection and escalation | Incident analysis, forensics, and containment | Delays increase total breach cost significantly |
| Business disruption | Downtime, lost productivity, and system outages | Direct revenue and reputation losses |
| Post-breach recovery | Data restoration, infrastructure rebuilds | Slower return to normal operations |
| Compliance and legal | Regulatory fines, settlements, and lawsuits | Long-term financial liability |
| Customer turnover | Loss of trust and market confidence | Hardest impact to recover from |
Organizations that use AI for detection and automated response often spend less on breaches. Finding and stopping attacks faster means less downtime, fewer regulatory problems, and real savings.
Operational and Reputational Impact
A cloud breach can cause far more disruption than just financial recovery. Approximately three out of four organizations have downtime, and it frequently takes more than 100 days to recover.
Key impacts include:
- Service degradation and extended outages
- Decreased employee productivity
- Erosion of customer trust and brand reputation
- Increased regulatory and audit scrutiny
Reputation recovery takes considerably longer than system restoration. Many organizations face sustained customer churn and market hesitation long after operations resume.
| Recovery Duration | Share of Organizations |
| More than 150 days | 26% |
| 126–150 days | 24% |
| 101–125 days | 26% |
| 76–100 days | 17% |
In regulated industries, required notifications, extra oversight, and compliance fines add more pressure. Being open, communicating clearly during a crisis, and taking responsibility after an incident help restore trust and stability over time.
Cloud Security Mitigation Strategies and Best Practices
To counter new threats, cloud environment security calls for a flexible, multi-layered strategy. Multi-factor authentication (MFA), a zero-trust model, API security, and AI detection are important tactics that improve data protection and guarantee compliance.
Foundational Security Controls
A secure cloud environment starts with strong basics that protect identities, data, and systems. By focusing on these core security controls, organizations can lower the chances and impact of breaches.
These key practices are the basics of a strong cloud security plan. Each one addresses important risks and helps the organization stay strong.
1. Multi-Factor Authentication (MFA): Adds an extra credential layer; modern methods cut breaches by up to 80%.
2. Zero Trust Architecture: Adopts a “never trust, always verify” approach that prevents lateral attacker movement.
3. Least Privilege Access (PoLP): Limits permissions to essentials; reviews and just‑in‑time access reduce risks.
4. Data Encryption: Secures data in transit and at rest with strong key management.
5. Cloud Security Posture Management (CSPM): Continuously scans, detects misconfigurations, and automates remediation for compliance.
6. Infrastructure as Code (IaC): Automates deployments with version control; enforces compliance via policy‑as‑code.
7. Logging and Monitoring: Centralized logs and AI analytics enhance detection and threat hunting.
8. Incident Response Planning: Defines roles and recovery steps; testing and backups minimize downtime.
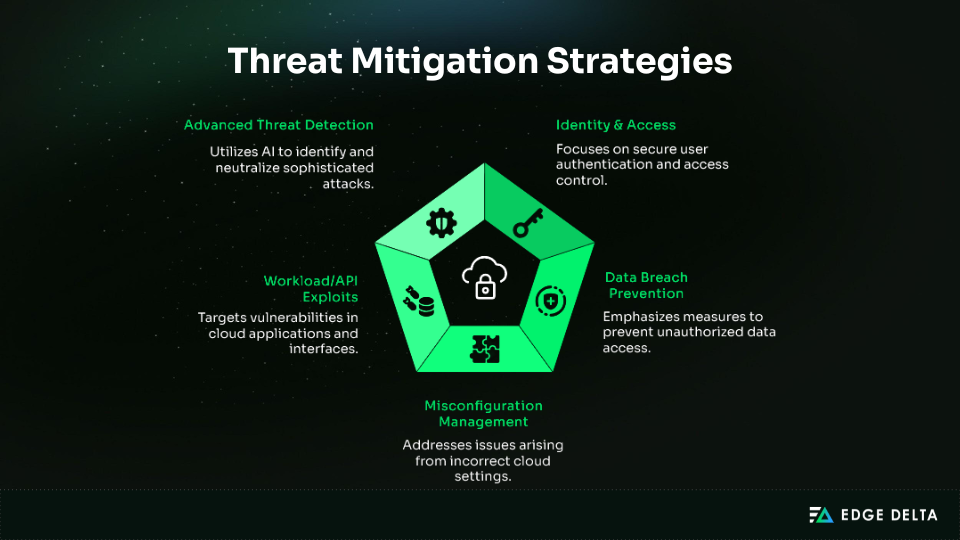
Advanced Security Practices
After setting up the basics, organizations can boost their protection with advanced, cloud-native defenses. These focus on automation, better visibility, and stronger resilience for workloads, APIs, and user identities.
1. API Security Framework: Protects critical gateways with strong authentication, rate limiting, and continuous monitoring to prevent misuse and data exposure.
2. Container and Workload Security: Secures Kubernetes and containerized apps through image scanning, runtime protection, and secrets management.
3. Cloud Access Security Broker (CASB): Extends visibility and policy enforcement across SaaS, detecting shadow IT and preventing data loss.
4. Cloud Infrastructure Entitlement Management (CIEM): Analyzes permissions and enforces least privilege automatically to reduce identity sprawl in multi‑cloud environments.
5. AI-Driven Threat Detection: Applies machine learning to spot anomalies, prioritize alerts, and automate response for faster containment.
6. In-Pipeline Masking: Automatically detects and masks PII and other sensitive data before it reaches downstream destinations.
7. Regular Security Assessments: Uses penetration tests, vulnerability scans, and audits to validate posture and compliance.
8. Employee Training and Awareness: Builds a security‑first culture through ongoing training, phishing simulations, and secure coding practices.
Security Tools and Technologies for 2025
As cloud infrastructure changes, security tools need to keep up. This section covers top platforms and solutions for 2025, organized by category and use case to help security teams match technology to their needs.
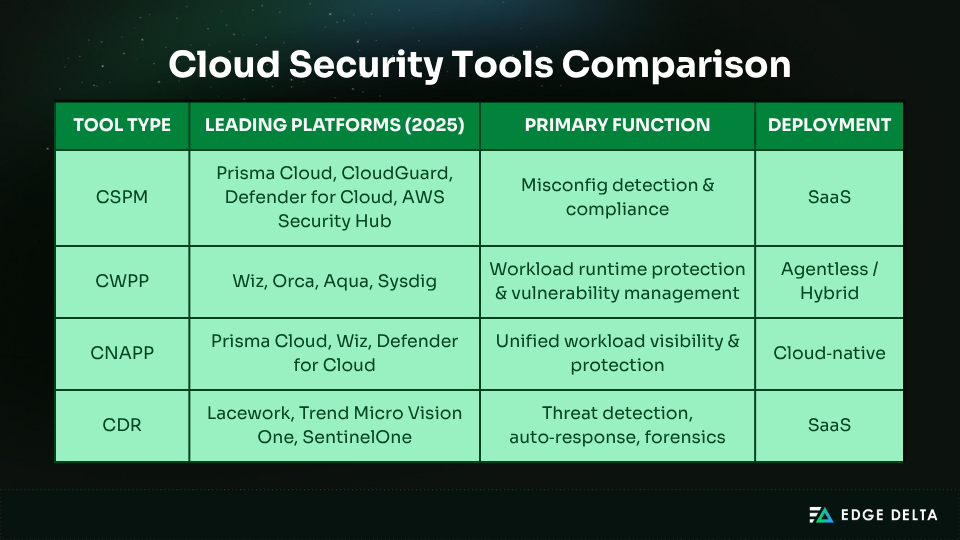
Cloud-Native Security Platforms
Specialized defenses that address risks across workloads, applications, and infrastructure are necessary in modern cloud environments. Every type of cloud-native security platform offers unique features:
- Cloud Security Posture Management (CSPM): Detects cloud misconfigurations, monitors compliance, and assesses risk.
- Examples: Prisma Cloud, CloudGuard, Microsoft Defender for Cloud
- Cloud Workload Protection Platforms (CWPP): Provides runtime protection, vulnerability management, and workload visibility.
- Examples: Wiz, Orca Security, Aqua Security
- Cloud Detection and Response (CDR): Delivers real‑time threat detection, automated response, and forensic investigation.
- Examples: Lacework, Trend Micro, SentinelOne
- Cloud‑Native Application Protection Platforms (CNAPP): Combines CSPM, CWPP, and additional controls for unified visibility and comprehensive protection
Identity & Access Security Tools
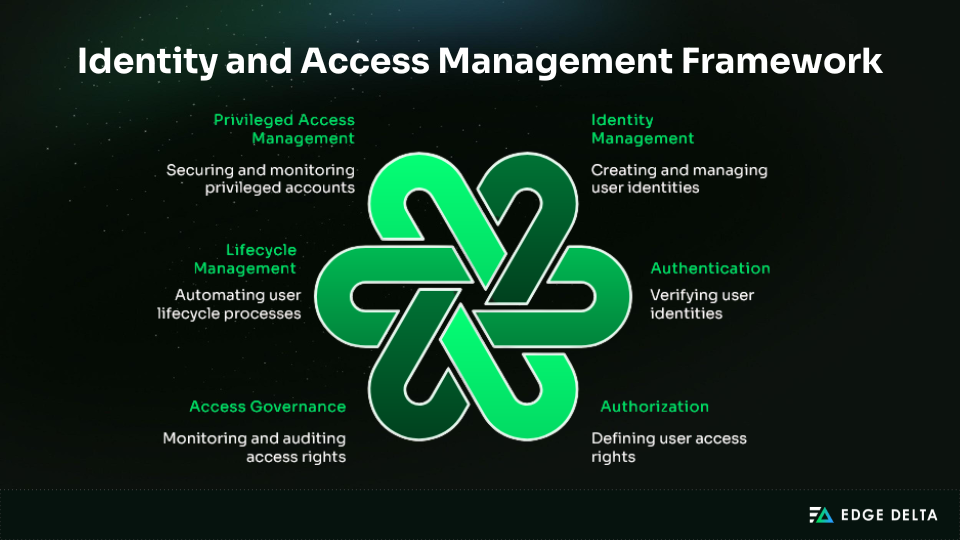
Identity security is a key part of cloud defense, including IAM, CIEM, and PAM tools. The market was worth $20 billion in 2024 and is expected to grow by about 16% each year through 2030, showing how important these tools have become.
The table below highlights the main categories, leading providers, and core functions that define today’s identity security landscape.
| Category | Leading Vendors | Core Functions |
| IAM | Microsoft Entra ID, AWS IAM Identity Center, Google Cloud Identity, Okta, Ping Identity | Authentication, authorization, identity governance |
| CIEM | CloudKnox, Ermetic, Sonrai Security | Permission analysis, least‑privilege enforcement, identity sprawl reduction |
| PAM | CyberArk, BeyondTrust, Delinea | Credential management, session recording, just‑in‑time access, secrets rotation |
These tools work together to limit credential abuse, strengthen governance, and align identity management with Zero Trust principles.
Organization-Specific Security Roadmaps
Every organization’s path to strong cloud security is different. The best plan depends on size, risk, rules, and resources. The goal is to build a program that grows over time without overloading budgets or teams.
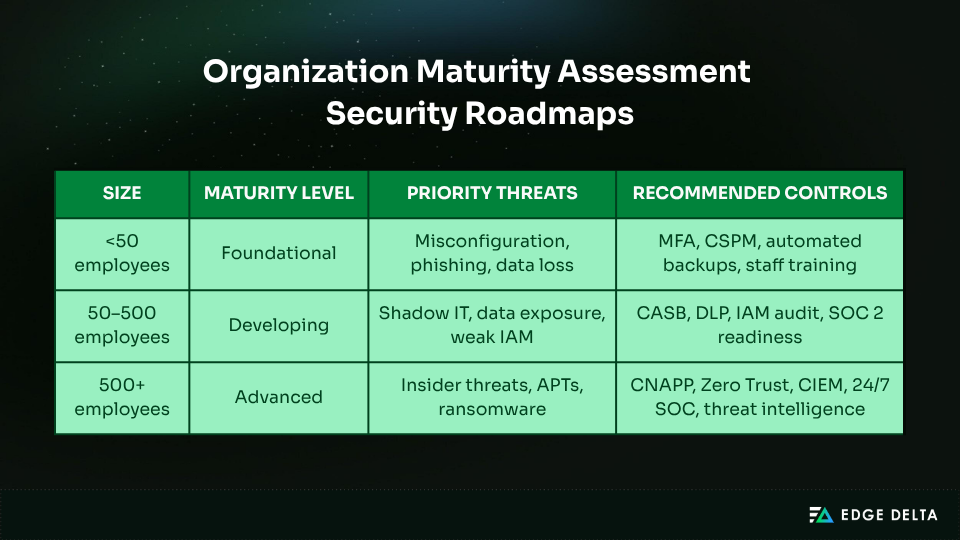
Small to Mid-Size Organizations (< 500 Employees)
For smaller teams, efficiency and automation are the foundation of security maturity. With budgets ranging from $2,000 to $8,000 per month, the goal is to deploy simple, high-impact defenses that reduce misconfiguration and credential risks.
The table below outlines how budgets, priorities, and tools progress across these stages.
| Focus Area | Recommended Actions |
| Core Protection | Enforce MFA, implement CSPM, and enable secure automated backups |
| Visibility | Use lightweight SIEM or logging for basic monitoring |
| Human Layer | Conduct employee training and phishing simulations |
As organizations grow, with budgets of $8,000–$50,000 per month, security priorities expand beyond the basics. Growth teams should:
- Control shadow IT with CASB.
- Protect sensitive data using DLP.
- Prepare for incidents with a formal response plan.
- Mature tooling by integrating CSPM + CWPP and adopting centralized IAM.
- Achieve compliance with frameworks such as SOC 2 or ISO 27001.
Enterprise Security (500+ Employees)
Large organizations need multiple layers of defense that combine visibility, automation, and strong governance.
With security budgets often exceeding $100,000 per month, these companies typically have 24/7 SOC teams, employ Zero Trust architecture, and deploy CNAPP platforms for comprehensive protection.
Strategic priorities include:
- Continuous threat hunting and CIEM for access governance
- Automated workflows validated through red‑team exercises
- Threat intelligence integration
Compliance remains a key focus, with enterprises adhering to standards, such as SOC 2 Type II, ISO 27001, HIPAA, PCI-DSS, and FedRAMP. Organizations use maturity models to track progress from basic controls to more advanced, adaptive security.
| Level | Capability Focus | Description |
| 1 – Reactive | Basic controls | Responds to incidents with minimal preparation |
| 2 – Proactive | Monitoring + detection | Establishes continuous monitoring and early detection |
| 3 – Optimized | Automation + analytics | Uses automation and analytics to predict and prevent threats |
| 4 – Adaptive | AI‑driven improvement | Employs AI for continuous learning and evolving defenses |
Industry-Specific Threat Considerations
Cloud risks vary by industry, depending on data sensitivity, regulatory requirements, and attack frequency. Each sector has its own main security and compliance priorities.
Healthcare remains the most expensive at $7.42M per breach, the highest for 14 years, though down from $9.77M in 2024. Other sectors face distinct risks shaped by regulation, data sensitivity, and the focus of attackers.
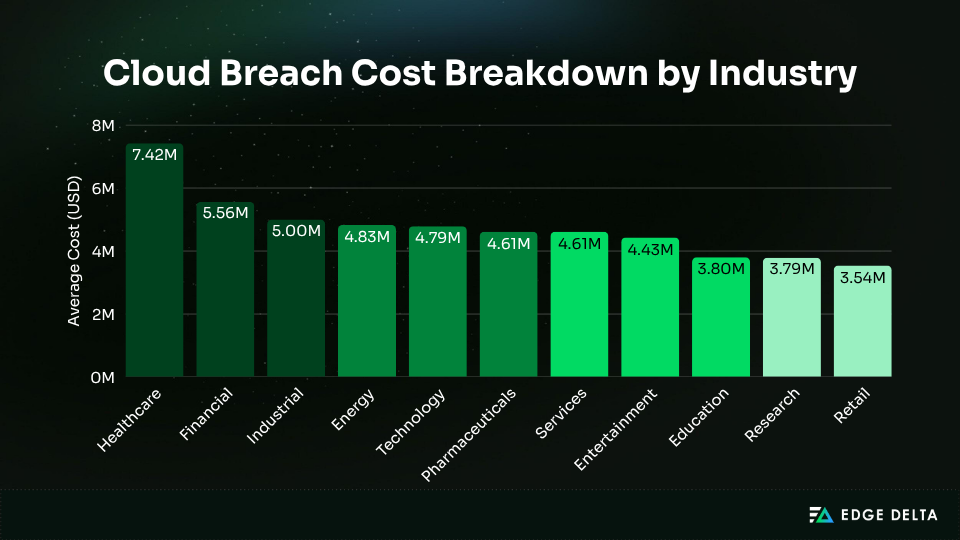
The table below highlights key risks and recommended security focus areas across industries:
| Industry | Primary Risks | Recommended Focus |
| Healthcare | Ransomware on PHI, legacy systems, HIPAA compliance gaps | Strong encryption, strict access controls, immutable backups |
| Financial Services | Fraud, PCI-DSS requirements, regulatory scrutiny, high-value targeting | Zero Trust, continuous monitoring, advanced threat intelligence |
| Retail / E‑Commerce | Payment data theft, DDoS during peak seasons, customer trust erosion | CASB, DLP, API security |
| Government / Public Sector | Nation‑state threats, outdated infrastructure, strict compliance mandates | Zero Trust, CIEM, continuous monitoring |
Emerging Threats and Future-Proofing
New risks are emerging as more businesses migrate to the cloud, necessitating proactive measures. AI attacks and quantum decryption are among the next risks that will test faith and technology.
On the 2025–2026 horizon:
- Quantum Computing: “Harvest now, decrypt later” attacks highlight the need for post-quantum cryptography and early migration planning.
- Edge Computing: Expanded IoT and 5G networks create distributed attack surfaces that require stronger endpoint security and edge data protection.
- AI Security: Around 62% of AI deployments include vulnerable components, exposing systems to model poisoning, adversarial AI, and unmanaged “shadow AI.”
- Serverless Environments: Function-level vulnerabilities and event-driven exploits remain under-monitored risks.
To stay resilient, organizations should adopt future‑proofing strategies such as:
| Strategy | Purpose |
| Cloud‑agnostic security | Avoid vendor lock‑in and maintain flexibility across platforms |
| AI‑driven detection | Enhance speed and accuracy of threat identification and response |
| Quantum‑safe encryption | Prepare for “harvest now, decrypt later” risks from quantum computing |
| DevSecOps integration | Embed security into development pipelines for continuous protection |
| Continuous threat intelligence | Stay ahead of evolving attacker tactics and vulnerabilities |
| Regular architecture reviews | Identify gaps and modernize defenses before exploitation |
Conclusion
Cloud security in 2025 demands continuous vigilance. With breaches affecting 83% of organizations and 82% of incidents tied to cloud‑stored data, the risks are undeniable. Visibility, configuration discipline, and strong identity management are now critical.
Since 99% of failures stem from misconfigurations, prevention must take priority over reaction. The average breach cost of $4.88 million underscores the value of early detection and automation.
Immediate priorities (next 90 days):
- Enable multi‑factor authentication across all accounts
- Deploy a CSPM tool to detect and remediate misconfigurations
- Audit IAM and remove excessive or orphaned privileges
- Implement centralized logging and test the incident response plan
Over the next 6–12 months, organizations should:
Adopt a Zero Trust architecture and expand AI‑driven detection. Automate response workflows, enforce continuous compliance, and conduct regular penetration testing.
By implementing these steps, organizations create a durable security posture. This approach lowers breach likelihood, enhances resilience, and safeguards long‑term trust.
Frequently Asked Questions
What are the most common cloud security threats in 2025?
Top threats include misconfigurations, weak identity controls, insecure APIs, ransomware, and supply chain attacks. These vulnerabilities expose sensitive data and disrupt operations across multi-cloud environments.
How much does a cloud security breach cost on average?
A typical cloud breach costs about $4.88 million, driven by downtime, data loss, recovery, and compliance fines. Multi-cloud breaches often exceed this average due to broader exposure.
What is the difference between CSPM, CWPP, and CNAPP?
CSPM detects misconfigurations, CWPP protects workloads at runtime, and CNAPP unifies both for full visibility, automated remediation, and protection across cloud infrastructure and identities.
How can organizations prevent cloud misconfigurations?
To identify and address risks early, use automated scanning, CSPM, and IaC. Unintentional exposure and configuration drift are avoided by least-privilege access and ongoing monitoring.
What security tools should I implement first?
Start with MFA, CSPM, encryption, and automated backups. These foundational tools provide visibility, protect data, and minimize breach impact before adding advanced detection and response capabilities.
Source List: