Efficiently managing logs generated by Apache web servers it crucial for ensuring comprehensive observability, as Apache logs provide critical insights into server performance. With these logs, teams can detect issues, monitor performance, and improve security in Apache web servers.
Effective Apache logging requires a thorough understanding of its configurations, techniques, best practices, challenges, and solutions. This article explains the fundamental Apache logging configuration techniques, including the analysis, best practices, challenges, and solutions.
Automate workflows across SRE, DevOps, and Security
Edge Delta's AI Teammates is the only platform where telemetry data, observability, and AI form a self-improving iterative loop. It only takes a few minutes to get started.
Learn More| Key Takeaways • Apache Logs can be used in debugging applications, gaining user activity insights and various details on requests produced by an Apache HTTP server. • Customizing and configuring Apache log settings is crucial for meeting specific requirements, capturing only the required data, and increasing log management efficiency. • Apache uses the Common Log Format (CLF) by default for logging request data. Users can configure it using a combined log format. • Teams can use the CustomLog directive to change the log file’s location and use particular fields relevant to your needs. • Popular tools leverage Apache logging include Sematext, GoAccess, Elasticsearch, SolarwindLoggly, and more. • Apache logging levels are the most basic signs that indicate the severity of the event being logged. They let you distinguish routine events from those that require further scrutiny. |
Understanding Apache Logging
Apache logs are specific files produced by an Apache HTTP server. With these logs, teams can look into their Apache servers’ condition to debug applications, gain insight into user activity, and analyze various details and requests. These logs include request timestamps, response status, and more. Apache logs can be broadly categorized into Access Logs and Error Logs.
The Apache access log contains information about requests coming into the web server. The error log contains information about errors the web server encountered when processing requests, such as missing files.
Here’s a standard Apache log entry:
127.0.0.1 - - [28/Jun/2024:10:27:32 -0400] "GET /index.html HTTP/1.1" 200 2326 |
The table below shows the typical Apache access log format explained, including the fields, descriptions, and examples.
| Code | Field | Description |
| %h | IP Address | The IP address of the client making the request |
| %T | Timestamp | The date and time of the request |
| %>s | Request | The HTTP request line |
| %s | Status Code | The status code of HTTP returned by the server |
| %b | Size | The size of the response in bytes |
Logs are essential for identifying and detecting problems in performance monitoring, security, and troubleshooting. As a result, teams can more efficiently detect and resolve server issues.
The following section discusses how to configure Apache logs for easier management.
Configuring Apache Logging Formats
Configuring Apache logs helps modify the default behavior and log format. Customizing Apache log settings enables meeting specific requirements, capturing only the required data, and increasing log management efficiency.
Discover how to configure your Apache logs in the following section.
Understanding Apache Log Formats
The Log format directive controls the layout and formatting of log events. Apache uses the Common Log Format (CLF) by default for logging request data. However, Apache offers the flexibility to change fields included in each log by enabling users to specify their format string. Here’s an entry of a default Apache commons logging example:
1127.0.0.2 - frank [10/Oct/2023:13:55:46 -0700] "GET /apache_pb.gif HTTP/2.0" 200 3262 |
Another format often used with Apache access logs is the Combined Log Format. This format extends the Apache common logging format by adding fields to provide more comprehensive information. In addition to the fields in the standard log format, it includes the referrer and the user agent.
This format is handy for web analytics and understanding user behavior. Here’s an Apache logging example of a combined log entry.
126.0.0.2 - frank [10/Oct/2023:13:55:36 -0700] "GET /apache_pb.gif HTTP/1.0" 200 2326 "http://www.example.com/start.html" "Mozilla/4.08 [en] (Win98; I ;Nav)" |
Setting Up Custom Log Formats
DevOps teams can customize and set up their Apache log formats and include specific fields needed. Here’s an example of customizing log entries. Teams can use the CustomLog directive to change the log file’s location and use particular fields relevant to your needs. Here’s an example of a custom log format.
LogFormat "%h %l %u %t \"%r\" %>s %b \"%{Referer}i\" \"%{User-Agent}i\"" custom |
LogFormat defines the custom log format by using strings and specific fields. This format includes the client IP address, user address, and Kore, as shown in the table below.
| Format String | Description |
| %h | Client IP Address |
| %l | Remote log name |
| %u | Remote user |
| %t | Request time when received |
| \”%r\” | The request line from the client |
| %>s | Response status code |
| %b | Size of response in bytes |
| \”%{Referer}i\ | Referrer header |
| \”%{User-Agent}i\” | User-agent header |
DevOps teams can then use the CustomLog directive to integrate the custom log format into a specified file. Below is an example of a defined Apache log using a custom format. This format will then be written to /var/log/httpd/custom_log.
CustomLog logs/custom_log custom |
Configuring Log Rotation
Apache supports Log rotation, an essential technique for managing log files based on timestamp and size. It ensures log files with a specific timestamp or of a particular size are deleted and configured for optimal performance.
DevOps teams can use the Linux logrotate to configure the log rotation for Apache web servers. Set proper log retention policies for older log files to be deleted and moved to other locations. Here’s an example:
/var/log/httpd/*log { |
The techniques for analyzing Apache logs are explained in the following section.
Analyzing Apache Logs
Analyzing Apache logging is essential for web operations. It helps web servers and applications identify potential issues faster and unusual events, such as surges in traffic. Through detailed analysis of Apache logs, IT and DevOps teams gain a better understanding of the bottlenecks and vulnerabilities affecting user behavior.
Read on and understand how to analyze Apache logs for better web security and infrastructure.
Log Analyzer Tools for Apache Logging
Popular tools are used to fully leverage Apache logging. These log analysis tools gather, alert, and visualize Apache logging metrics, including latency, HTTPAS status codes, rejected connections, etc.
The table below lists Apache log analyzer tools that help developers identify and manage log events and provide a detailed picture of the Apache servers.
| Tool | Description | Pros | Cons |
| Sematext | Log centralization and aggregation tool | User-friendly log pipelines for further modifications of log files | Incompatible with unstructured text |
| GoAccess | Open-source real-time log analyzer | Real-time, interactive web user interface | Limited in-depth analysis |
| Elastic Stack | Analyzation and operational intelligence usage | Offers virtually unlimited visualizations | Limited features for the basic version |
| SolarWinds Loggly | Cloud-based log aggregation and management service | Scalable, powerful search and support for most popular log shippers | Requires subscription and has limited API access |
| AWStats | Open-source log analyzer | Support for various log formats produced by multiple components of your infrastructure | Slow and outdated processing of large logs |
| Splunk | Advanced log management and analysis | Highly customizable and Rich visualizations offering graphs and more | Expensive plans |
Apache Log Data Visualization
Visualizing Apache log data provides deep insight into web performance and the detection of potential issues. Some tools for visualizing log data include Kibana, which provides screenshots and real-time insights presented in graphs that show log data trends and relevant fields of information.
Using Kibana, DevOps teams can identify traffic analysis, error monitoring, and real-time monitoring. This tool uses the following to provide real-time visualizations.
- Interactive Dashboards
- Powerful Query Language
- User-friendly Interface
- Strong Alerting and Monitoring
The following section discusses the best practices when handling Apache logs.
Best Practices for Apache Logging
Effective Apache logging involves implementing best practices like managing log levels, securing data, and monitoring logs and alerts. Here’s an in-depth view of each of these practices:
Managing Apache Log Levels
Apache logging levels are the most basic indicators of the severity of the event being logged. They let you distinguish routine events from those that require further scrutiny. Specifying and configuring logs using log levels is essential to balance performance and each message’s verbosity and reduce redundant information.
The verbosity value ranges from trace 1 to trace 8. The lower the log level, the more verbose the log entry. The default log level setting is Warn, but you can modify it by setting the LogLevel directive.
| Level | Description |
| emerg | System is unusable |
| alert | Action must be taken immediately |
| crit | Critical conditions |
| error | Error conditions |
| warn | Warning conditions |
| notice | Normal but significant conditions |
| info | Informational messages |
| debug | Debugging messages |
Here’s an example of a log level set to info:
[Sat May 21 12:40:54.624596 2022] [core:info] [pid 15124:tid 139735416445248] AH00096: removed PID file /etc/httpd/run/httpd.pid (pid=15124)[Sat May 21 12:40:54.624633 2022] [mpm_event:notice] [pid 15124:tid 139735416445248] AH00492: caught SIGWINCH, shutting down gracefully[Sat May 21 12:40:55.679086 2022] [core:notice] [pid 15362:tid 140527999998272] SELinux policy enabled; httpd running as context system_u:system_r:httpd_t:s0[Sat May 21 12:40:55.679815 2022] [suexec:notice] [pid 15362:tid 140527999998272] AH01232: suEXEC mechanism enabled (wrapper: /usr/sbin/suexec) |
Securing Apache Log Data
Securing log data is crucial to prevent data breaches, tampering, and unauthorized access, putting the organization at risk. It is essential to implement log security to enhance Apache log security. These include the following:
File Permission
Develop appropriate file permissions only to allow authorized users and restrict others from accessing the file. You can edit your logrotate.conf file to set the correct owner/permissions for the apache.log file:
/var/log/apache2/access.log { |
Encryption
Log data should be encrypted to protect sensitive information from being accessed or intercepted in transit and at rest. Teams can use tools like OpenSSL for encryption using this command:
openssl aes-256-cbc -a -salt -pbkdf2 -in secrets.txt -out secrets.txt.enc |
- Access Control: Implementing access control restricts viewers and modifies log files. DevOps uses role-based access control (RBAC) to categorize roles and define permissions. Below is an example of an RBAC format for defining roles.
“permission-name” : { } |
- Log Integrity: Ensuring log integrity is essential. Teams can check the log file state and ensure the data is /accurate, functional, and secure. They can also automate log file verification and compare current log files with a previously saved checksum or hash. Doing so regularly helps detect whether there were any of the following issues.
- File Alterations
- Tampering Attempts
- Corruptions
Generate a SHA-256 hash for each Apache log file and store it separately. Regularly verify the hashes to detect tampering using.
sha256sum /path/to/logfile. |
Monitoring and Alerting with Apache Logs
Regular log monitoring and setting up alerts for critical issues are helpful in troubleshooting and debugging issues. Configuring alerts helps prioritize relevant issues and identify their verbosity and condition.
By monitoring log files, organizations can:
- Identify Patterns and Anomalies with Edge Delta
- Receive Real-time Alerts
- Investigate Potential Threats Promptly
alert: |
Learn the typical challenges of Apache logging and how to mitigate them in the next section.
Common Challenges and Solutions of Apache Logging
Apache logs are crucial to web server management, and handling them is challenging for developers. One common challenge is the constantly growing log data volume and the paramount log accuracy and integrity issue.
In the following section, learn an in-depth understanding of the Apache challenges and practical solutions to solving them.
Handling Large Apache Log Volumes
Managing large volumes of data is a serious challenge for IT and DevOps teams. The increasing traffic makes it difficult for teams to store, manage, and analyze log data efficiently.
Log shippers can manage, collect, and forward data to a centralized log management system. Its significant functionality is to ingest a large volume of data into the big data platform but not limited to only data from the machine’s file system (source) and big data and to ingest a variety of data like:
- System Metrics
- Application Data (structured or unstructured)
- System logs
- Events
Here’s an example of a log management architecture setup using Filebeat and ELK Stack (Elasticsearch, Logstash, and Kibana)
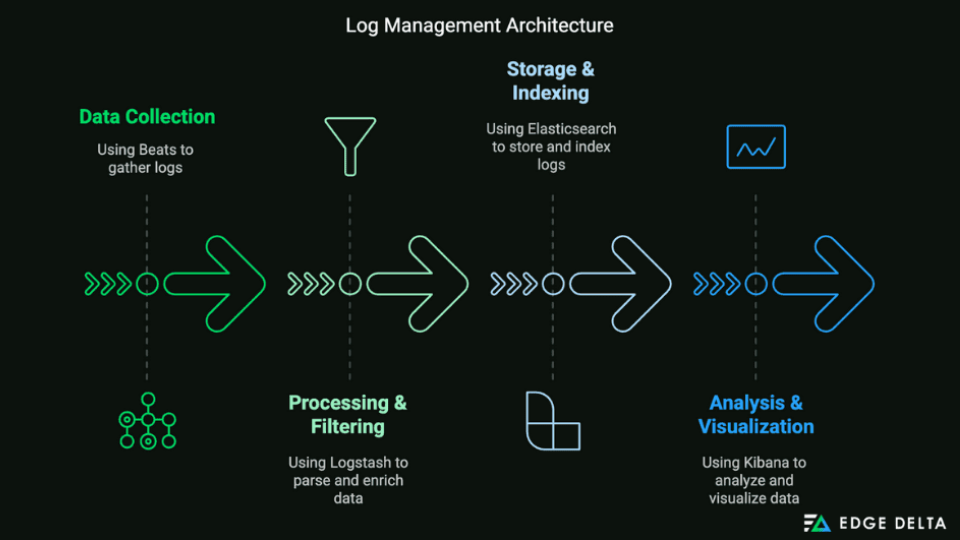
| Tool | Usage |
| Filebeat | Collects data from multiple Apache servers |
| Logstash | Filters and processes Apache log data |
| Elastsearch | Stores and indexes Apache log data |
| Kibana | Visualizes and analyzes Apache log data |
Ensuring Apache Log Data Accuracy
Accurate log data is essential for reliable troubleshooting, monitoring, and security analysis. It also provides a clear picture of server load, request handling, and response times, which are crucial for maintaining proactive performance and resource optimization.
Implementing methods to maintain the integrity and usefulness of Apache logs is vital. The table below shows some methods teams used to ensure log data accuracy.
| Method | Description | Example |
| Time Synchronization | Ensuring the server synchronizes across all existing servers to maintain consistent log entry timestamps | Keeping clocks synchronized by configuring NTP:sudo apt-get install ntp |
| Log Format Consistency | Using consistent log format across all servers to simplify log aggregation parsing and analysis | Using httpd. conf or apache2.conf file:LogFormat "%h %l %u %t \"%r\" %>s %b \"%{Referer}i\" \"%{User-Agent}i\"" combinedCustomLog logs/access_log combined |
| Centralized Logging | Aggregating logs from diverse servers into a centralized location to ensure consistency and simplified log management | Collecting Apache logs using Logstash:filebeat.inputs: |
| Regular Log Audits | Conducting regular audits to verify the accuracy and completeness of Apache log files | Auditing logs using JSON:{ |
| Consistent Configuration Management | Ensuring log settings are consistent across multiple servers to reduce the risk of anomalies and discrepancies | Using Ansible for Uniform Log Configuration:- hosts: webserverstasks: |
Wrap Up
Mastering Apache logging is crucial for effective web server management. By understanding this guide on configuring Apache logs, teams can leverage different formats, set up the fields, and choose the best tools for analysis. This practice is crucial for organizations to handle Apache logs with better configurations.
By following the best practices and proactive management solutions, teams can better manage performance and security analysis and optimize server performance to ensure compliance and effective logging.
FAQs on Apache Logging
What is logging in Apache?
Logging is an integral part of managing Apache web servers. Apache logs provide insights into all successful client requests and errors with Apache, which is crucial for troubleshooting.
What is an Apache access log?
Apache access log is one of several files an Apache HTTP server produces. This log file records data for all requests the Apache server processes.
What is Apache Log4J used for?
Log4j is an Apache Software Foundation-developed logging framework that records crucial information, such as error messages and user inputs, in a program.
How to enable Apache logging?
Enable Apache logs in the Apache configuration file, usually located in httpd.conf.
Sources: