When using traditional observability platforms, it can be difficult for Security teams to identify unexpected or suspicious behavior. Two core challenges cause this issue.
First, financial constraints make it difficult for teams to ingest 100% of the logs their systems generate. Instead, they often practice sampling or filtering – in some cases, they may neglect datasets altogether. By nature, these practices limit visibility into potential anomalies.
Want Faster, Safer, More Actionable Root Cause Analysis?
With Edge Delta’s out-of-the-box AI agent for SRE, teams get clearer context on the alerts that matter and more confidence in the overall health and performance of their apps.
Learn MoreSecond, depending on the feature set of the platform in use, detecting issues in real-time can require significant manual operations. In some cases, Security teams are flooded with false positives and alerts to investigate. In others, they must define regexes and configure static queries and alerts to spot specific patterns and statistical deviations. Given that new threats always appear, this workflow requires engineers to predict patterns that could represent any and all security breaches – an impossible task.
This latter challenge recently impacted one of our customers – a managed services provider that hosts websites on behalf of thousands of customers worldwide – during a potential breach.
Detecting a Brute-Force Attack with No Manual Intervention
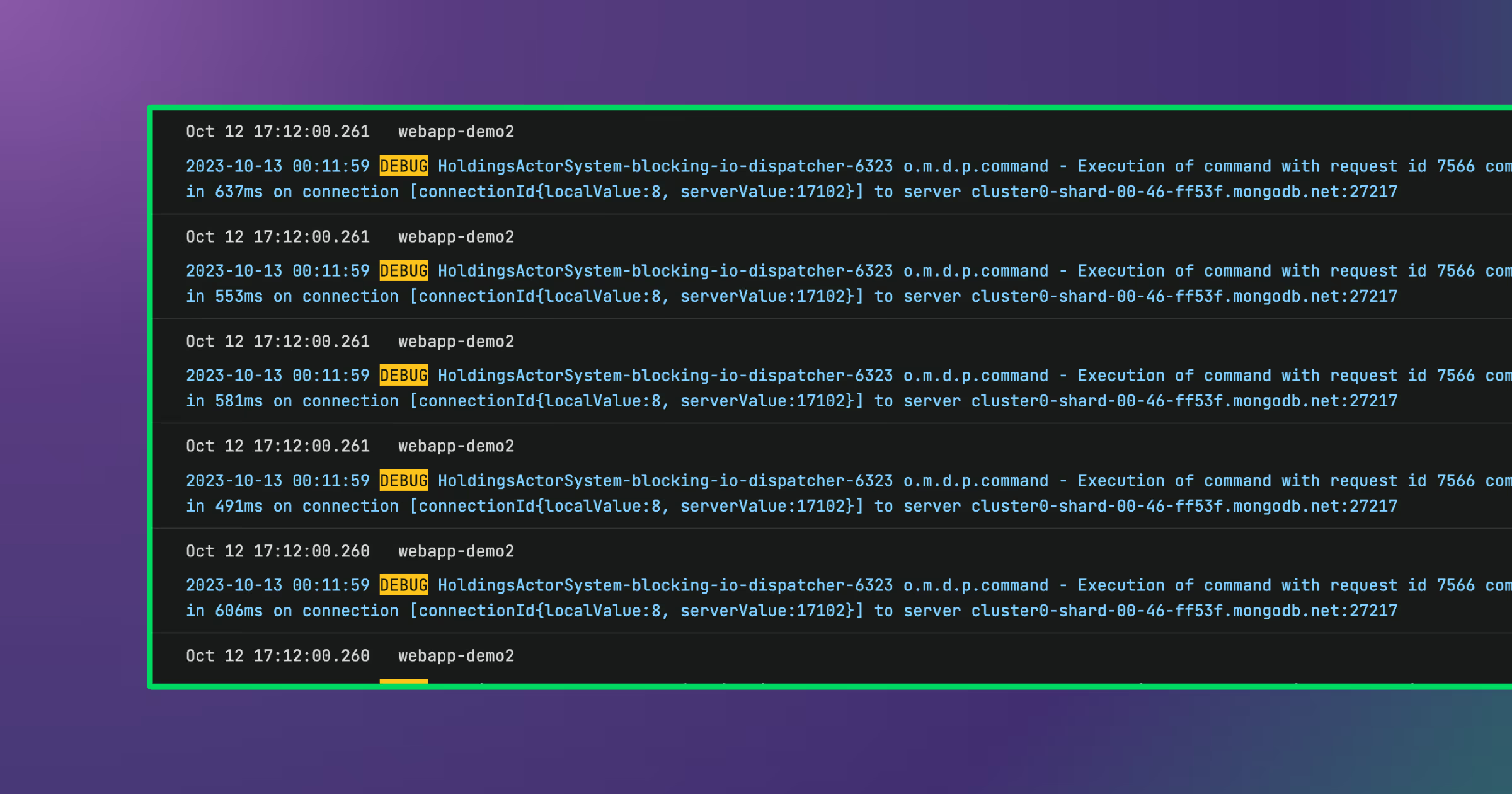
On November 20, this provider experienced over 50 unsuccessful attempts to gain root access to an SSH server in one of their customer’s environments. This incident was unexpected for two reasons: the sheer volume of attempts and the fact they came from several different IP addresses. The root cause of this incident could have been any number of vulnerabilities. For example, a misconfiguration or exposed customer credentials.
The provider uses Sumo Logic for dashboarding and alerting. But, since they had never seen this exact pattern before, they understandably had not defined a regex to detect the outlier and trigger an alert.
However, the company also uses Edge Delta to analyze all of their logs as they’re generated at the source – before they’re centralized in Sumo Logic. Edge Delta provides several features that automate observability, eliminating the toil associated with detecting anomalies in real-time.
In this instance, Edge Delta’s Pattern Analytics identified several new patterns within the loglines, communicating the potential brute-force attack. Spotting these events required no manual intervention or pre-configuration:
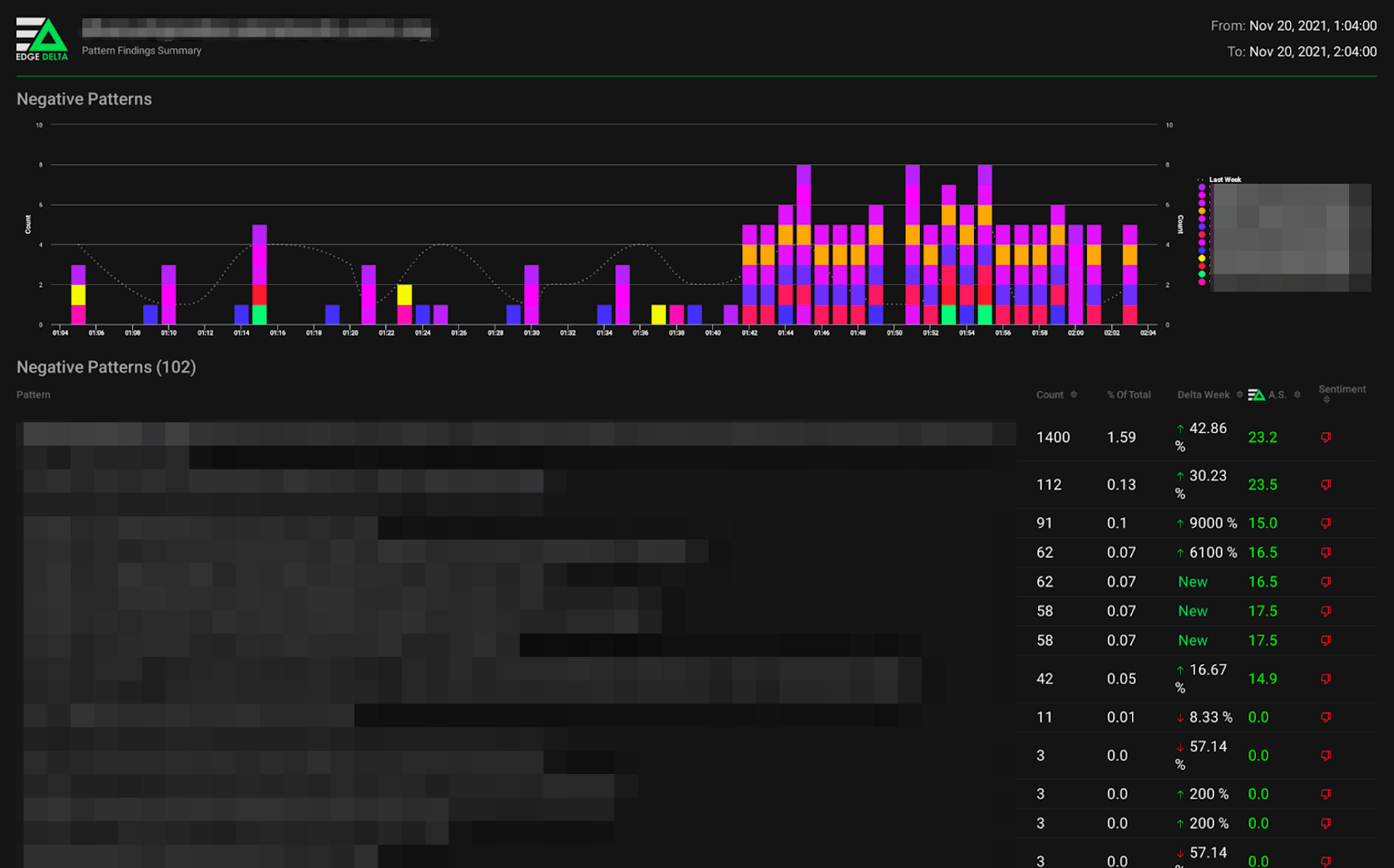
At the same time, Edge Delta uses machine learning to understand the sentiment of the patterns – in this case, negative given the nature and volume of the attempts – and captures how many times each happened.
Three of the patterns detected had never been captured before. Nonetheless, Edge Delta not only spotted the behavior but proactively identified them as troublesome. In tandem, Anomaly Detection assigned a confidence score, indicating the likelihood of anomalous behavior.
Here, the massive delta of activity of these patterns and their negative sentiment triggered an anomaly. When this happens, Edge Delta automatically begins a circular buffer to capture full-fidelity logs before, during, and after the incident. (By default, Edge Delta captures 15 minutes of logs both before and after the event, however, you can configure it to capture any timeframe.)
From there, the provider created a ticket with their Information Security team and provided the data to perform an investigation of the event.
Strengthening Your Real-Time Security Posture with Edge Delta
Security threats continue to grow and evolve. However, many of the tools traditionally used to detect and remediate these threats have remained largely unchanged. Those that have matured with the security landscape have failed to do so without false positives and alert fatigue.
The team at Edge Delta understands that this status quo isn’t good enough. Additionally, the onus shouldn’t fall on engineers to react to every potential vulnerability 100% of the time. That’s why Edge Delta automates observability – providing features like pattern analysis and machine learning at the source to detect potential threats and equip Security teams with the information they need to keep customers protected.
In this instance, the services provider was able to augment their Sumo Logic deployment without any manual configuration. They simply ingested the logs into Edge Delta to gain the insights they needed to prevent the potential breach. Use cases like this are the reason Edge Delta is becoming an essential platform to strengthen your real-time security posture.