Log data refers to data that records information on events that occur within a digital system, in an application, or on a network device or endpoint. In modern applications, log data provides insights for IT and DevOps teams to determine real-time system bottlenecks and issues, particularly through in-depth log analysis.
Implementing effective log management with real-time log analysis capabilities and alert functionality is crucial to leveraging log data’s full potential. Logs enable teams to access helpful insights covering system performance, user activity, security events, and much more.
Want Faster, Safer, More Actionable Root Cause Analysis?
With Edge Delta’s out-of-the-box AI agent for SRE, teams get clearer context on the alerts that matter and more confidence in the overall health and performance of their apps.
Learn MoreThis article discusses log data, its benefits, and the best practices to implement for better log management.
|
Key Takeaways
|
Understanding Log Data
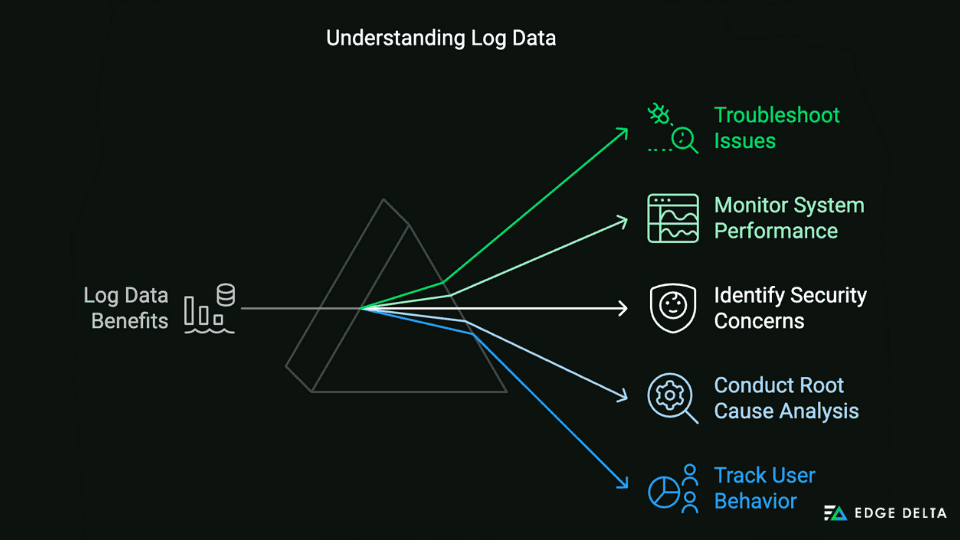
In modern IT operations, log data is critical in monitoring and debugging. Software programs and systems generate log files containing information about the application, user device, time, IP address, and more. These logs obtain timestamps and event details that DevOps and Security teams commonly use for the following:
- Troubleshooting Issues.
- Monitoring System Performance.
- Identifying Security Concerns.
- Conducting Root Cause Analysis.
- Tracking User Behavior.
For instance, Security teams may leverage Security Information and Event Management (SIEM) solutions to secure the organization’s network by monitoring log data records across devices and applications. As shown in the table below, SIEM solutions must collect and analyze various types of log data to evaluate the network’s security posture.
| Types of Log Data | Description |
| Perimeter Device Logs | Archived data for monitoring and regulating traffic to and from the network, such as firewalls, virtual private networks (VPNs), intrusion detection systems (IDSs) |
| Windows Event Logs | Record of everything that happens on a Windows system, including web application, system, directory, DNS, security, and more. |
| Endpoint Logs | Data of devices connected to the system network that communicates with other devices such as desktops, laptops, smartphones, and printers |
| Application Logs | Records of multiple applications, which include web server applications, databases, and other in-house apps |
| Proxy Logs | Records of all user activity (events/logs/etc.) in all protected applications associated with inline access control and DLP policies |
Organizations need a robust log management system that can cope with their various structured and unstructured formats to leverage their log data fully. Some logs are already structured, like the one below:
{
"timestamp": "2023-06-30T12:34:56Z",
"level": "INFO",
"message": "User login successful",
"userID": "12345",
"userIP": "192.168.1.1",
"sessionID": "abcd3456",
}
Which adheres to this schema defined below:
| Field | Description |
| Timestamp | The time the log entry was created |
| Level | The severity of the log message |
| Message | The content of the log entry |
| UserID | Identifier for the user associated with the log |
| Source IP | IP address where the request was generated |
| SessionID | User’s session identifier |
But not all logs come in this exact same shape and format. Proper log analysis and log data benefits only arrive when different data sources are correlated to paint a full picture of environment health and user activity.
The following section discusses the benefits of log data with actual examples.
Benefits of Log Data With Examples
Properly configured log data provides many advantages to IT and DevOps teams. With it, they can maintain their entire infrastructure, responds to potential errors, and provides critical insights and trends. Additionally, log data monitoring improves performance, security, operational efficiency, and resource optimization.
Read on and learn the benefits of working with log data in the following section.
1. Enhances Troubleshooting and Debugging
Organizations can access insightful information from collected log data and get real-time updates on errors and performance, minimizing downtime. Log data software provides detailed records of application events and errors that can be used to trace the root cause of an application error.
Error logs can be helpful in troubleshooting and debugging. These logs provide detailed insights and severity levels of the problem or error and help developers figure out how to fix it. Here’s an example of a troubleshooting scenario.
2023-06-30T12:34:56Z ERROR Failed to connect to database: ConnectionTimeout2023-06-30T12:34:56Z ERROR Failed to connect to database: ConnectionTimeout2023-06-30T12:35:00Z INFO Retrying database connection2023-06-30T12:35:05Z INFO Database connection successful2023-06-30T12:35:10Z WARN Slow query detected: SELECT * FROM users WHERE last_login > '2023-06-01'
With the information from these logs, it’s clear there’s a potential issue with connecting into some system database, along with some issue regarding its performance.
2. Improves Performance Monitoring
Log data is critical for monitoring application performance and health on the front and back end. Applications hosted on the cloud are highly distributed, and logging and monitoring tools can help organizations connect the dots across the application stack.
These logs can quickly troubleshoot performance issues and remediate security threats in real time. Log data also help teams:
- Spot issues before they affect consumers.
- Monitor app components like servers, databases, and more.
- Provide alerts and a dashboard to remove application bottlenecks.
Here are some sample API logs with key information about response time and request success rate:
2023-06-30T12:34:56Z INFO API response time: 120ms2023-06-30T12:35:00Z INFO API response time: 115ms2023-06-30T12:35:05Z INFO API response time: 130ms2023-06-30T12:35:10Z ERROR API request failed: Timeout 11:33 AM
From logs like these, there are a number of valuable metrics teams can derive, including the ones shown below in the table:
| Metric | Description |
| Response Time | Time taken to respond to API requests |
| Error Rate | Frequency of errors occurring |
| Throughput | Number of requests handled per second |
Application logs obtain ongoing activities within the system and record almost everything from errors to significant events, which enables monitoring to detect potential issues. Here’s another sample application log record:
02-AUG-2024 17:38:48 * (CONNECT_DATA=(SERVICE_NAME=dev12c) (CID=(PROGRAM=sqlplus)(HOST=oralinux1)(USER=oracle))) * (ADDRESS=(PROTOCOL=tcp)(HOST=192.168.2.121)(PORT=21165)) * establish * dev12c * 0
The application log above records the following essential information:
- Date and time when the database server acquired the request
- Information on the user
- Host computer details from which the request originated
- IP address and port number
3. Ensures Security and Compliance
Compliance and safety issues are key reasons to conduct log analysis. Log data analysis helps detect data leaks, unauthorized access attempts, and other suspicious activities.
Another vital use of a detailed log file analysis is to help organizations conduct forensic research and analysis and meet compliance and audit requirements concerning investigations. Here’s a security log entry example using the different log severity levels:
2024-06-30T12:34:56Z WARN Unsuccessful login attempt for user: admin from IP:10.0.0.12024-06-30T12:35:00Z INFO User 'admin' logged in successfully from IP:10.0.0.12024-06-30T12:35:05Z ERROR Multiple failed login attempts detected from IP:10.0.0.22024-06-30T12:35:10Z ALERT Brute force attack detected on user 'admin'
4. Provides User Behavior Analysis
Using the user’s log dataset, DevOps teams can gain crucial insight into how users use their applications, allowing them to deliver a higher-quality user experience. This data can also help teams recognize and resolve incidents of application abuse.
Below is an example of a user activity log accessing and navigating the page.
2023-06-30T12:34:56Z INFO User '12345' accessed 'homepage' from IP:192.168.1.22023-06-30T12:35:00Z INFO User '12345' clicked on 'product page'2023-06-30T12:35:05Z INFO User '12345' added item 'SKU1234' to cart2023-06-30T12:35:10Z INFO User '12345' completed checkout for order 'order98765'
Here’s a table summarizing the details of the user log activity.
| Metric | Description |
| Page Views | Number of pages viewed by users |
| Session Duration | Time users spend on the application |
| Click-Through Rate | Frequency of user interactions |
5. Facilitates Resource Optimization
Troubleshooting problems is a great example of how log data is beneficial, as they can be used to optimize resource usage, reduce costs, and identify issues that occur. By monitoring resource utilization, response times, and application behavior through logs, organizations can:
- Identify Opportunities for Optimization
- Resource Allocation Improvements
- Make Better Decisions on Scaling
Here are some examples of resource log usage.
2023-06-30T12:34:56Z INFO Memory usage: 75%, CPU usage: 60%, Disk usage: 50%2023-06-30T12:35:10Z WARN Memory usage high: 90%, Consider scaling up
6. Offers Predictive Maintenance
Predictive maintenance through machine learning and other advanced tools uses historical and real-time log data from diverse parts of your operation to predict problems before they happen. Analyzing these data allows potential issues to be predicted and prevented, leading to a more reliable operation, improved customer service quality, and reduced additional costs.
2023-06-30T12:34:56Z WARN Disk space usage at 90%, nearing capacity2023-06-30T12:35:00Z ERROR High error rate detected in disk reads2023-06-30T12:35:05Z INFO Scheduled maintenance task initiated2023-06-30T12:35:10Z INFO Disk cleanup completed, current usage: 70%
| Metric | Description |
| Disk Space Usage | Current usage of disk space |
| Error Rates | Frequency of errors that might predict failures |
| Scheduled Maintenance | Ongoing projects with an expected time of completion |
| Disk Clean Up | Designed to free up log database |
7. Strengthens Audit and Accountability
Log data provides detailed trails for auditing system performance and changes to evaluate use action within the application, which is crucial for regulatory compliance and accountability purposes. Audit log management is essential because it enables teams to:
- Meet compliance regulations and requirements.
- Make a distinction between user and system problems.
- Help reconstruct fraudulent activity.
- Show weaknesses in security for future improvement.
- Provide proof of actions in legal proceedings.
Audit logs typically record login and logout actions and details when and how someone manipulates data within a system and who they are. It allows organizations to leverage mechanisms to improve security and limit damage when incidents occur. Here’s an example:
2023-06-30T12:34:56Z INFO User 'admin' changed configuration settings from IP:192.168.1.32023-06-30T12:35:00Z INFO Configuration change: 'max_connections' set to '500'
8. Consolidates Business Intelligence
Granular log data provides data-driven insights for strategic planning and decision-making. Companies can configure and optimize their operations and develop an effective marketing strategy by analyzing valuable insights like:
- Customer Satisfaction
- Sales Transactions
- Other Business-Related Activities
Here’s an example of a business intelligence log, and below is a table representing the metrics used.
2023-06-30T12:34:56Z INFO Sales transaction completed: OrderID '98765'Amount: $150.00, UserID: '12345'2023-06-30T12:35:05Z INFO User '12345' left a product review: 'Great product!', Rating: 5 stars
| Metric | Description |
| Sales Transactions | Number of completed sales |
| Revenue | Total revenue generated |
| Customer Retention | Rate of returning customers |
The following section discusses the best practices for using log data in the following section to leverage its potential fully.
Best Practices for Utilizing Log Data
In today’s fast-paced digital landscape, maximizing the effectiveness of your logging efforts and utilizing log data is crucial. Log data use requires adherence to best practices to ensure secure and reliable information.
Read on and learn the best practices for harnessing the power of log data in the following section.
Choosing the Right Logging Level
Selecting the appropriate logging levels for different types of messages is invaluable to IT teams looking to search, filter, alert, and troubleshoot applications. These levels make key events easily identifiable so IT and DevOps teams can detect, investigate, and take action efficiently.
The typical log levels and how they’re typically used include:
- INFO: Informative logs without any real concern behind them
- ERROR: Errors affecting a specific operation
- WARN: Abnormal situations indicating potential problems
- CRITICAL: Indicating a problem that cannot continue operating normally
- FATAL: Severe issue significantly affecting the entire program
Implementing a Centralized Logging System
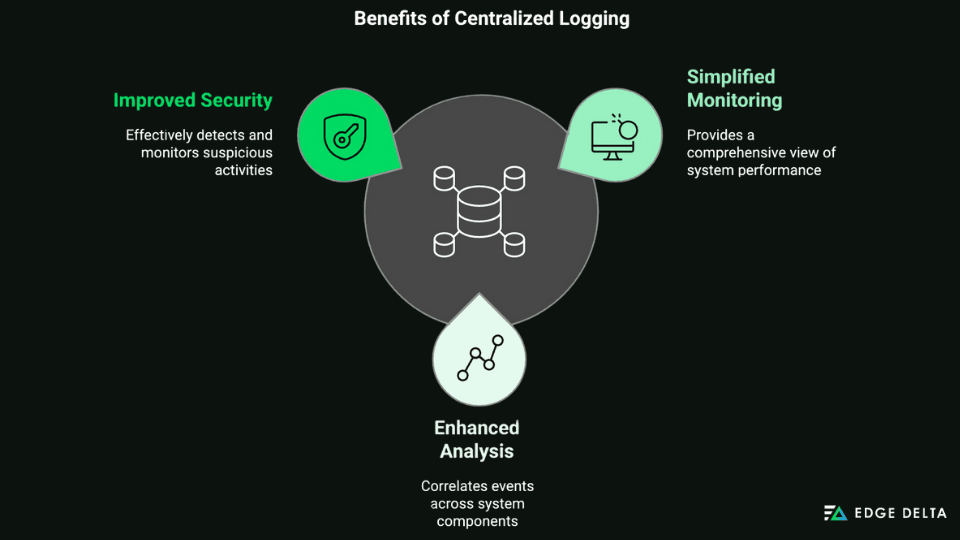
A centralized logging system is adequate for aggregating logs from diverse sources into a single repository. This approach facilitates easier management, analysis, standardization, and parsing of JSON logs and other data processing. The benefits of centralized logging include:
- Simplified Monitoring: Provides a holistic view of the system performance
- Enhanced Analysis: Correlates events across different components of the system
- Improved Security: Monitors and detects suspicious activities effectively
By funneling all logs into a centralized log management system, organizations can effortlessly search, analyze, and correlate log data, making identifying and resolving issues easier. Popular tools for centralized logging include the ELK Stack – Elasticsearch, Logstash, and Kibana.
Regularly Analyzing Log Data
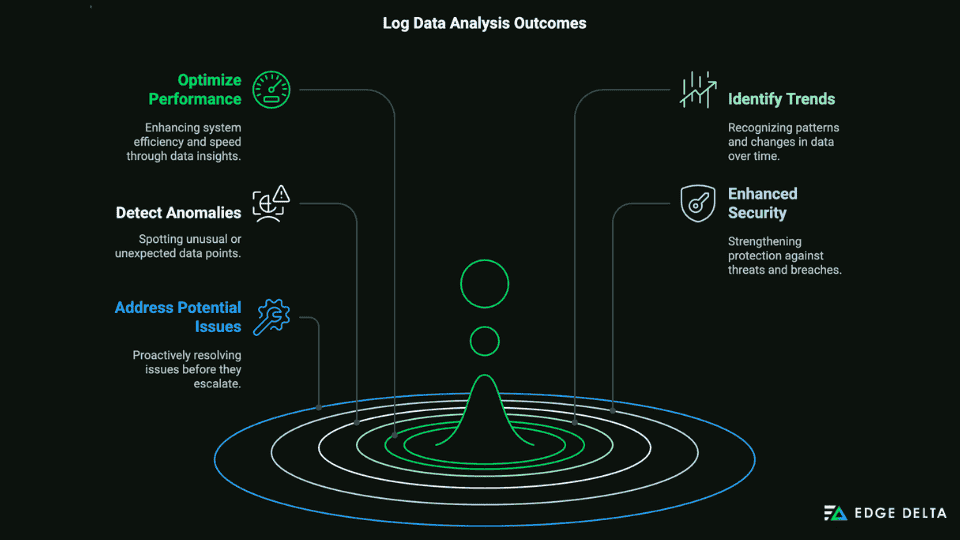
Regularly analyzing log data is essential for ongoing improvements and proactive issue resolution. It provides real-time monitoring and enables IT and DevOps to be notified of problems like threats or unauthorized activity that would otherwise be difficult to identify.
By regularly analyzing and examining log data, teams can:
- Optimize Performance
- Identify Trends
- Detect Anomalies
- Enhanced Security
- Address Potential Issues
Monitoring, analyzing, and having visibility in log data can empower developers and administrators to analyze log events as users interact with their applications or systems.
Automating Log Data Processing
Automation can help organizations collect, analyze, store, and process large volumes of logs more effectively and securely. Automation enables organizations to dynamically allocate storage resources based on demand, ensuring optimal performance and resource utilization, saving costs, and reducing stress.
The processes involved in automating log data include:
- Log Parsing: Extracting relevant data from parsing low log events or entries
- Alerting: Setting up automated alerts for log patterns and anomalies
- Reporting: Generating a detailed report that summarizes the log data information
Standard automation tools for log data analysis include Datadog, Splunk, Elastic, Edge Delta, and more. These tools streamline log data processing and reduce human error and manual effort.
Ensuring Log Data Security
Log data should be kept where security protocols are strictly implemented. Otherwise, they can cause data breaches or be the source of accidental data leaks.
| Pro Tip Leveraging security event logs to uncover data related to security can strengthen your system’s protection against leaks and breaches. With this data, you can check every login attempt, system modification, and security policy infraction. These logs provide insights to understand a system’s security comprehensively. |
It is essential to implement the following practices to secure logs and enhance data security:
| Measure | Description |
| Encryption | Encrypting log data in transit and at rest |
| Access Controls | Restricting access to log data |
| Monitoring | Monitoring access to log data |
| Tokenize | Concealing sensitive information in logs |
| Exclude Data from Code | Isolating sensitive data from code |
| Redact and Mask Data | Hiding or removing sensitive information |
By implementing these best practices, teams can significantly reduce risk and ensure log data security.
Wrap Up
Log data is a beneficial tool for IT and DevOps professionals. It offers valuable insights into system health, performance, and security events and many significant benefits. These benefits include enhanced troubleshooting and debugging, performance monitoring, security and compliance, and more, which are crucial for every system’s operation.
By understanding the best practices for utilizing log data and methods for securing it, such as data encryption, access control, and tokenization, organizations can efficiently evaluate and make informed decisions to optimize system health and performance.
FAQs on Log Data Benefits
What are the benefits of log data?
Log data’s benefits include helping teams optimize root cause analysis, reduce MTTA, better understand application usage, and enhance troubleshooting.
What are the advantages of log files?
Log files offer a detailed and easily accessible record of a system that provides information about the system performance and compliance of your applications.
Why is data log important?
A data log is essential because it provides valuable information and captures every system interaction, event, and anomaly.
Sources: