Logs are computer files that record the history of events and activities performed by a system or application. With this information, IT teams can gain insights into a system’s condition and performance. Thus, logs provide crucial data for monitoring system performance, troubleshooting issues, debugging system components, auditing, and much more.
Since logs can come from a wide variety of system components and sources, they differ in type, format, and structure, which makes log management challenging and complex. By understanding every log type and format, teams can implement proper troubleshooting, performance tuning, and security monitoring to keep their infrastructure components running smoothly. Thus, it’s crucial to understand all log types and formats to ensure effective log management.
Want Faster, Safer, More Actionable Root Cause Analysis?
With Edge Delta’s out-of-the-box AI agent for SRE, teams get clearer context on the alerts that matter and more confidence in the overall health and performance of their apps.
Learn MoreThis article discusses several of the most popular log types and formats, including examples, importance, and best practices, to ensure effective log management and analysis.
| Key Takeaways • Logs are historical records of a system or application. Since these files come from several components, they differ in format and structure. • The most common types of logs are system, application, and security logs. Each type provides specific information that helps understand a system or application’s condition. • Log formats include plain text, structured, binary, syslog, CLF, and ELF. When interpreting logs, it’s crucial to transform them into one format to ensure accurate insights. • Tools like Edge Delta’s Telemetry Pipelines are perfect for log format normalization, as they automatically convert incoming log data into the OpenTelemetry schema. • Understanding log types and formats helps improve troubleshooting, enhance system security, ensure compliance and auditing, and improve performance monitoring. • Implementing the best practices for log management can ensure effectiveness and accuracy. This involves centralization, security, consistency, rotation, retention, automation, and improvement. |
Understanding Logs in IT Systems
Logs are one of the three pillars of observability. They are frequently used in the IT world by operations teams, analysts, DevOps, and SRE Teams, and they store key information and metadata about events that occur within systems, workflows, components, and more. For instance, software applications and systems like web servers produce logs for traffic, network, login, authentication success, and more. Logs allow you to see what applications and systems are doing and how users engage with them.
Three of the core components of logs are as follows:
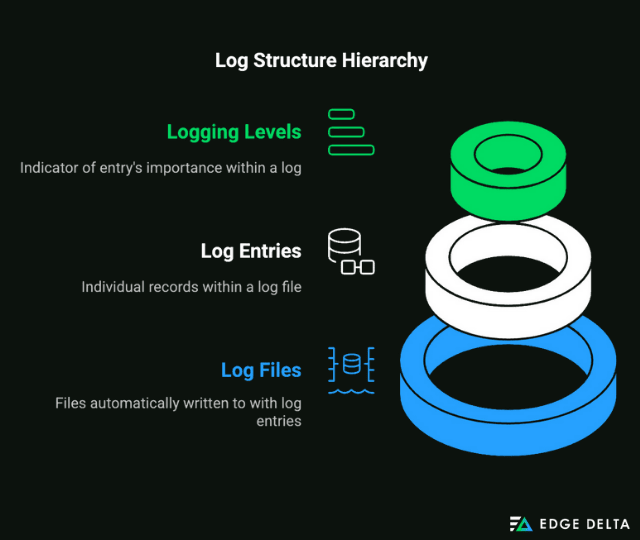
- Log Entries: Individual records within a log file.
- Log Files: Files which are automatically written to with log entries.
- Logging Levels: Indicator of the importance of an entry within a log.
Here’s a quick view of the different log types and formats with examples:
| Log Type | Description | Common Contents |
| System Logs | System-level events and errors | • Kernel logs • Authentication Logs • Security Logs |
| Application Logs | Logs generated by applications | • Contextual Information • Timestamps • Log Levels |
| Security Logs | Logs tracking security events | • Authentication logs • Access logs • Intrusion detection |
| Audit Logs | Logs used for compliance and forensic analysis | • User actions • Data access events • System changes |
| Event Logs | Logs tracking significant system, security, and application events | • System events • Application-specific events |
Types of Logs
Several log types exist to support the needs of diverse applications and industries that require logging for various purposes. Each purpose may necessitate different types of logs tailored to their specific needs.
| Fun Fact! Logging is sometimes confused with tracing, but they have different goals. Tracing refers to the set of interactions between system components taken to accomplish a task, while logging records details describing a particular event. |
The most common log types are system, application, security, audit, and event logs. Here’s an in-depth overview of each one:
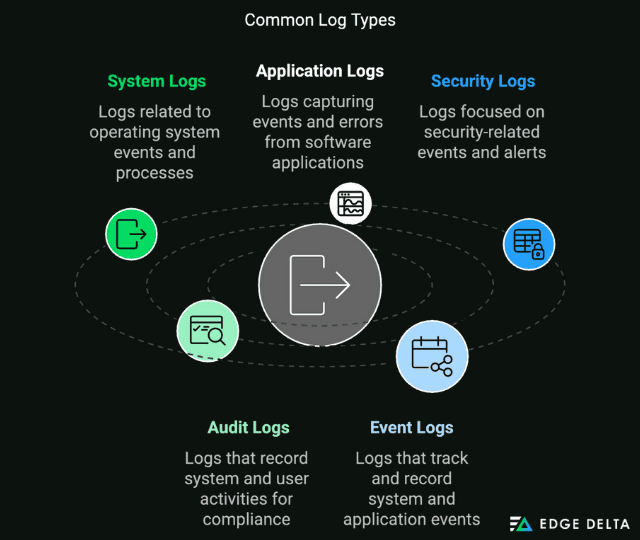
System Logs
System logs contain events related to your operating system, hardware, and other system components. These logs determine whether processes and drivers are loaded successfully.
There are three main types of system logs:
- Kernel Logs: A kernel is part of the operating system that deals directly with a computer’s RAM. Kernel logs detail each event the kernel completes, and help with system auditing, troubleshooting startup, and hardware concerns.
- Authentication Logs: These logs provide information about the authentication status of users who attempted to access a system.
- Security Logs: Logs which track events related to the safety of a system, including potential security breaches.
Application Logs
Businesses need to run various applications to perform certain functions. Events in an app’s lifecycle are recorded as application logs, which help track behavior.
Developers determine what goes into an application log file. They control which events and information are helpful and how they are executed.
However, application log messages usually contain the following information:
- Context information: Information about the application’s state at the time of the message.
- Log levels: Labels for calculating the level of importance of entries in a log file (info, warn, error, etc).
- Timestamps: Time at which the event occurred.
Security Logs
Security logs refer to system security events, such as user authentication, access control, and intrusion detection. They can be found in security software, databases, and applications.
Here are examples of security log sources:
- Antivirus program
- Firewall
- Intrusion detection/prevention system
- Vulnerability management
- Authentication server
- Router
| Note: Security logs may contain PII or personally identifiable information on users of information resources. |
Through security logs, you can monitor and examine the security posture of your system.
Here are security log examples:
- Authentication Logs show information about user authentication. This log type includes data on login attempts and whether they were successful or not.
- Access Logs contain information on access requests.
- Intrusion Detection Logs involve firewall activities, including allowed and blocked connections, intrusion attempts, and traffic patterns. This log type includes alerts to detect anomalies and potential cyberattacks at the intrusion stage.
- Intrusion Detection/Prevention System (IDPS) Logs are alerts and events generated by IDPS sensors, indicating potential malicious activities or policy violations.
Audit Logs
These logs are also called audit trails or audit history. They aim to record activities and transactions for security, compliance, and troubleshooting.
| Note: Audit logs were traditionally utilized for compliance and audit purposes. However, rising cyber threats have prompted many to use audit logs to search for, detect, and respond to security incidents. |
Audit logs provide proof of compliance with rules and industry standards. They also help with forensic analysis. For instance, you can use the audit trail to reconstruct events after specific incidents for investigation.
Audit logs usually have the following content:
- User actions: When a user accesses the system or logs out.
- Data access events: When users create, modify, or delete something.
- System changes: Any changes to system settings, including configurations or preferences.
Event Logs
Event logs are high-level logs with information about significant actions and occurrences in a system or application. System events and application-specific events are the typical contents of event logs.
An event log can have some of the following details:
- Date and time of an occurrence
- Description of an event
- Source, which is the program or component that caused the event
- An event’s severity
- Processes
- Specific codes for event identification
- Others
Event logs are a core component in Microsoft Windows. They are classified into the following:
- Windows application logs
- Security logs
- System logs
- Directory service logs
- DNS server logs
- File replication service logs
Common Log Formats
Depending on the device, system, or application that generates them, logs can be generated in various structured and unstructured formats.
Most Log formats have the following specifications:
- Whether the data is in plain text or binary
- The kind of encoding the log file will use
- How records are delimited
This table provides an overview of the typical log format examples.
| Log Format | Description | Example |
| Plain Text | Simple, unstructured logs containing only actual text characters | 2024-06-25 12:58:25.357 EST INFO: LOGIN (admin): UserID=”admin”, Client=”Console”, Origin=”renzo”, SessionID=”ED1D522D-D4DD-493D-80D9-0806EB4D907D” |
| JSON | Structured, easily parsed by machines | { |
| XML | Structured, used for complex data | <logEntry> |
| Binary | Efficient, used for recording changes to databases | [Timestamp: 2024-06-24 15:31:00] [Event Type: INSERT] [Affected Table: users] [Data: Binary representation of inserted data] |
| Syslog | Standard format for Unix-like systems | <102>Jun 20 11:15:22 server-03: CPU load average: 1.5 |
| Common Log Format (CLF) | Standard format for web server logs | 127.0.0.1 – michael [19/Jul/2024:11:30:15 -0700] “GET /apache_pb.gif HTTP/1.0” 200 2326 |
| Extended Log Format (ELF) | Detailed web server logs | 10.0.0.1 – erica [20/Jul/2024:19:40:10 -0400] “GET /dashboard HTTP/1.1” 200 15824 “https://example.com/login” “Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/99.0.9999.99 Safari/537.36” “sessionID=xyz987654321; user=erica” “example.com” |
Here’s a deeper dive into these types of log formats:
Plain Text Logs
Plain text logs are characters in their simplest form, without special formatting like bold, italics, or colors. This simplicity helps ensure consistent results across different environments.
These logs act as the basis for creating and manipulating more complex formats. They are used for coding, scripting, configuration files, and data storage. You can easily read and edit plain text logs using text editors.
Structured Logs (JSON, XML)
Logs can be structured, semi-structured, or unstructured. Structured logs are readable by humans and machines because they have clear and consistent patterns.
Unlike unstructured logs, structured logs enable developers to search through events easily. They are helpful when troubleshooting an issue or discovering a concerning trend.
| Pro Tip! You can leverage observability tools Edge Delta for better log storage and searching. It offers hybrid log search and features for easy log visualization and fast troubleshooting! |
Structured logs generate logs in easily parsable formats: JSON and XML.
JSON Logs
JavaScript Object Notation (JSON) Logs are structured logs with key-value pairs. Each JSON log represents a separate object, allowing messages to be easily searched, filtered, and analyzed. Thus, almost all programming languages, even those without JSON functionality, can parse these logs. You can even nest data into different layers while keeping the format readable.
JSON logs offer the following significant advantages:
- A simple and familiar structure, ideal for most developers and machines
- Adaptable since it lets you add or remove fields with ease
- Provides rich, contextual data that facilitates observability
XML Logs
Extensible Markup Language (XML) is a text-based formatting language designed to store and transport data. It supports information exchange between websites, databases, and third-party applications.
XML logs are structured hierarchically using tags to define different elements and attributes.
XML offers the following advantages:
- Readable and understandable
- Compatible with Java and is portable
- XML is extendable; you can create your custom tags or use the tags created by others
- Stricter than JSON
- Has support for schemas and namespaces
Binary Logs
Binary logs contain events describing database changes, such as table creation operations, changes to table data, and more. These logs include events that potentially made modifications. They also indicate how long each statement took to update data.
MySQL, a popular relational database management system, uses binary logs to record database changes.
Binary logs are efficient in many ways:
- Storage: These logs store data in a compact binary format, not human-readable text, reducing the required storage space. Some database systems offer options to compress binary logs for reduced storage requirements.
- Performance: These logs are highly performant because they impose less overhead on database performance. Writing data in binary format typically requires fewer disk I/O operations.
- Restoration: Binary logs can also be used to restore data after a backup, as they store a record of all changes.
Despite its benefits, there are challenges associated with parsing binary logs:
- Events are written in a non-human-readable format.
- The structure can vary depending on the database management system.
- Binary logs include metadata with many parts that may be encoded differently, requiring careful parsing.
Syslog Format
System Logging Protocol (syslog) defines logging standards for transporting event messages between computer systems and software applications.
Syslog makes it easy to exchange log information by solving the difficulty of interpreting log messages sent by unknown applications. Syslog messages may include timestamps, event messages, host IP addresses, and more.
Syslogs are widely used in Unix-like systems by the kernel and many applications. Unix is a multiuser computer operating system. Meanwhile, syslog is the standard Unix logging mechanism.
| Note: Mid-range to high-end network devices implement syslogs as their logging mechanism. |
There are lots of syslog formats, and the original has the following structure:
<priority>timestamp hostname: message
- Priority refers to numerical values showing a message’s severity and importance. This part also represents the part of the system sending the message, also called the ‘facility.’
- Timestamp pertains to the instance when a message was generated. It goes by the month, day, hour, minute, and second format.
- Hostname is the name of the device or system that generated the log.
- Message refers to the actual log information or event description.
Here is a sample syslog message using the original format:
<102>Jun 20 11:15:22 server-03: CPU load average: 1.5 |
Here’s a breakdown of this log format example:
- Priority Value: 102
- Timestamp: June 20 11:15:22
- Hostname: server-03
- Message: CPU load average: 1.5
The new syslog format is structured this way:
timestamp hostname process[pid]: message |
Here, the meanings of the timestamp and hostname fields are identical to the old syslog format. The process and [pid] fields have information about the process that created the log.
A syslog message using the new format looks like this:
Jun 10 10:29:25 server-08 kernel[0]: CPU temperature exceeded threshold. |
In this example, a syslog message on June 10 at 10 am informs about a critical event. It is related to the CPU temperature logged by the kernel process on server-08.
Common Log Format (CLF)
Most web servers produce a log file in the CLF format for every HTTP request. This text-based log format is standardized and non-customizable.
Various log analysis programs can read the CLF. The format is as follows:
%h %l %u %t \"%r\" %>s %b |
Log file entries produced in CLF look like this:
127.0.0.1 - michael [19/Jul/2024:11:30:15 -0700] "GET /apache_pb.gif HTTP/1.0" 200 2326 |
- 127.0.0.1 (%h) – refers to the IP address of the client, which is the remote host who requested the server
- – (%l) – the hyphen indicates that the server did not require authentication
- Michael (%u) – username of the authenticated user as determined by HTTP authentication
- [19/Jul/2024:11:30:15 -0700] (%t) – date and time of the request. The time that the request was received. It goes by day, month, year, hour, minute, second, zone.
- GET /apache_pb.gif HTTP/1.0 (\”%r\”) – request line from the client including the HTTP method, requested source, and HTTP protocol version
- 200 (%>s) – status code that the server sends back to the client, indicating the success/failure of the request. Here, 200 means OK.
- 2326 (%b) – the size of the object returned to the client as part of the server’s response
Extended Log Format (ELF)
The Extended Log Format (ELF) is more flexible and contains more information on web server transactions than CLF. Web servers like Apache HTTP Server and Nginx use ELF.
ELF allows you to include the fields you want while limiting log file sizes by omitting unwanted fields. Some additional fields in the ELF are start/end date/version/field data/software information.
Here’s an ELF example:
10.0.0.1 - erica [20/Jul/2024:19:40:10 -0400] "GET /dashboard HTTP/1.1" 200 15824 "https://example.com/login" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/99.0.9999.99 Safari/537.36" "sessionID=xyz987654321; user=erica" "example.com" |
- 10.0.0.1 – remote host
- Erica – user ID
- [20/Jul/2024:19:40:10 -0400] – date and time
- GET /dashboard HTTP/1.1 – request line
- 200 – status code (OK)
- 15824 – bytes sent
- https://example.com/login – referrer
- Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/99.0.9999.99 Safari/537.36 – user agent
- sessionID=xyz987654321; user=erica – cookies
- example.com – virtual host
Importance of Log Types and Formats
Many types of log files and formats exist because of diverse systems and application-specific needs. They help with consistent log data representation for better interpretation and analysis.
Specifically, log types and formats assist with the proper parsing and extraction of relevant information to support your observability efforts.
| Helpful Article! Log parsing, or organizing entries into fields, can be challenging because of its volume, velocity, and variety. Thus, it’s crucial to understand and implement the best practices for effective log parsing. |
Discover how you can benefit from the many log types and formats below.
Effective Troubleshooting
Understanding log types and formats lets you pinpoint where issues occur, enabling you to conduct effective troubleshooting and root-cause analysis. For instance, application logs may reflect bugs or failures in specific software components, while system logs can indicate hardware or operating system warnings. Integrating different logs into your observability workflows can help give you end-to-end visibility over your environment.
Enhanced Security
Logs enhance security by providing a detailed record of information that could impact the security of your IT environment. It is much easier to investigate problems when you have access to time-stamped records of activities. For instance, audit logs can identify and track successful and unsuccessful login attempts. This data enables security threat detection and response, if too many unsuccessful login attempts are logged.
Additionally, security logs provide information about security events like authentication failures, access control violations, and errors. These interactions and activities can be used to examine an application’s security posture.
Compliance and Auditing
Some environments require compliance with standards like SOX, HIPAA, and GDPR. Log types and structures make consistent log data representation required in these environments. Log management ensures that logs are audited effectively to meet such requirements. Securely storing logs makes them accessible for auditing purposes.
Performance Monitoring
Logs contain performance metrics to help monitor the health and performance of systems and applications. Here are some performance-related metrics that can be derived from logs:
- CPU utilization
- Memory usage
- Disk I/O
- Response times
- Throughput
- Error rates
These performance logs provide data on resource usage. Use them to predict when you’ll need additional resources and support your growing needs.
Assessing logs’ historical performance also establishes baseline performance metrics. It enables developers to track deviations from typical performance, allowing you to identify opportunities for optimization.
Best Practices for Log Management
Proper log file monitoring and analysis enable observability on your IT infrastructures’ extensive network. They help create transparency and allow visibility into the cloud computing environment that powers your key business services. There are many activities to enable proper log management, such as centralized logging and automated alerting.
Dive into the specifics of how to perform better log management below.
Centralized Logging
Centralized logging is roughly defined as collecting logs from distributed systems and centralizing them in one location to store and analyze. These sources could be any collection of networks, infrastructures, or applications.
This technique gives a consolidated view of all activities, making spotting and troubleshooting issues more manageable. Tools like Edge Delta’s Telemetry Pipelines enable teams to do exactly that, by giving them full control over their data.
Many tools facilitate centralized logging, such as Splunk and the ELK stack. Splunk is a centralized log management tool, while the ELK stack is a set of open-source projects:
- Elasticsearch
- Logstash
- Kibana
| Pro Tip! Implement a centralized logging approach to ensure you do not lose log data if one node is compromised. |
Security and Privacy
Log types and formats in cyber security contain sensitive data that anyone with access can easily read. Thus, hackers can access and alter sensitive data without proper integrity and confidentiality measures.
Hackers are always waiting for any vulnerability to infiltrate your systems. Implementing best practices to ensure the security and privacy of log data is crucial.
Learn from the following tips:
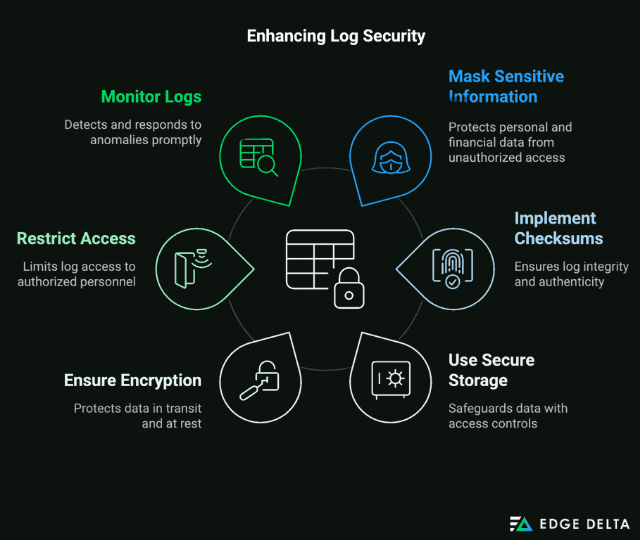
- Mask sensitive information, such as personally identifiable information and financial details. This tip mitigates insider threats by restricting how sensitive data is accessible to individuals.
- Implement checksums and cryptographic signatures for logs. They prove the identity and origin of logs and expose any alterations to assure clearance of tampering.
- Use secure storage solutions with access controls.
- Ensure encryption to log files in transit and at rest to protect from unauthorized access.
- Restrict log access to authorized individuals only.
- Monitor and audit logs regularly and proactively. Make this a habit to detect and respond to any anomaly quickly.
Consistent Log Formatting
Automated systems that process logs rely on consistent formats to accurately parse and extract information. Consistent log formatting promotes readability and interpretation because you can quickly scan through them.
This technique enables reliable automation of tasks like log aggregation, analysis, and alerting. It also enhances search capabilities and improves the ability to visualize log data.
Use a consistent format throughout your logs by arranging the same information in order. For instance, you can include the timestamp, severity level, component where the event occurred, and message in one log entry, while having them in the same order for all subsequent entries.
| Pro Tip! Establish a uniform format for your logs, like the OpenTelemetry Schema, and ensure everyone on your team is aware. This way, it can be more easily parsed and analyzed by a log analysis software. |
Log Rotation and Retention Policies
Log rotation involves regularly archiving and discarding old log files as your application generates them. This practice avoids filling up your disk space and system slowdowns.
Establishing a rotation schedule and retention policy for this technique is critical. For instance, you can rotate logs weekly and retain them for a month. This step should depend on the volume of logging on your system. You can also implement a data tiering strategy to intelligently send data to a variety of downstream destinations, depending on importance and timeframe.
You can use the following tips to balance data availability and storage constraints effectively:
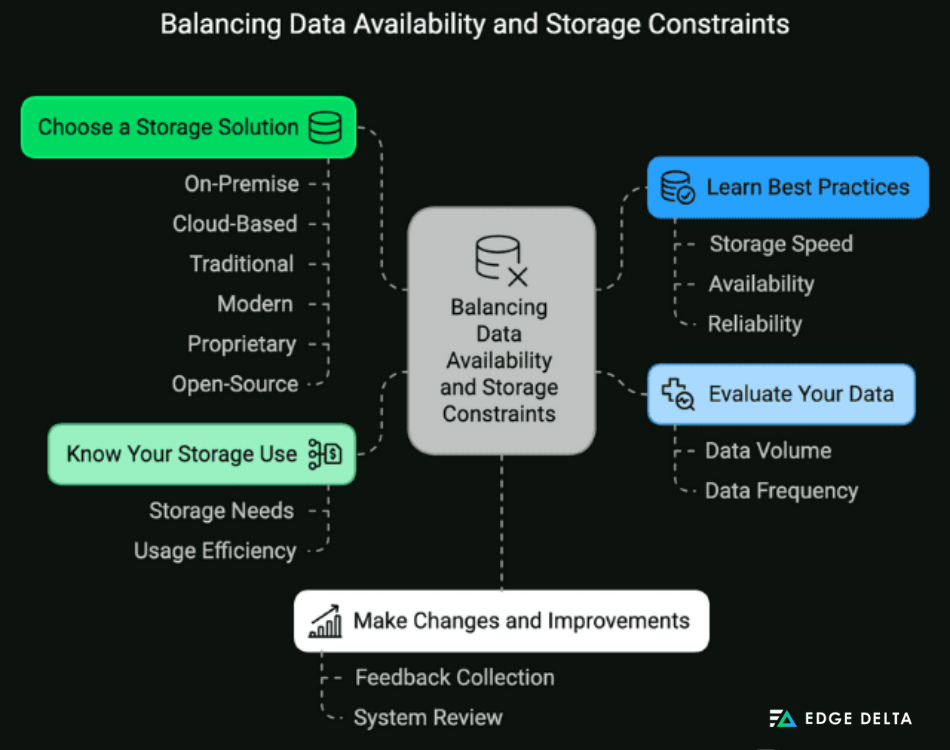
- Evaluate your data. Understand how much data you need and how often you need them.
- Choose a storage solution. You can choose between on-premise or cloud-based, traditional or modern, and proprietary or open-source storage.
- Know your storage use. Understand how much storage you need and how well you use your storage system.
- Learn the best practices for improving your data storage. This step involves understanding aspects like storage speed, availability, and reliability.
- Make changes and improvements. Use reviews and feedback to know what areas need improvement in your storage system.
Automated Alerting and Monitoring
Proper log monitoring means continuously tracking your logs. Real-time automated alerting systems play a significant role in this process. They help ensure that potential security threats are addressed promptly.
Here are some examples of where log alerts are essential:
- Suspicious activities, such as potential breaches and unauthorized access attempts
- Critical errors, exceptions, or failures
- Performance metrics falling below acceptable thresholds
- Resource utilization metrics nearing capacity limits
- Infrastructure changes like configuration updates
- Changes to security settings
- Business metrics such as customer engagement levels and sales volumes
If you haven’t set up alerts for critical events, follow these steps:
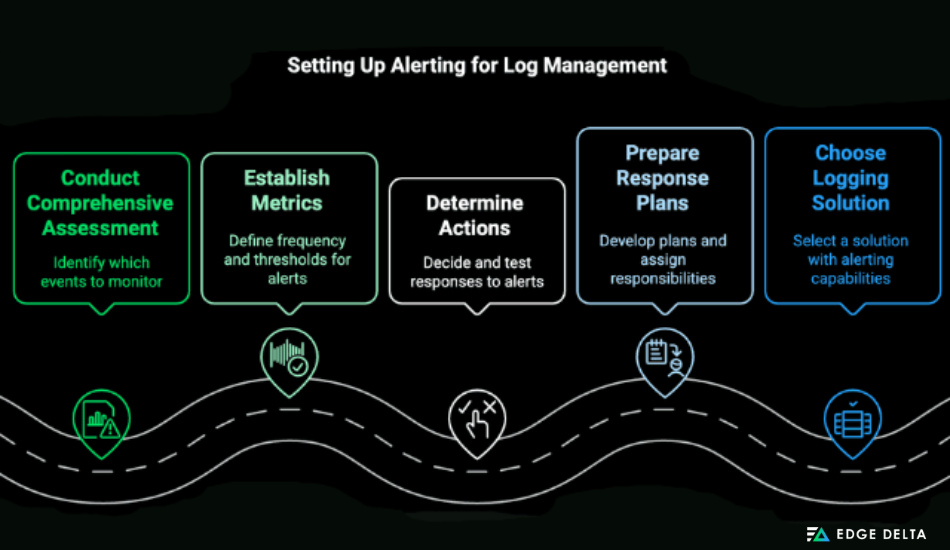
- Conduct a comprehensive assessment of which events you want to monitor, such as system errors.
- Establish metrics like the frequency of your checks and thresholds that define when an event should trigger an alert.
- Determine the actions you wish to do in response to an alert and test them.
- Prepare response plans for different alert types, assigning who is in charge and determining what actions should be taken.
- Choose a logging solution that supports alerting capabilities like the ELK stack.
Continuous Improvement
Log utilization can evolve significantly over time due to technological advancements, increased data volumes, etc. This implies the need for continuous improvement in log management.
| Helpful Article! Managing high-volume logs is time-consuming, complicated, and expensive. Thus, it’s crucial to understand several tips to ensure effective high-volume log management. |
Regularly reviewing and updating logging configurations can create an environment of continuous improvement for log management. This practice ensures that your logging system remains effective and aligned with your needs.
Here are some ways to review and update logging configurations:
- Review your existing logging configurations and understand their current requirements. Then, document any changes made, including the rationale behind each change.
- Identify your stakeholders who depend on logging data and get their feedback and requirements for logging.
- Assess your system’s logging levels, such as warning and error, and determine if they are at normal levels.
- Thoroughly test updated logging configurations in a test environment before deployment. This way, you can verify that logs are correctly captured and alerts are triggered appropriately.
Conclusion
Logs help maintain operational efficiency, security, and compliance. Each log type and format plays a key part in monitoring, troubleshooting, auditing, and analyzing activities. Thus, learning the best practices for log management is critical to making the most of logs. Centralized logging is the number one method for ensuring a log’s security and privacy.
Log files provide a record of activities and changes in your system or application, so you must learn how to manage them effectively. You can improve your log management with tools like Edge Delta. It normalizes data upon creation to help you track and maintain your system and application health.
FAQs on Log Types and Formats
How many types of logs are there?
Common log types include system, application, security, audit, and event logs. The exact number of logs that exist is unknown. There are also error logs, access logs, debug logs, database logs, network logs, and much more.
What is the best format for logs?
JSON logs are the de facto standard for structured logging because tools can quickly parse it. However, there is no “best” format – it all depends on your needs and requirements.
Is syslog and SIEM the same?
No. Syslogs are standard protocol computer systems transporting logs for centralized logging and monitoring systems/apps. Meanwhile, SIEMs have all of the features of log management systems, but with a focus on security.
Sources:








